Limiting Recursion with Named ACLs (2605)
Scenario
Your team decided to apply different security policies to your Grid members serving DNS. members will only accept queries originating from internal address space using named ACLs. Please make the necessary configuration changes in the Grid.
Estimate Completion Time
20 to 25 minutes
Credentials
Description | Username | Password | URL or IP |
|---|---|---|---|
Grid Manager UI | admin | infoblox |
Requirements
Administrative DNS access to the Grid
Which networks can perform DNS queries (connect on port 53)
Learning Content
Lab Initiation
Access jump-desktop
Once the lab is deployed, you can access the virtual machines required to complete this lab activity. To initiate the lab, click on the jump-desktop tile and login to the Linux UI:
Username: training
Password: infoblox
Initiate lab
To initiate the lab, double-click the Launch Lab icon on the Desktop.

Launch Lab
Choose the lab number from the list and click OK.
After clicking OK, you will see a pop-up message with a brief description of the lab task. If the description looks correct, click Yes to continue lab initiation.
Lab initiation will take a couple of minutes to finish.
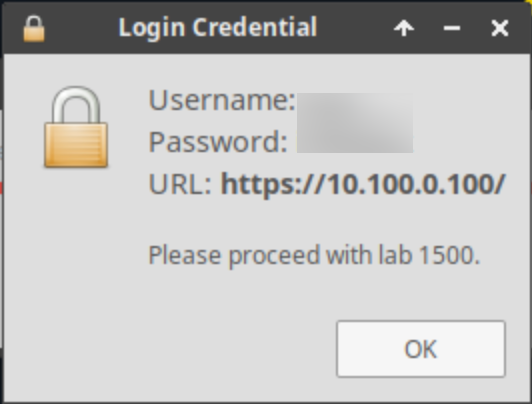
Once complete, you will see another pop-up message with the login credentials and the URL for the Grid Manager’s User Interface. Note that the credentials may differ from those from prior labs.
Tasks
Task 1: Named ACL and Limit Recursion
In this task, you will update the Grid DNS settings to protect against two attacks targeted at recursive servers.
Login to the Grid Master IBGM (10.100.0.100):
Navigate to Administration → Named ACLs
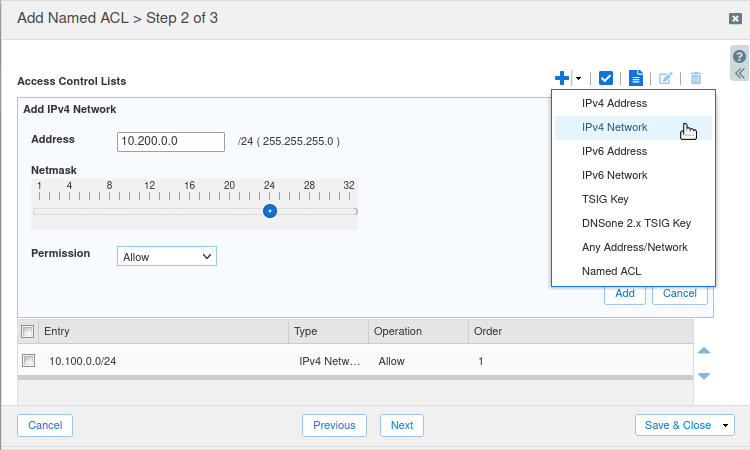
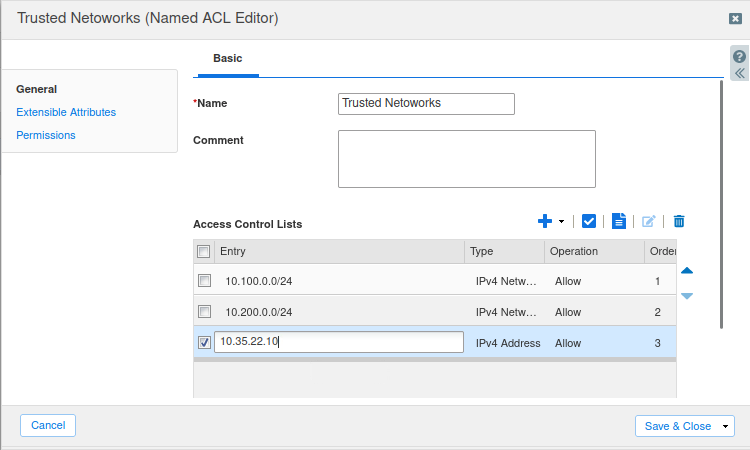
Create a new ACL with the name Trusted Networks
Add the two networks 10.100.0.0/24 and 10.200.0.0/24 and the host Jump-Desktop(10.35.22.10) to the list, then Save & Close.
