Watching Common Lookalike Domains Using Infoblox Portal (1534)
Scenario
Your organization’s security team has detected suspicious activity involving the frequently used domain PayPal.com, raising concerns about phishing attempts and the use of lookalike domains to target employees. As a security analyst, you are tasked with proactively monitoring and investigating these lookalike domains to help prevent potential cyber threats. This involves enabling domain monitoring for PayPal.com, reviewing recent activity associated with lookalike domains, and exporting relevant data for in a report for deeper analysis.
Estimated Completion Time
10 to 15 minutes
Prerequisites
Access to the Infoblox Portal
Knowledge of lookalike domains and threat reports
Tasks
Enabling Monitoring for PayPal.com
Analyzing Lookalike Domain Data for PayPal.com
Exporting and Reviewing Lookalike Domain Data
Task 1: Enabling Monitoring for PayPal.com
Use the Education Infoblox Portal credentials to log in to the Infoblox Portal. Use the Lookalike Common Watched Domains list to enable monitoring for the domain PayPal.com.
Task 2: Analyzing Lookalike Domain Data for PayPal.com
Use the Lookalike Report to investigate recent lookalike domain acitivity associated with PayPal.com.
Task 3: Exporting and Reviewing Lookalike Domain Data
Export your findings into and highlight any suspicious lookalike domains for futher analysis.
Solutions
Task 1 Solution: Enabling Monitoring for PayPal.com
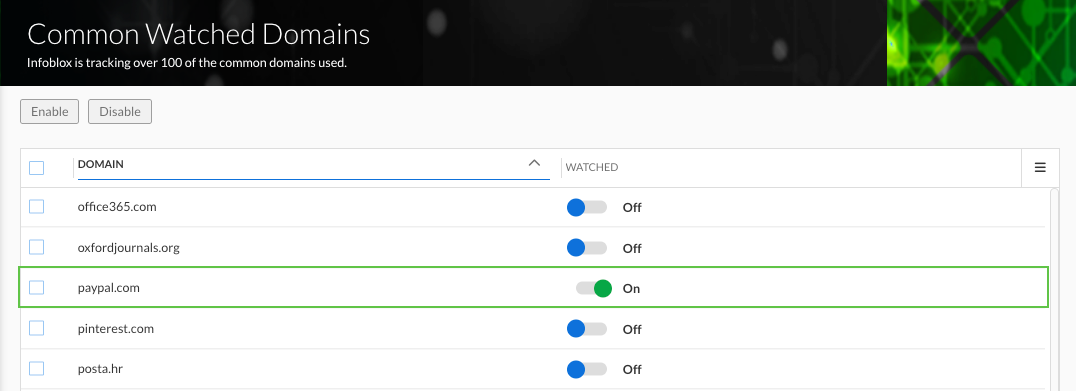
In this task, we will use the Common Watched Domains list on the Infoblox Portal and toggle monitoring for PayPal.com on. This enables Threat Defense to investigate lookalike domain acitivty associated with the domain.
Log in to your lab’s jump-desktop.
Use your Education Infoblox Portal Credentials to log into the Infoblox Portal.
Navigate to Monitor > Reports > Security > Lookalike Domains > Common Watched Domains.
Scroll down until you locate PayPal.com in the list.
Toggle the switch next to PayPal.com to enable monitoring.
Ensure the switch is turned to the ON position.
