Allowing and restricting DNS queries in NIOS (2519)
Scenario
Your team decided to apply different security policies to two Grid members serving DNS. The first DNS member will accept queries from any client, the second member will only accept queries originating from internal address space. Please make the necessary configuration changes in the Grid.
Estimate Completion Time
20 to 25 minutes
Credentials
Description | Username | Password | URL or IP |
|---|---|---|---|
Grid Manager UI | admin | infoblox |
Requirements
Administrative DNS access to the Grid
Which networks can perform DNS queries (connect on port 53)
Learning Content
Lab Initiation
Access jump-desktop
Once the lab is deployed, you can access the virtual machines required to complete this lab activity. To initiate the lab, click on the jump-desktop tile and login to the Linux UI:
Username: training
Password: infoblox
Initiate lab
To initiate the lab, double-click the Launch Lab icon on the Desktop.

Launch Lab
Choose the lab number from the list and click OK.
After clicking OK, you will see a pop-up message with a brief description of the lab task. If the description looks correct, click Yes to continue lab initiation.
Lab initiation will take a couple of minutes to finish.
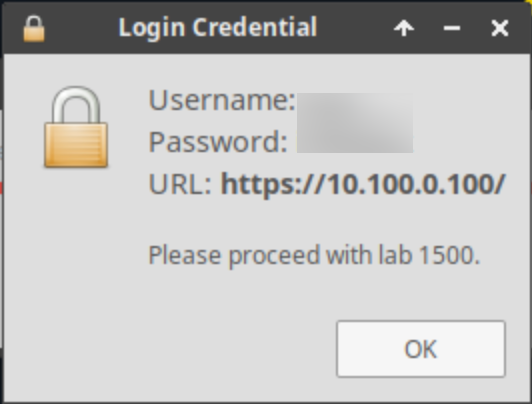
Once complete, you will see another pop-up message with the login credentials and the URL for the Grid Manager’s User Interface. Note that the credentials may differ from those from prior labs.
Tasks
Task 1: Allowing DNS queries on a member
The Grid member ibns1.techblue.net needs to accept DNS connections from any client. Please configure it as such.
Task 2: Restricting DNS queries on a member
The Grid member ibns2.techblue.net should only accept DNS connections from clients originating from the 10.100.0.0/16 network. Please configure it as such.
Task 3: Restarting Grid services
You should have been prompted to restart Grid services after making these changes. If not, please manually restart Grid services.
Solutions
Task 1 Solution: Allowing DNS queries on a member
DNS Access Control can be applied at any level of the DNS hierarchy. In this lab, we will be applying it on members.
Navigate to Data Management → DNS → Members
Check the box next to ibns1.techblue.net and click Edit
In the Member DNS Properties window, click on Queries tab
Click Override in the Allow queries from section
Choose Set of ACEs radio button and click Add
 dropdown
dropdownSelect Any Address/Network and click Save & Close
Task 2 Solution: Restricting DNS queries on a member
For ibns2.techblue.net we will allow one network and deny all others
Navigate to Data Management → DNS → Members
Check the box next to ibns2.techblue.net and click Edit
In the Member DNS Properties window, click on Queries tab
Click Override in the Allow queries from section
Choose Set of ACEs radio button and click Add
 dropdown
dropdownSelect IPv4 Network
Use the slider to set Netmask as /16
In the Address box, type in 10.100.0.0 and click Add
Click Save & Close
Task 3 Solution: Restarting Grid services
Changes made to DNS configuration will only take effect after a service restart on all members that were involved.
Restart the Service when prompted by clicking Restart in the banner
In the Restart Grid Services window, click Restart
Alternatively, we can also restart services from the Members menu by navigating to Grid → Grid Manager → Members or Data Management → DNS → Members
From the Toolbar on the right, click Restart Services
Select the radio button for Force restart services
Click Restart
