Investigating Domains using Dossier (2808)
Scenario
Your SOC team has asked you to investigate domains recently connected to abnormal behaviour. Threat Defense security policies identified and blocked the risk. Your task is to use Dossier to collect as much information about these malicious domains as possible and report your findings.
Estimated Completion Time
15 to 20 Minutes
Prerequisites
Administrative access to the Infoblox Portal
Tasks
Investigate threats with Dossier.
Task 1: Investigating threats with Dossier
Log in to your lab’s jump-desktop with the credentials
training / infoblox, and use your Education Infoblox Portal Credentials to log in to the Infoblox Portal.Investigate the domains: schwabalert-secure04f.ink, rt0ia9x.top, and dateuncertainup.pro
Gather as much information about each domain to answer the following questions:
What is the risk level for each domain?
What is the threat property for each domain?
Were any of the domains detected by Feeds? If so, list the feeds.
Are any of the listed domains still active?
Are there any impacted devices in your organization?
Are there any Intel publications about any of the listed domains?
Are there any IP addresses or domains associated with any of the suspicious domains?
Where are these domains registered and hosted?
Are any of the listed domains connected to domain impersonation?
Generate a report from Dossier with all your findings.
Solutions
Task 1 Solution: Investigating threats with Dossier
Please note that your report data might not exactly match the screenshots and answers provided
In this task, we will use Infoblox Dossier to collect information about the three discovered malicious domains and answer the questions.
Log in to your lab’s jump-desktop with the credentials
training / infoblox.Use your Education Infoblox Portal Credentials to log into the Infoblox Portal.
Navigate to Monitor → Research → Dossier.
We will be investigating three domains:
tel.onl
rt0ia9x.top
dateuncertainup.pro
In the Search bar, type the name of each domain, then hit Enter.
Gather as much information about each domain to answer the following questions:
What is the threat level for each domain if available?
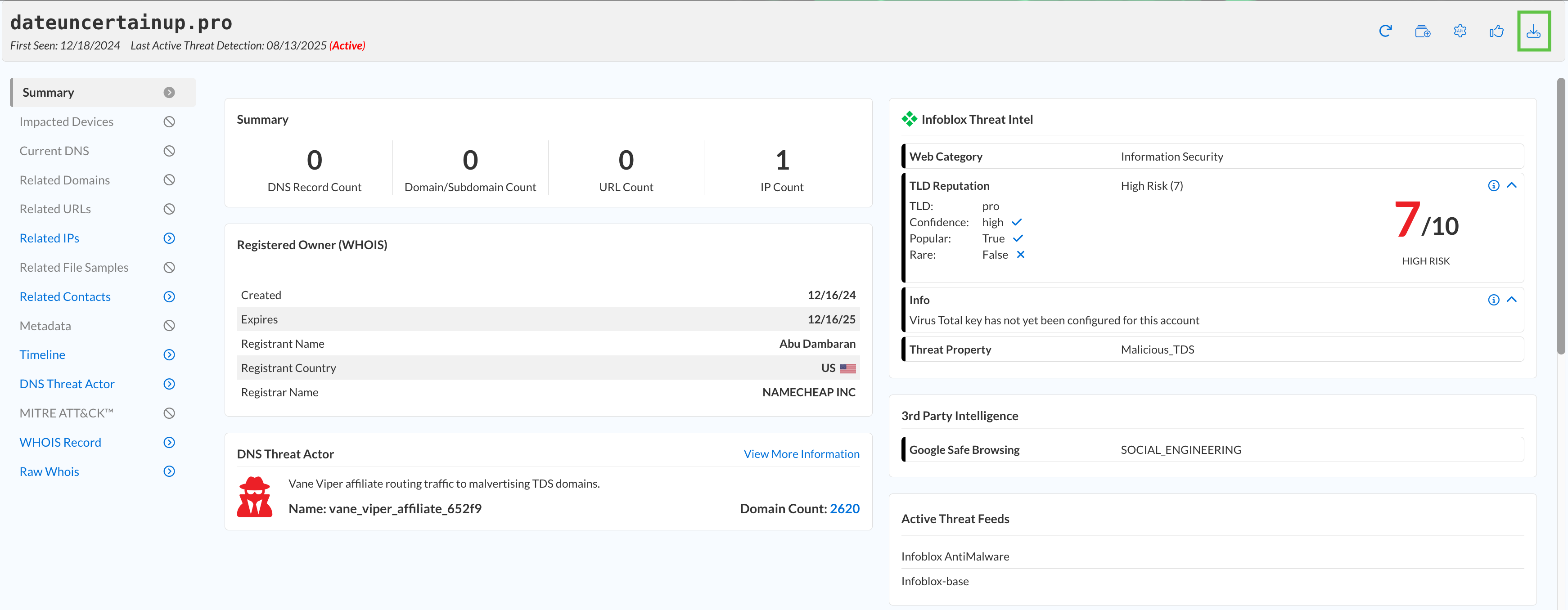
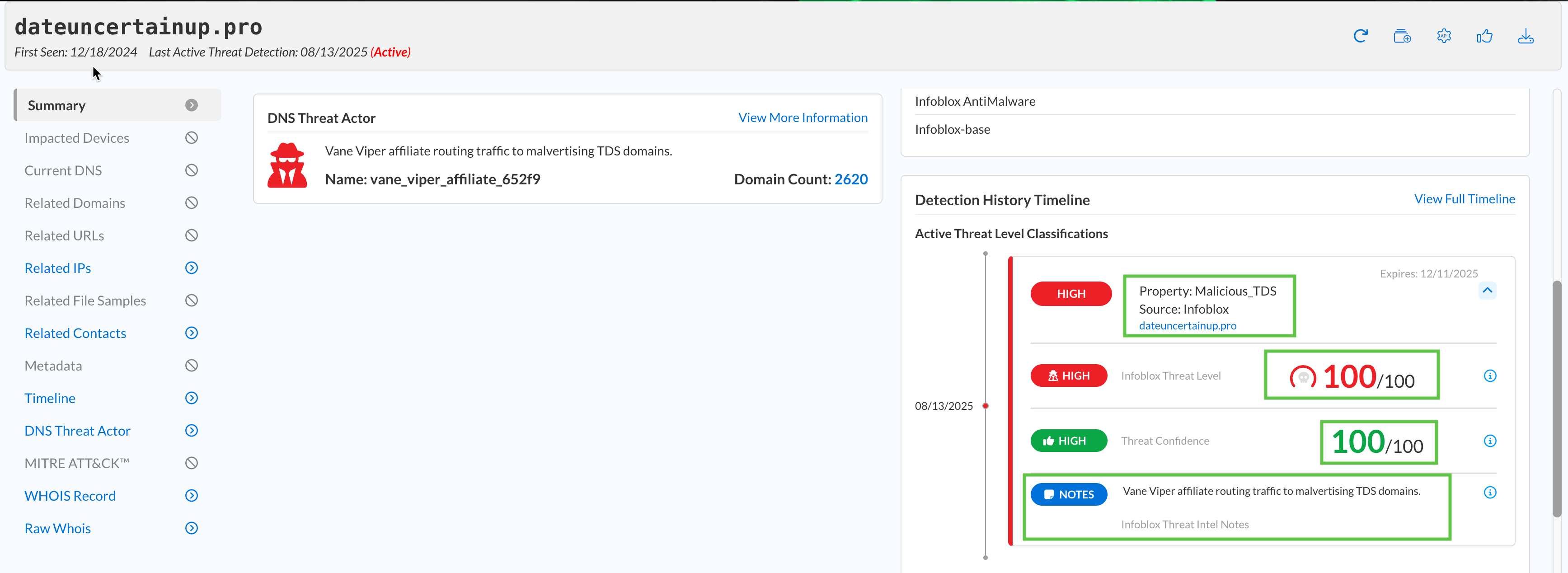
This information can be found in the summary report, specifically in the Detection History Timeline section for each domain.
tel.onl → 100/100, rt0ia9x.top → 80/100, dateuncertainup.pro → 100/100.