Navigate to Data Managment → DNS
On the Toolbar click on Grid DNS Properties
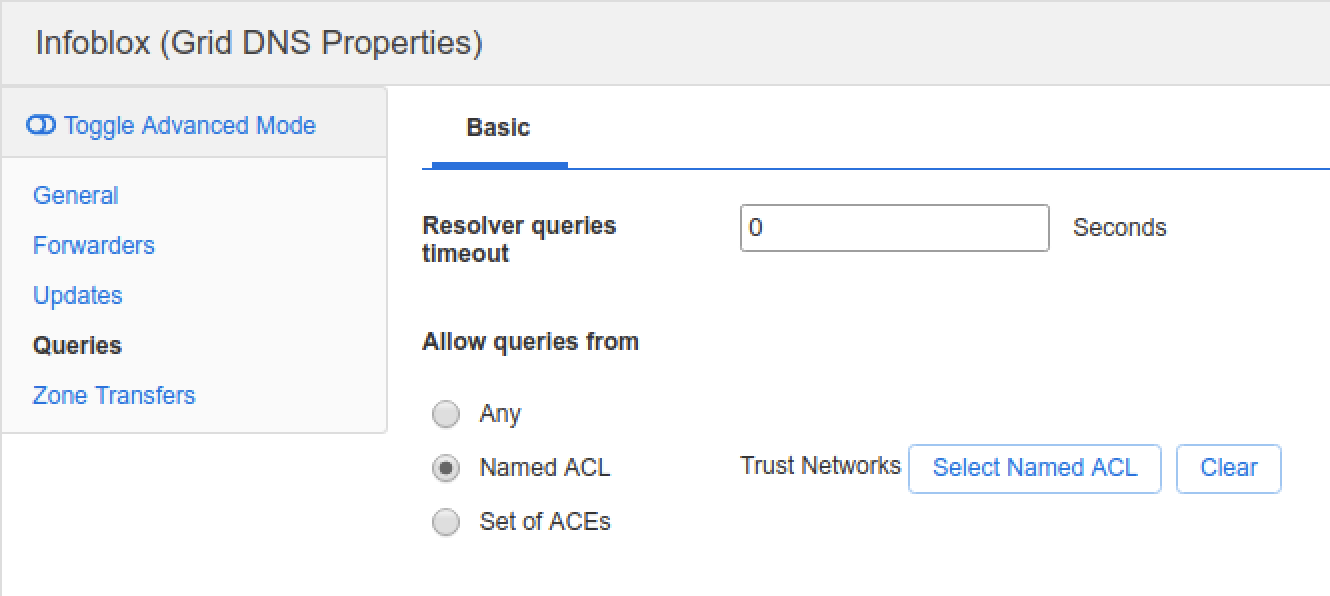
Select Queries and under the Allow queries from section choose Named ACL
Click Select Nmaed ACL and choose Trusted Networks, then Save & Close
Restart services when prompted.
Task 2: Verifying Recursion Limitations
In this task, you will verify that the configuration done in the previous step did work.
On the Jump-Desktop(10.35.22.10):
Open a terminal window
Execute a dig command querying IBNS1 (10.100.0.105) for www.example.com
dig @10.000.0.105 www.example.com.
What was the response? why?
On the Testing-Linux:
Open a terminal window
Execute the following command:
sudo set-network-static-nios
if you get this error message: Failed to reload network settings: No such file or directory, please re-execute the command once more
Execute a dig command querying IBNS1 (10.100.0.105) for www.example.com
dig @10.000.0.105 www.example.com.
What was the response? why?
