DNSSEC signing with NSEC in NIOS (3609)
Scenario
You are a DNS administrator at a coffee company. The internal name space includes an authoritative zone coffee.corp on the server NS1 (10.100.0.111) and a delegated zone zone kona.coffee.corp on server NS2 (10.100.0.222).
The branch office does not have DNSSEC setup. They have decided to sign their zone kona.coffee.corp with NSEC instead of the recommended NSEC3.
Please assist them to perform the configuration on the child zone kona.coffee.corp as well as whatever configuration is necessary on the parent zone coffee.corp. Then show how this choice allows for zone enumeration (without zone transfer).
Estimate Completion Time
30 to 45 minutes
Credentials
Description | Username | Password | URL or IP |
|---|---|---|---|
Grid Manager UI | admin | infoblox |
Learning Content
Lab Initiation
Access jump-desktop
Once the lab is deployed, you can access the virtual machines required to complete this lab activity. To initiate the lab, click on the jump-desktop tile and login to the Linux UI:
Username: training
Password: infoblox
Initiate lab
To initiate the lab, double-click the Launch Lab icon on the Desktop.

Launch Lab
Choose the lab number from the list and click OK.
After clicking OK, you will see a pop-up message with a brief description of the lab task. If the description looks correct, click Yes to continue lab initiation.
Lab initiation will take a couple of minutes to finish.
Once complete, you will see another pop-up message with the login credentials and the URL for the Grid Manager’s User Interface. Note that the credentials may differ from those from prior labs.
Tasks
Task 1: Sign with NSEC
In this task we will sign the zone kona.coffee.corp with NSEC as the proof of non-existence
Login to NS2(10.100.0.222):
navigate to Data Management → DNS
in the Toolbar, Select Grid DNS Properties → DNSSEC
change the Resource Record Type for Nonexistance Proof to NSEC
Navigate to the unsigned authoritative zone kona.coffee.corp
in the Toolbar, click DNSSEC → Sign Zones
Task 2: Upload the DS record to the parent zone
Performing a key rollover requires uploading new DS records to the parent zone. We will perform that in this task.
Export the trust anchor from the delegated child zone.
Login to NS2, navigate to Data Management → DNS → Zones, click on kona.coffee.corp. In the Toolbar, select DNSSEC → Export Trust Anchors
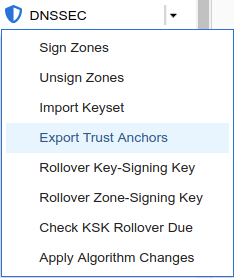
Export Trust Anchors dialog appears, select DS records and click Export.
Save the exported trust anchor to local file. It doesn't matter what you save the file name as. For our example, the file name is ds_records.txt.
Open the file in editor and leave the editor open. We will need this information for the next step.
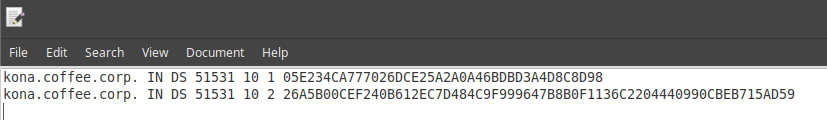
Import the exported trust anchor into the parent zone.
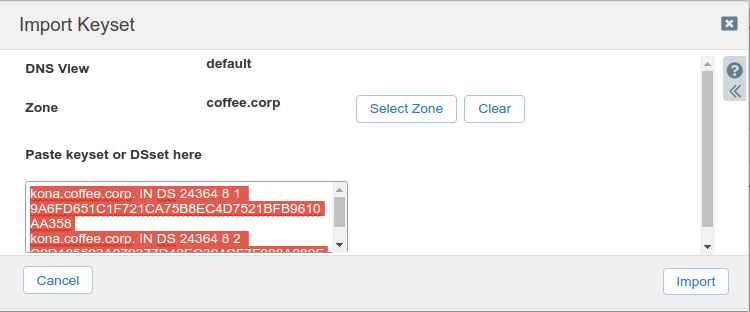
Login to NS1 (10.100.0.111), navigate to Data Management → DNS → Zones, click on coffee.corp. In the Toolbar, select DNSSEC → Import Keyset.
The Import Keyset dialog appears. Copy and paste the DS record text from text editor (ds_records.txt in our example) and click Import.
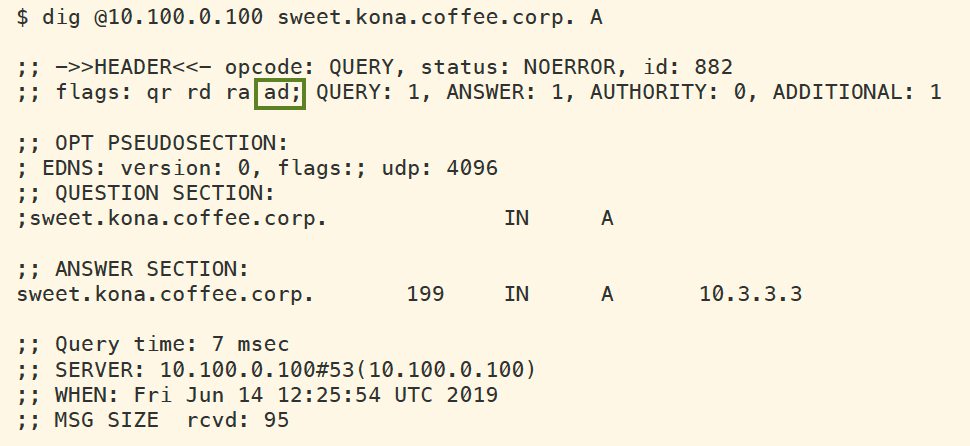
Execute lockups for domains in kona.coffee.corp to verify the AD flag is present and validation is successful.