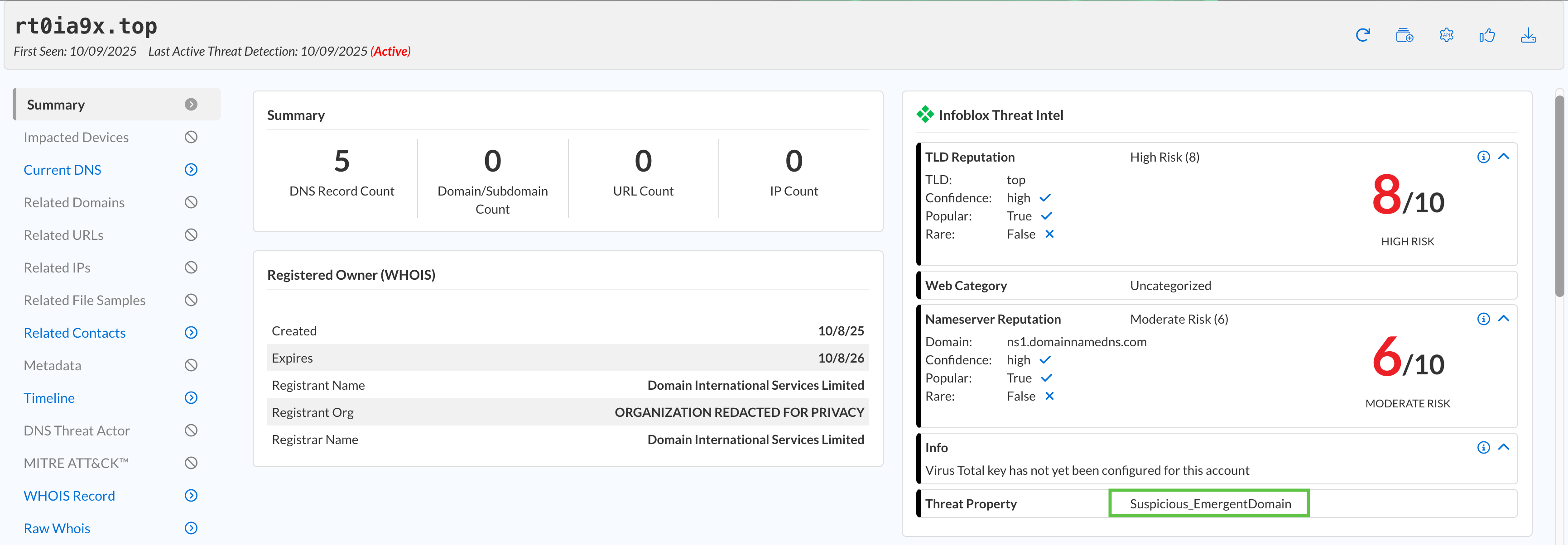
What is the threat property for each domain?
This information is found in the summary report under the Infoblox Threat Intel section for each domain.
tel.onl → Phishing_Generic, rt0ia9x.top → Suspicious_EmergentDomain, dateuncertainup.pro → Malicious_TDS.
Were any of the domains detected by Feeds? If so, list the feeds.
Each domain’s summary report under the Active Threat Feeds and Status section contains this information.
All three were detected either using Infoblox-base or Infoblox-high-risk.
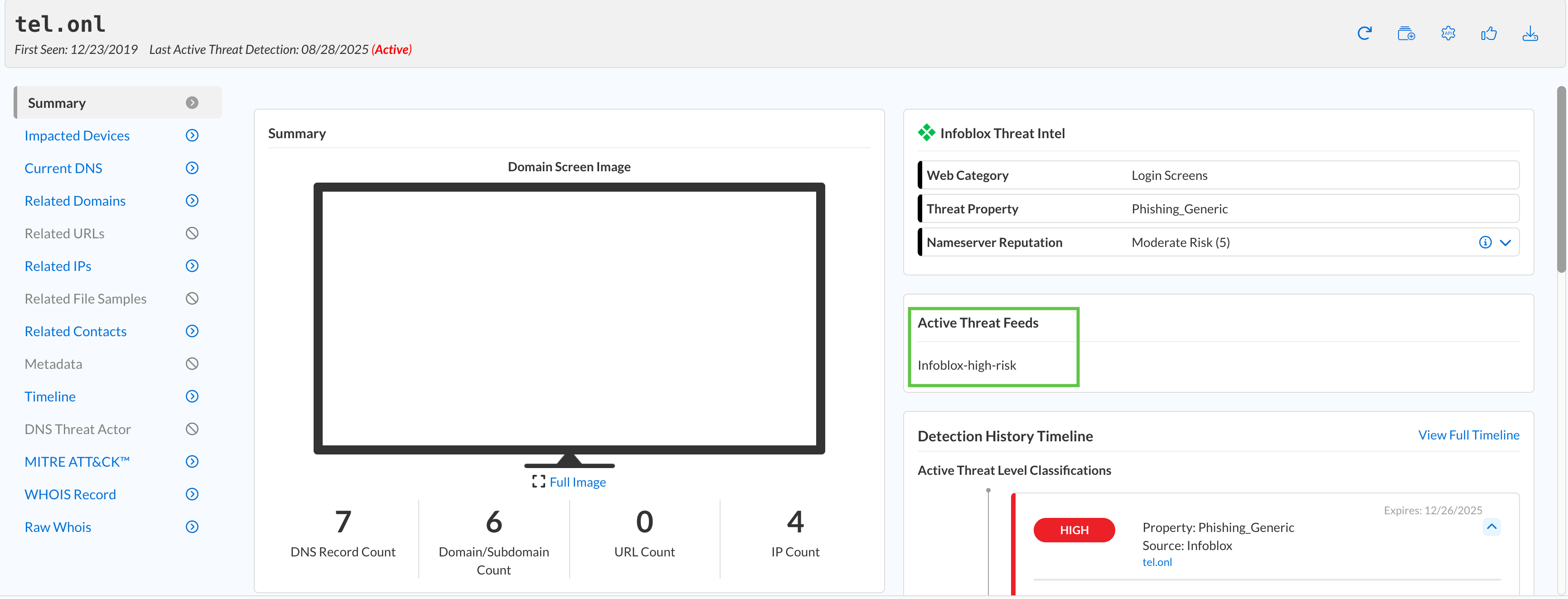
Are any of the listed domains still active?