Solutions
Task 1: Named ACL and Limit Recursion
Login to the Grid Master IBGM (10.100.0.100):
Navigate to Administration → Named ACLs
Create a new ACL with the name Trusted Networks
Add the two networks 10.100.0.0/24 and 10.200.0.0/24 and the host Jump-Desktop(10.35.22.10) to the list, then Save & Close.
Navigate to Data Managment → DNS
On the Toolbar click on Grid DNS Properties
Select Queries and under the Allow queries from section choose Named ACL
Click Select Nmaed ACL and choose Trusted Networks, then Save & Close
Restart services when prompted.
Task 2: Verifying Recursion Limitations
Detailed Analysis:
On the Jump-Desktop(10.35.22.10) our dig query will be responded to normally with the NOERROR response code and an A record, this is because we added the host to the Named ACL we used allowing this host to use the Grid's recursion services, ash shown the figure below: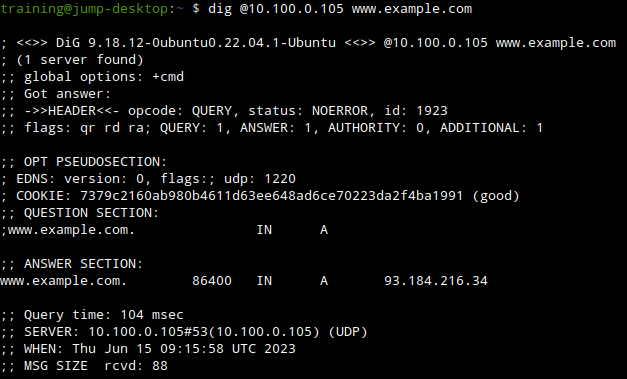
However, once we move over to Testing-Linux which is after executing the command sudo set-network-static-nios has the IP address outside of the scope of our created Named ACL Trusted Networks, as we can see below: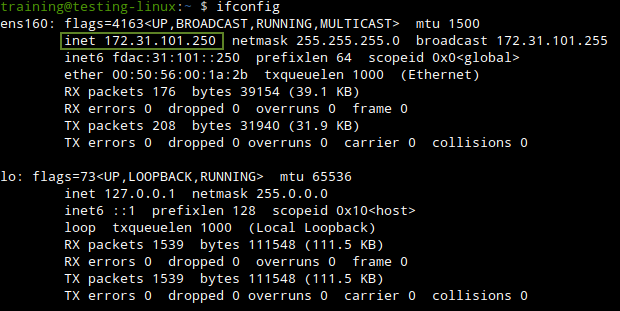
So when we execute the same dig command on Testing-Linux the response is different, we get the REFUSED response with the warning message recursion requested but not available. Which is as we know is due to the ACL blocking us from using the Grid DNS recursion services.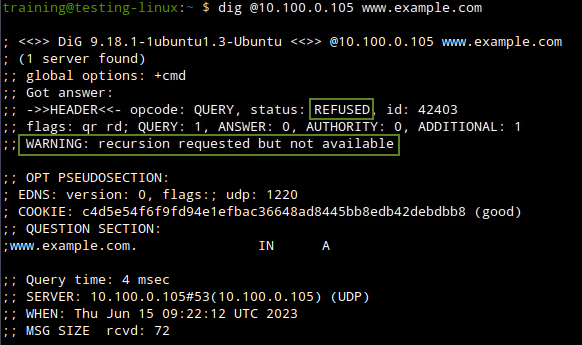
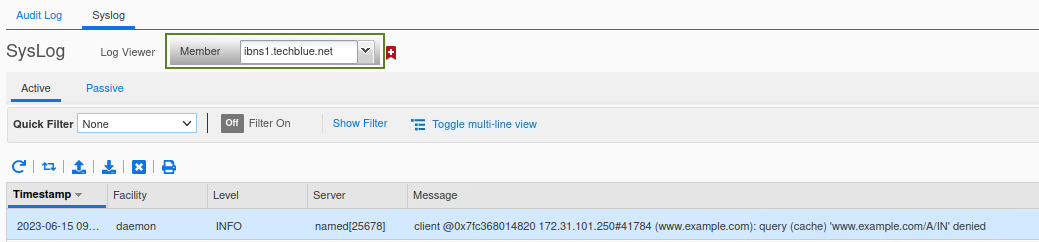
This can also be verified by the syslog message for ibns1, shown below: