Interpreting Authoritative and Non-Authoritative DNS Responses (1530)
Scenario
In this lab, you will practice distinguishing between authoritative and non-authoritative DNS responses. You will also explore how the TTL (Time to Live) field changes in non-authoritative responses and understand the significance of the AA (Authoritative Answer) flag in DNS responses.
Estimate Completion Time
10 to 15 minutes
Requirements:
Access to the online Dig Web Interface or a system with the dig command-line tool installed and internet access
Learning Content
Tasks
We suggest using the Dig Web Interface for this lab, as the Dig tool may not be installed on all machines. If you already have Dig installed on your system, you may use Command Prompt or Terminal to complete these tasks.
Task 1:Query an Authoritative DNS Server
Use the Dig Web Interface to look up the domain login.ddi.ninja. Use the DNS server mimosa.techblue.io.
Task 2: Query a Non-Authoritative DNS Server
Use the Dig Web Interface to look up the domain login.ddi.ninja. Use the default DNS server (or any open DNS servers such as 8.8.8.8). Compare the response with the one from Task 1, focusing on the AA flag and the TTL value.
Task 3: Observe TTL Decrease in Non-Authoritative Response
Repeat the non-authoritative DNS query from Task 2 several more times at intervals. Observe how the TTL value decreases with each subsequent query.
Solutions
Task 1 Solution: Query an Authoritative DNS Server
You can query an authoritative DNS server using one of the following methods:
Using Dig Web Interface:
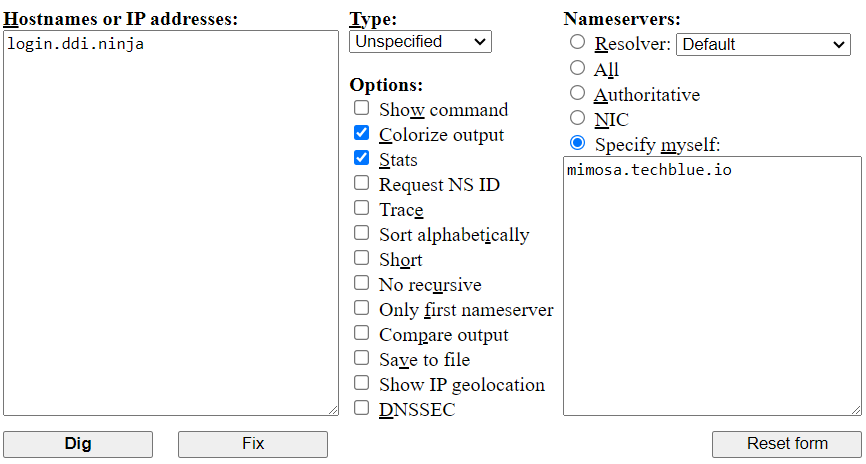
Access Dig Web Interface using a web browser.
Enter login.ddi.ninja in the "Hostnames or IP addresses" field.
Enter mimosa.techblue.io in the "Nameservers" field and select Specify myself.
Enable the Colorize output and Stats options.
Click Dig.
Using Terminal (Linux and macOS):
Open the terminal on your system.
Linux: Press Ctrl + Alt + T to open the terminal.
macOS: Press Command + Space, type Terminal, and press Enter.
Run the following command:
dig @mimosa.techblue.io login.ddi.ninja.
Using Command Prompt (Windows):
Open the Command Prompt by pressing Win + R, typing cmd, and pressing Enter.
If you have dig installed, run the following command:
dig @mimosa.techblue.io login.ddi.ninja.
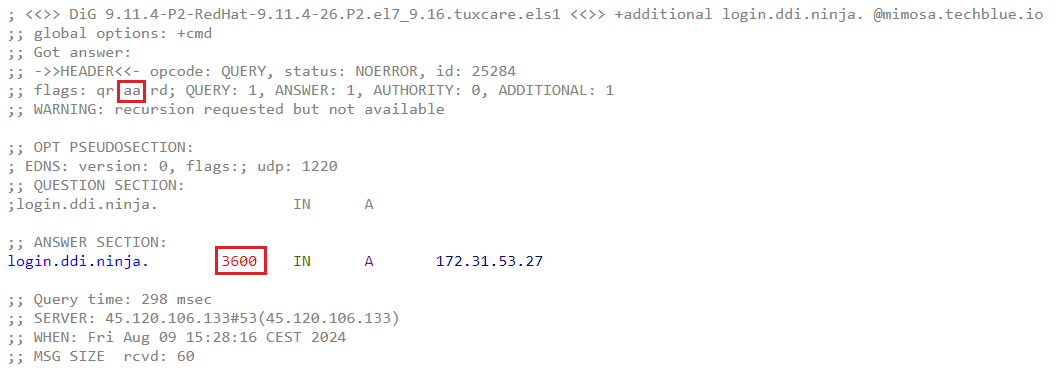
Expected Output:
The AA flag should be present, indicating an authoritative answer, and the TTL value should remain consistent across repeated queries.
Task 2 Solution: Query a Non-Authoritative DNS Server
You can query a non-authoritative DNS server using one of the following methods:
Using Dig Web Interface:
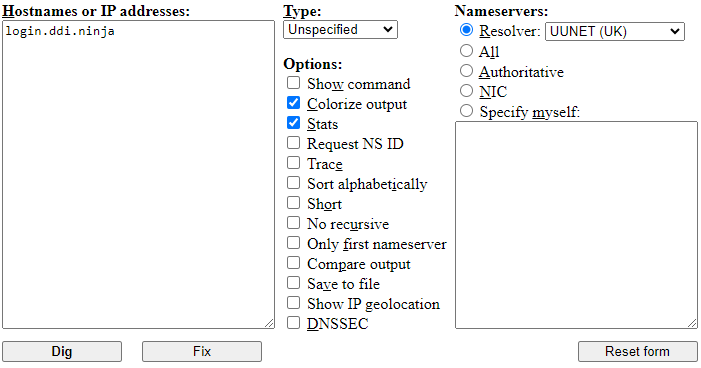
Access Dig Web Interface using a web browser.
Enter login.ddi.ninja in the "Hostnames or IP addresses" field.
Under the "Nameservers" field, select the Resolver option. From the dropdown, select UUNET (UK).
Enable the Colorize output and Stats options.
Click Dig.
Using Terminal (Linux and macOS):
Open the terminal on your system.
Linux: Press Ctrl + Alt + T to open the terminal.
macOS: Press Command + Space, type Terminal, and press Enter.
Run the following command:
dig login.ddi.ninja.
Using Command Prompt (Windows):
Open the Command Prompt by pressing Win + R, typing cmd, and pressing Enter.
If you have
diginstalled, run the following command:dig login.ddi.ninja.
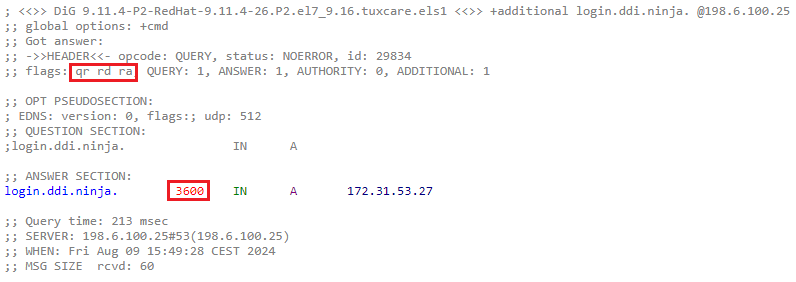
Expected Output
The AA flag should not be present, indicating a non-authoritative answer, and the TTL value should begin to decrease with repeated queries.
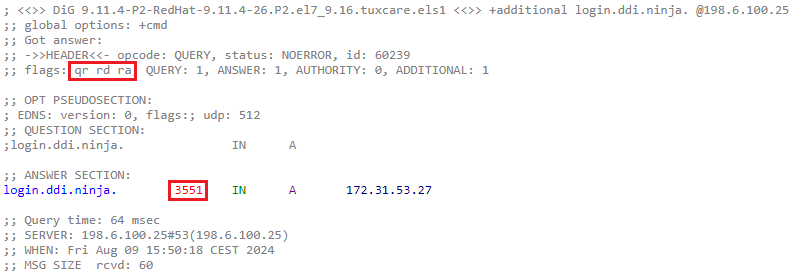
Task 3 Solution: Query a Non-Authoritative DNS Server
Repeat the non-authoritative DNS query from Task 2 multiple times at intervals using either the Dig Web Interface, dig command.
Expected Output:
Compare the TTL values in the responses after each query. Notice how the TTL value decreases with each subsequent query, reflecting the passage of time in the cached response.


When querying the same DNS recursive resolver, the TTL decreases with each repeated query because the TTL reflects the remaining time the response is valid in the resolver's cache. However, if your queries are directed to different DNS servers within a service provider's network—such as Google Public DNS (8.8.8.8), Cloudflare DNS (1.1.1.1), or OpenDNS (208.67.222.222)—the TTL might not decrease consistently. This is because your query could be routed to a different server each time, and each server has its own cache, resulting in varying TTLs.