This information is found at the top banner next to the domain name and the last detection date.
Yes, all three are still active.
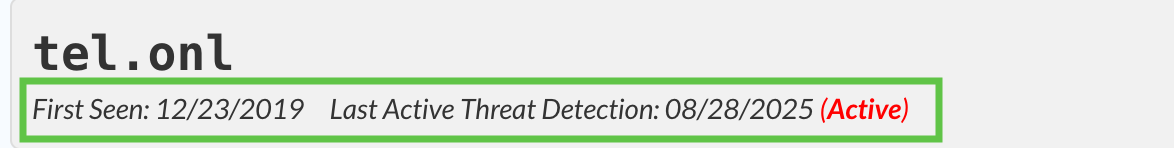
Are there any impacted devices in your organization?
We can find this information under the Impacted Devices report and by investigating security policy configurations, under Configure → Security → Policies → Security Policies.
No, multiple devices sent queries, but your organization’s threat policy using the recommended feeds blocked those attempts.
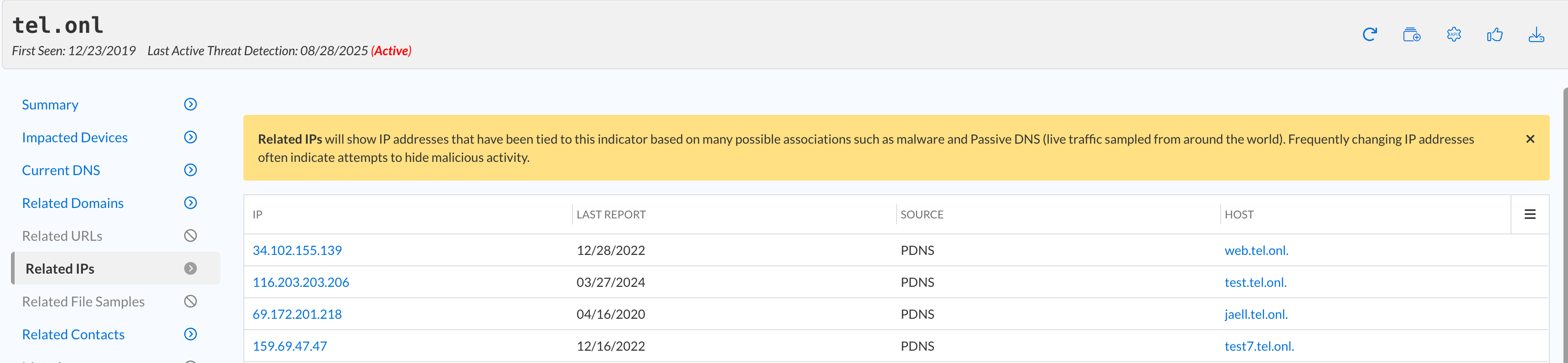
Are there any related IP addresses or domains associated with the suspicious domains?
This information is available under the Related IPs and Related Domains reports.
Yes, all three domains had either Liked IPs or Domains.
