Troubleshooting DNS in NIOS (3611)
Scenario
You are a DNS administrator for a company, part of your responsibilities is to resolve user submitted tickets. Users have reported their inability to resolve some domains, In the ticket the user reported www.example.com to be one of the problematic domains. You were informed that some changes were made recently to DNS servers that might have caused the issue. Please use your DNS knowledge to troubleshoot, locate the root cause(s), and make suggestions to the users.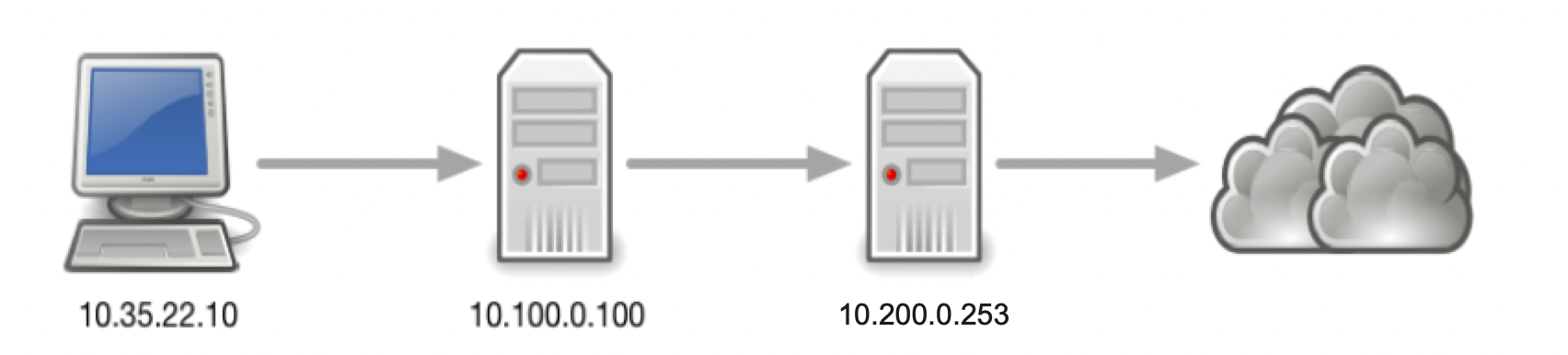
Estimate Completion Time
45 to 60 minutes
Credentials
Description | Username | Password | URL or IP |
|---|---|---|---|
Grid Manager UI | admin | infoblox |
Learning Content
Lab Initiation
Access jump-desktop
Once the lab is deployed, you can access the virtual machines required to complete this lab activity. To initiate the lab, click on the jump-desktop tile and login to the Linux UI:

Username: training
Password: infoblox
Initiate lab
To initiate the lab, double-click the Launch Lab icon on the Desktop.

Launch Lab
Choose the lab number from the list and click OK.

After clicking OK, you will see a pop-up message with a brief description of the lab task. If the description looks correct, click Yes to continue lab initiation.

Lab initiation will take a couple of minutes to finish.
Once complete, you will see another pop-up message with the login credentials and the URL for the Grid Manager’s User Interface. Note that the credentials may differ from those from prior labs.

Tasks
Task 1: First Ticket
User reports unable to resolve the name www.example.com. Please investigate root cause.
To verify the existence of the reported problem, execute the following command on the Jump-Desktop (10.35.22.10):
dig @10.100.0.100 www.example.com. AWhy did it fail?
For your convenience a packet capture is provided (3611-task1-ada.pcap)
Solutions
Task 1 solution: First Ticket
Root Cause:
ADA (10.100.0.100) forwards to BOB (10.200.0.253), which has recursion disabled.
Detailed Analysis:
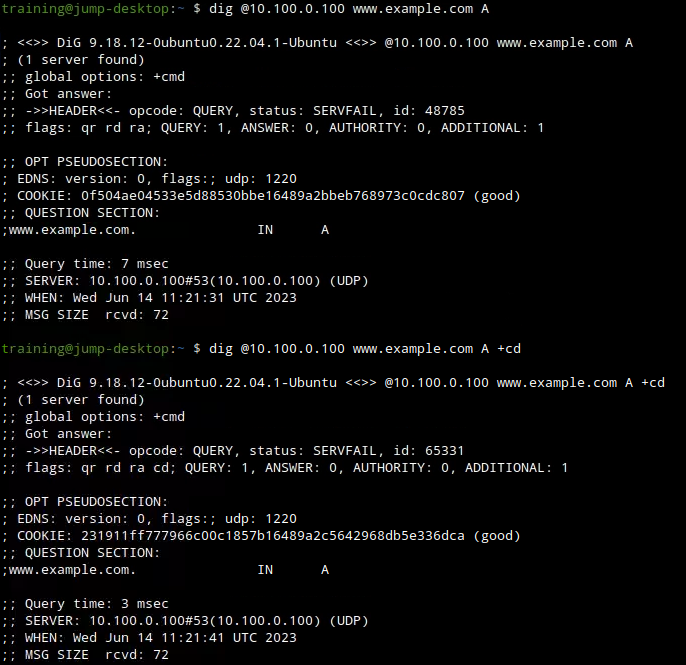
First of all, we isolate whether or not this is a DNSSEC issue, by trying the same queries twice, once without+cd, once with +cd. As seen below, we receive the exact same results, so this is not likely a DNSSEC issue, but a general DNS problem.
By investigating syslogs on ADA (10.100.0.100), we can navigate to Administration → Logs → syslog to access them we can see that the query failed due it being refused by BOB (10.200.0.253) as shown below:
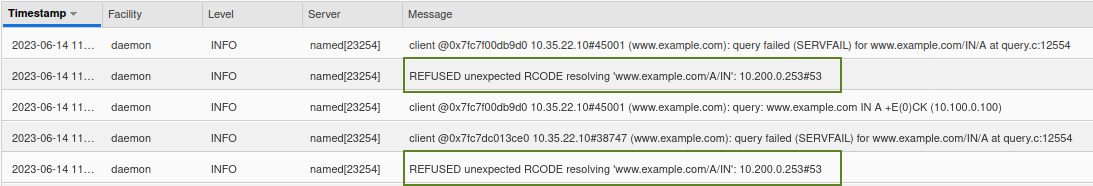
This informs us that ADA (10.100.0.100) is using BOB (10.200.0.253) as a forwarder and BOB doesn't have recursion enabled; hence why the refused response, we can verify that by doing a packet capture.During the capture we can see that queries are forwarded from ADA to BOB, and they are getting the REFUSED return code, as shown below: