Recognizing DNSSEC-signed domains (1601)
Scenario
Your organization has recently adopted DNSSEC, a valuable security measure that aligns with the latest recommendations for DNS security. As part of your responsibilities, you have been assigned the task of testing the resolution of your organization's DNSSEC-enabled zones, ensuring they can be accessed by the public while being properly signed.
To refresh your DNSSEC knowledge, you decided to validate a selection of public domains. These domains include some that are DNSSEC signed and others that are not.
Estimate Completion Time
15 to 20 Minutes
Course References
0301: Information Security Fundamentals
1204: DNSSEC Fundamentals
Learning Content
Tasks
Task 1: Recognize Signed Domains
In this task, we determine whether or not a particular domain name has been signed by DNSSEC, through querying for the SOA record of the domain and requesting additional DNSSEC information manually.
Using the name server 8.8.8.8, determine which of the following domain names have been signed
Domain Name
Status
www.fbi.gov
www.yahoo.com
www.infoblox.com
www.ietf.org
www.hawaii.edu
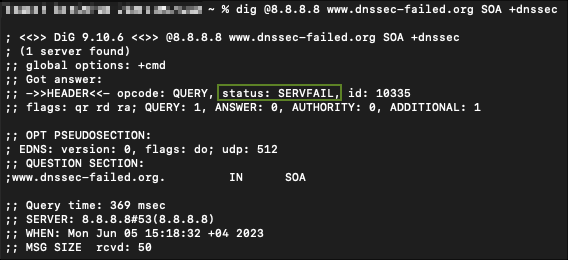
www.dnssec-failed.org
Which, if any, of the secure domains is bogus?
Solutions
Task 1: Recognize Signed Domains
Using dig with the name server 8.8.8.8, we determined that
Domain Name
Status
Reason
www.fbi.gov
secure
DNSSEC is implemented properly
www.yahoo.com
insecure
DNSSEC is not implemented at all
www.infoblox.com
insecure
DNSSEC is enabled on infoblox.com but not it's alias
www.ietf.org
secure
DNSSEC is implemented properly
www.hawaii.edu
insecure
DNSSEC is not implemented at all
www.dnssec-failed.org
bogus
We cannot be sure just by doing this step
You can follow the following syntax to validate each of the entries in the table:
dig @8.8.8.8 [domain-name] SOA +dnssec +multi
www.dnssec-failed.org is bogus and we can validate that by the SERVFAIL error response message.