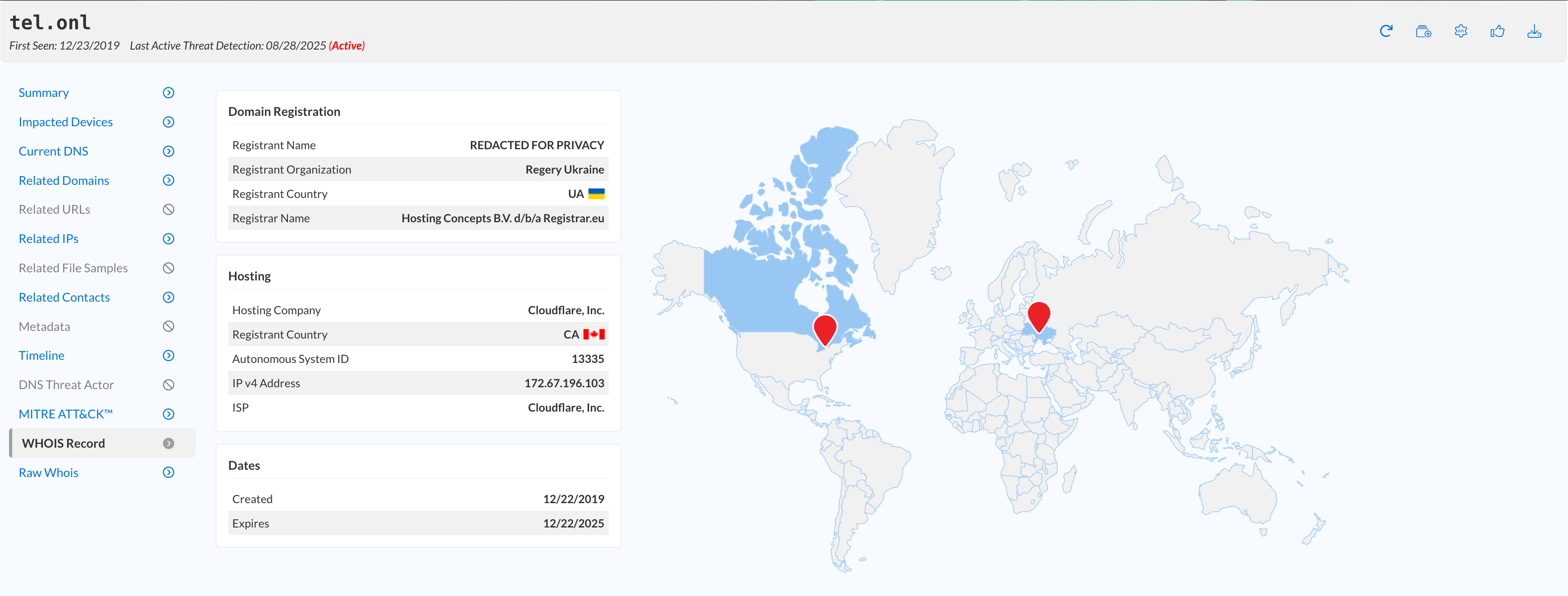
Where are these domains registered and hosted?
This information is available under the Registered Owner section on the summary and WHOIS Record reports.
tel.onl → UA/CA, rt0ia9x.top → Information unavailable, dateuncertainup.pro → US.
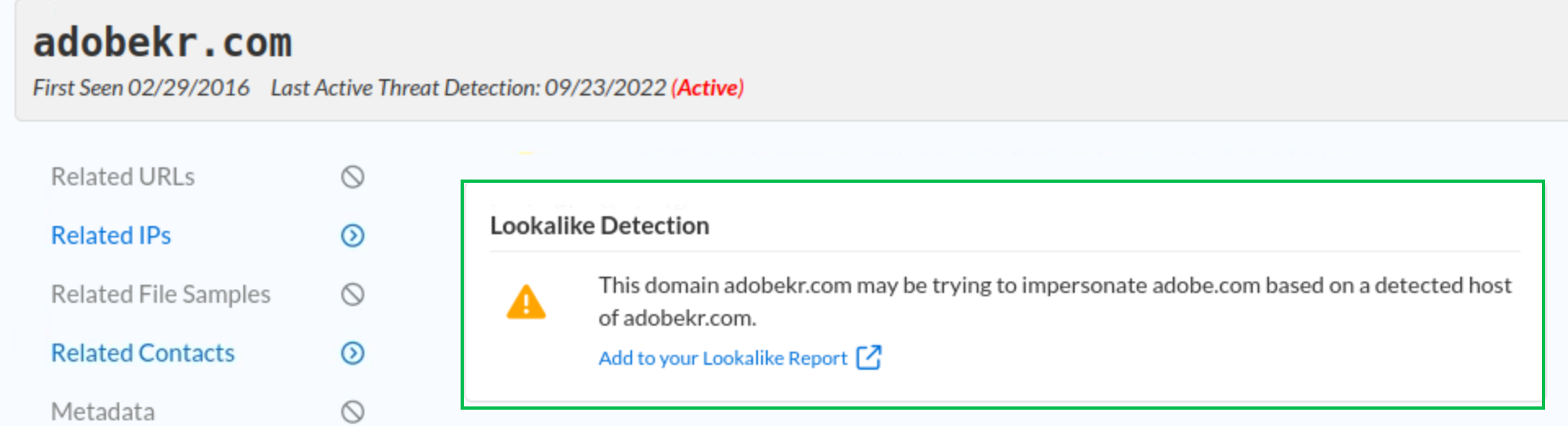
Are any of the listed domains connected to domain impersonation?
