Phantom Domains and NXDOMAIN attack protection in NIOS (3614)
Scenario
Your organization has decided to apply security hardening settings to your Grid members serving DNS. Please make the necessary configuration changes in the Grid to allow protection against both Phantom Domain attacks and NXDOMAIN attacks.
Estimate Completion Time
20 to 25 minutes
Credentials
Description | Username | Password | URL or IP |
|---|---|---|---|
Grid Manager UI | admin | infoblox |
Requirements
Administrative DNS access to the Grid
Which networks can perform DNS queries (connect on port 53)
Learning Content
Lab Initiation
Access jump-desktop
Once the lab is deployed, you can access the virtual machines required to complete this lab activity. To initiate the lab, click on the jump-desktop tile and login to the Linux UI:

Username: training
Password: infoblox
Initiate lab
To initiate the lab, double-click the Launch Lab icon on the Desktop.

Launch Lab
Choose the lab number from the list and click OK.

After clicking OK, you will see a pop-up message with a brief description of the lab task. If the description looks correct, click Yes to continue lab initiation.

Lab initiation will take a couple of minutes to finish.
Once complete, you will see another pop-up message with the login credentials and the URL for the Grid Manager’s User Interface. Note that the credentials may differ from those from prior labs.

Tasks
Task 1: Adding Phantom Domain protection
In this task, you will update the Grid DNS settings to protect against phantom domain attacks.
Login to the Grid Master IBGM (10.100.0.100):
Navigate to Data Managment → DNS
On the Toolbar click on Grid DNS Properties
Select Security (toggle advanced mode if needed)
Under the NON-RESPONSIVE SERVERS section:
What settings are enabled by default?
Select the appropriate settings to protect against phantom domain attacks
Task 2: Adding NXDOMAIN protection
In this task, you will update the Grid DNS settings to protect against NXDOMAIN attacks.
Login to the Grid Master IBGM (10.100.0.100):
Navigate to Data Managment → DNS
On the Toolbar click on Grid DNS Properties
Select Security (toggle advanced mode if needed)
Under the BOGUS-QUERY Alerting AND MITIGATION section:
What settings are enabled by default?
Select the appropriate settings to protect against NXDOMAIN attacks.
Solutions
Task 1 solution: Adding Phantom Domain protection
NIOS DNS Security settings can be configured at the Grid or the Member level. This solution shows how to configure it at the Grid level. To access NIOS DNS Security settings, login to the grid master IBGM(10.100.0.100), navigate to Data Management → DNS, from the Toolbar, select Grid DNS Properties. The dialog window appears, toggle the Advance Mode, and select the Security tab.
There are 3 main options in the section NON-RESPONSIVE-SERVERS that guard against phantom domain attacks, all 3 are unchecked by default. The more conservative option to enable is the hold down option, as shown below: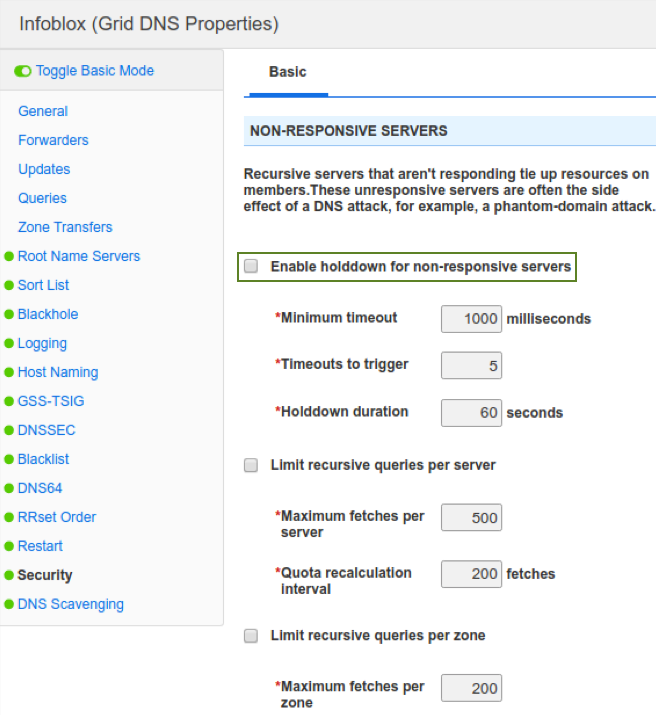
Brief description of each of the 3 options:Enable holddown for non-responsive servers: This checkbox enables the recursive server to stop sending queries to non-responsive servers for a specified time period (holddown duration), limiting the effectiveness of phantom domain attack.
Limit recursive queries per server: This checkbox limits the number of queries upstream to other servers,and if it exceeds the limit, clients get SERVFAIL. Before enabling, you should gather statistics to establish base line numbers, otherwise you risk causing errors for legitimate clients.
Limit recursive queries per zone: This checkbox limits the number of queries sent to a zone or domain,and if it exceeds the limit, clients get SERVFAIL. Before enabling, you should gather statistics to establish base line numbers, otherwise you risk causing errors for legitimate clients.
Task 2 solution: Adding NXDOMAIN protection
NIOS DNS Security settings can be configured at the Grid or the Member level. This solution shows how to configure it at the Grid level. To access NIOS DNS Security settings, login to the grid master IBGM(10.100.0.100), navigate to Data Management → DNS, from the Toolbar, select Grid DNS Properties. The dialog window appears, toggle the Advance Mode, and select the Security tab.
There are 3 main options in the section BOGUS-QUERY Alerting AND MITIGATION that guard against NXDOMAIN domain attacks, all 3 are unchecked by default. The more conservative option to enable is the hold down option, as shown below: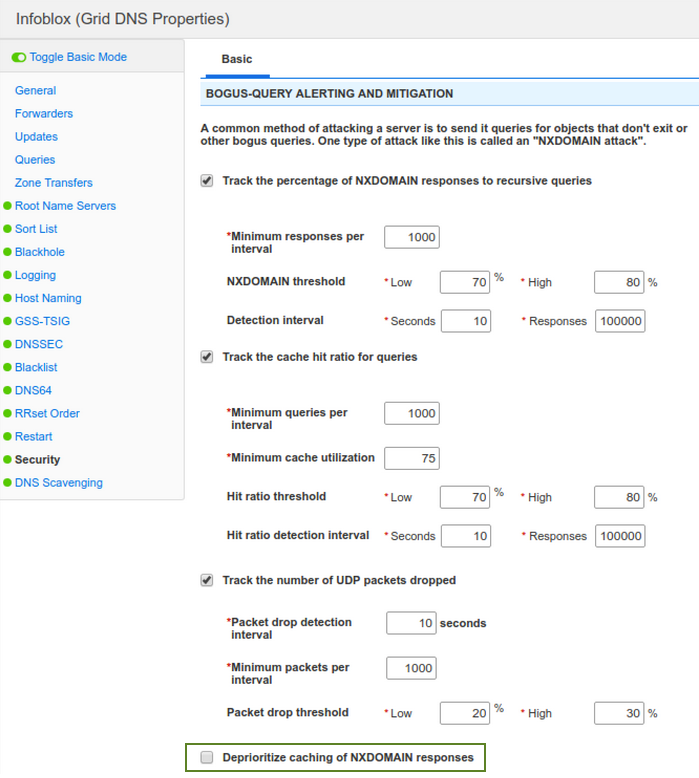
This option splits the DNS cache in two, one for NX (non-existent) responses, and one for all other responses. DNS server always removes the least recently used (LRU) item from the NX list first. This prevents the overall cache being filled up by NXDOMAIN responses.