dig @10.100.0.100 sweet.kona.coffee.corp. Adig @10.100.0.100 blend.kona.coffee.corp. A
Task 3: NSEC Zone Enumeration
In this task, we play the role of a curious client who utilizes NSEC to enumerate the zone kona.coffee.corp to learn every name in the zone.
Use your knowledge of NSEC and DNS to create queries to enumerate the zone kona.coffee.corp.
You can start with looking up the name a.kona.coffee.corp and go from there.
Solutions
Task 1 solution: Sign with NSEC & Task 2: Upload the DS record to the parent zone
Detailed Analysis:
Follow the instructions to sign the zone kona.coffee.corp on NS2 (10.100.0.222) with NSEC, and import the new DS records into coffee.corp on NS1 (10.100.0.111). After all steps have been completed, we should be able to look up names in the kona.coffee.corp domain and see the AD flag, as shown below:
Task 3 solution: NSEC Zone Enumeration
Detailed Analysis:
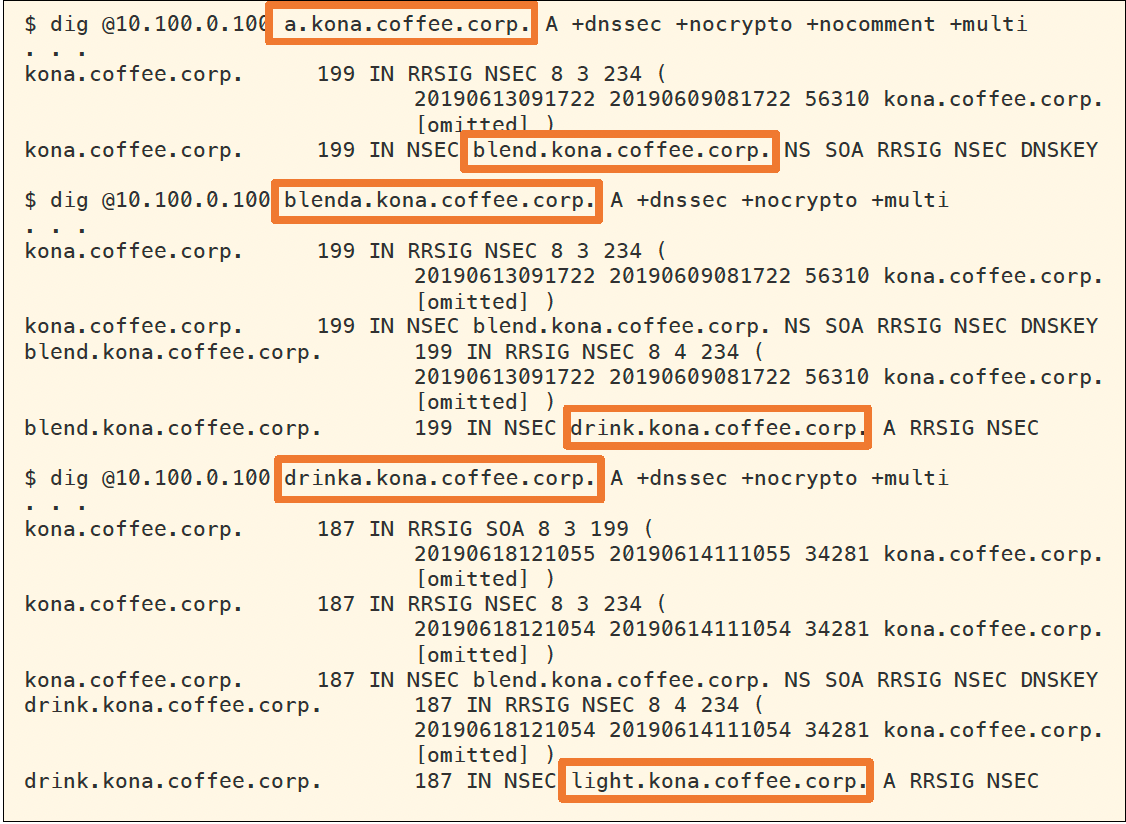
In this task, we utilize NSEC information to perform zone enumeration on kona.coffee.corp. The following figure, shows example of query and responses to perform the zone enumeration. We begin by querying for the name a.kona.coffee.corp, the NSEC response tells us the next name is blend.kona.coffee.corp; we then query for the name blenda.kona.coffee.corp, and the NSEC response tells us the next name is drink.kona.coffee.corp; we issue another query for drinka.kona.coffee.corp, and so on and so forth until we have enumerated every possible name in the authoritative zone.