Task 2 Solution: Analyzing Lookalike Domain Data for PayPal.com
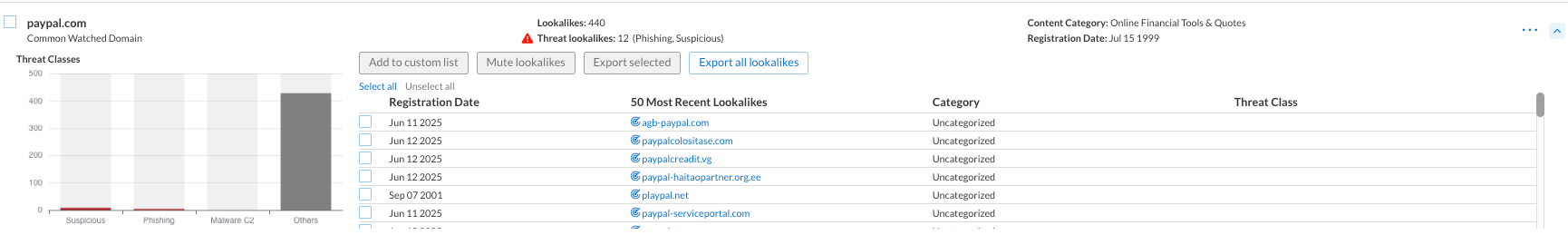
In this task, we will investigate lookalike domain activity for PayPal.com avaiable for us under the lookalike actitivty report.
Navigate to Monitor > Reports > Security > Lookalike Domains > Activity.
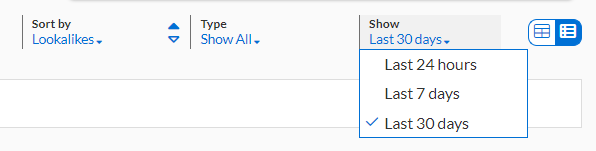
Set the Show filter to Last 30 Days by selecting it from the dropdown menu.
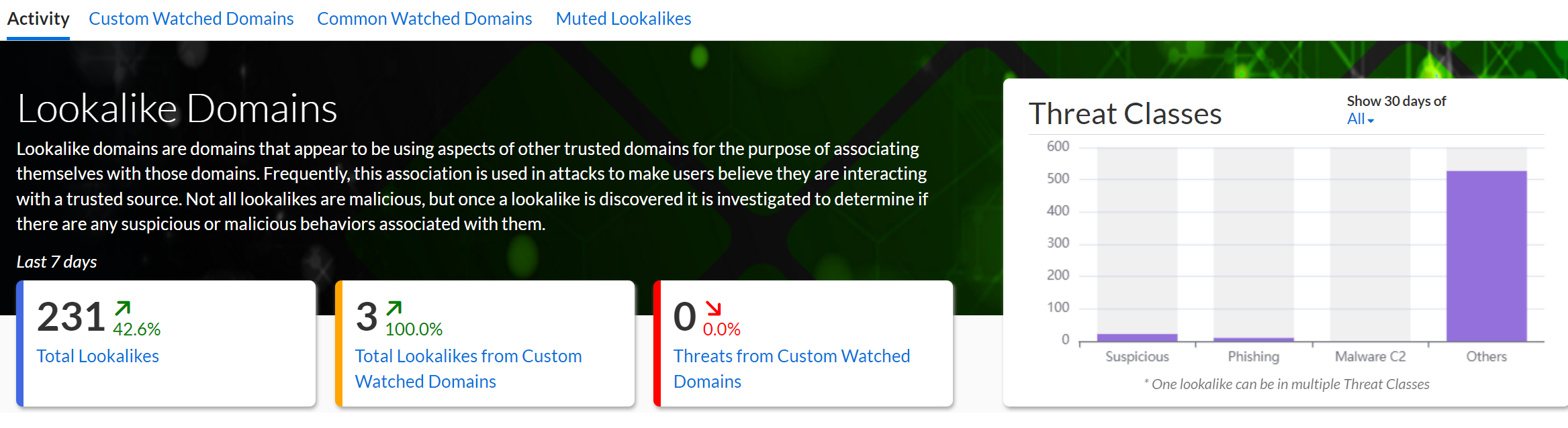
Review the following sections in the Activity page:
Total Lookalikes: Displays the total number of lookalike domains detected in the last 30 days.
Threat Classes: Shows the distribution of threat classes, such as suspicious activity, phishing, malware C2, or others.
Search for
paypal.comin the search bar.From the search results, expand the PayPal.com entry by clicking the arrow pointing downward.