This information will be available under the Lookalike Detection section in the summary report.
No, but if a domain is a lookalike domain, a new segment will be available in the report, as shown in this example with adobekr.com.
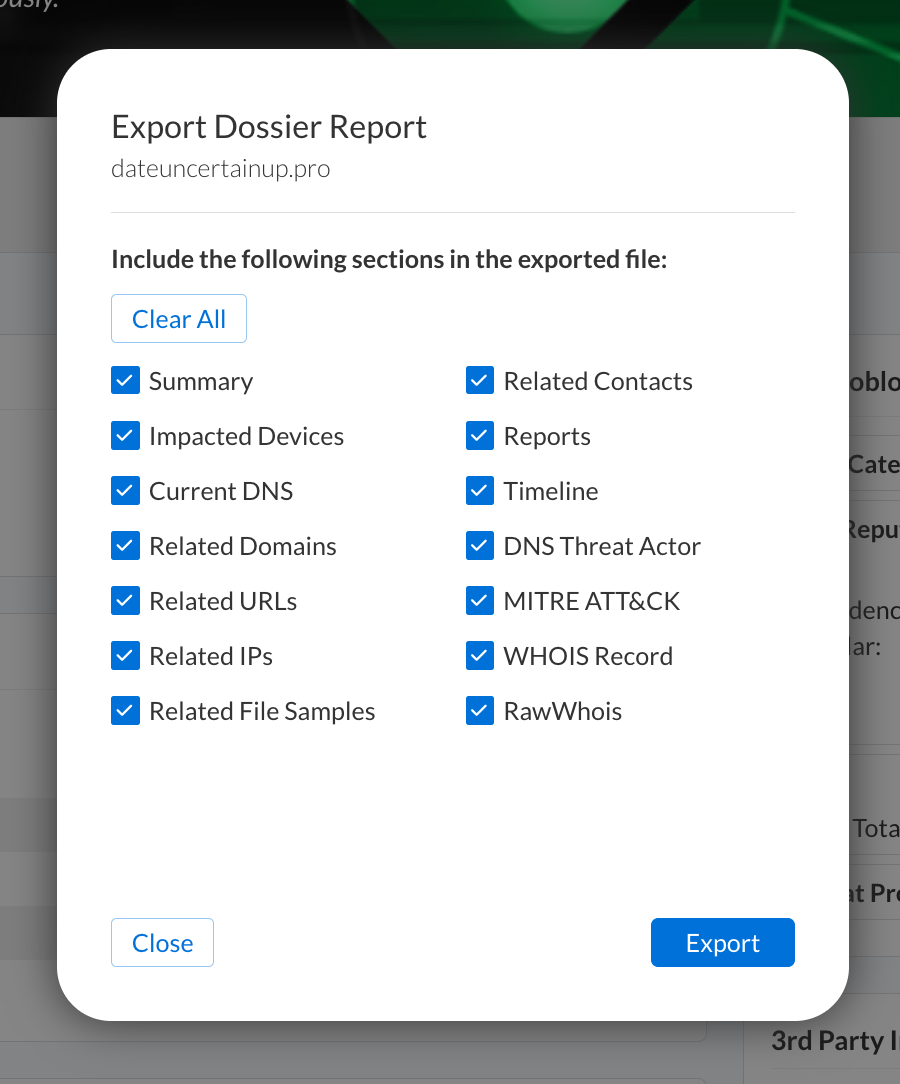
Click on the Export Dossier Report Button at the top left corner. Choose which reports to include, then click the Export button to create a PDF report.