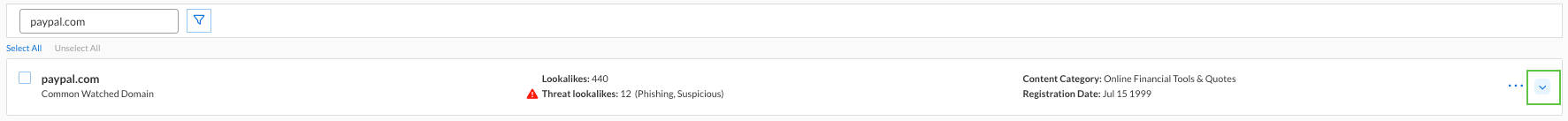
Review the detailed information displayed, including:
Registration Date
50 Most Recent Lookalikes
Category
Threat Class
Examine the Threat Classes chart to assess suspicious, phishing, and malware activity.
Task 3 Solution: Exporting and Reviewing Lookalike Domain Data
In this task, we will Export all our findings into a CSV file. We will review exported data and highlight any lookalike domain under the suspicious or phishing threat classes for further analysis.
With the PayPal.com entry expanded, click on Export All Lookalikes.
Open the downloaded file using a spreadsheet application.
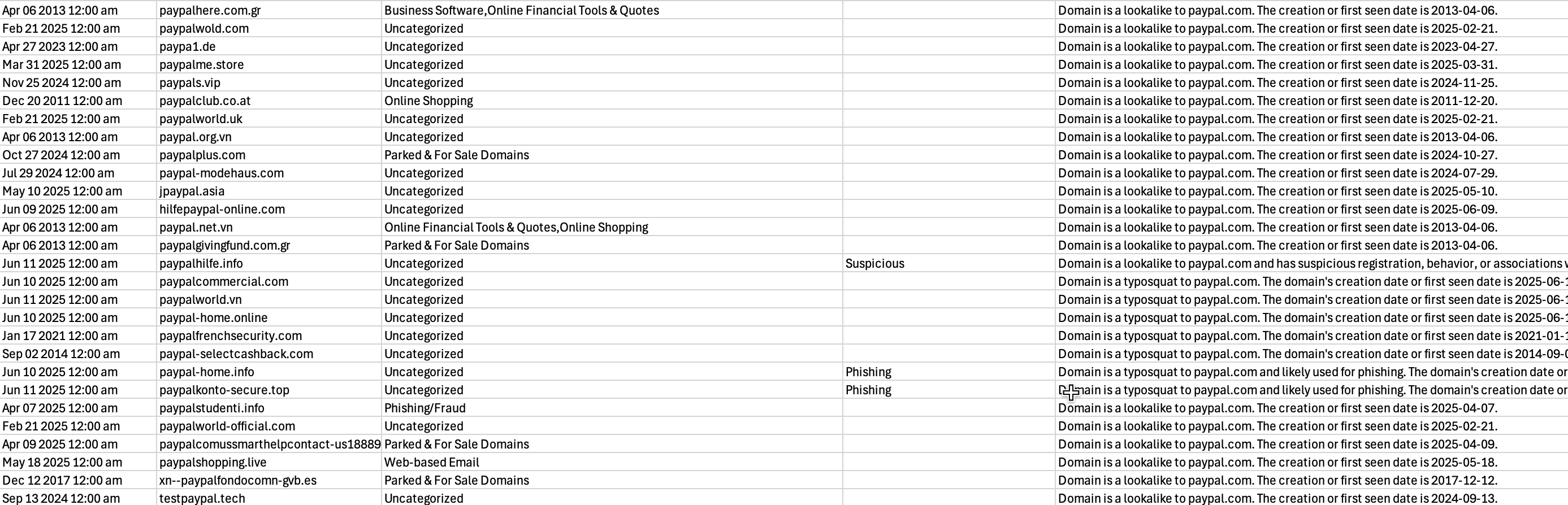
Review the key columns in the file
Registration Date: When the lookalike domain was registered.
50 Most Recent Lookalikes: Details on the most recent lookalike domains.
Category: Classification of the domain’s activity.
Threat Class: Threat types associated with the domain.
Explanation: Provides additional context or details about the lookalike domain.
Look through the Threat Class column to identify a few domains that fall under Suspicious or Phishing categories.
