Tracing DNS Delegation with Dig (2560)
Scenario
In this lab, you will trace DNS delegation for the domain name shopping.ddi.ninja using the dig +trace command. You will observe the delegation path and interpret the responses returned by each name server along the way.
Estimate Completion Time
15 to 20 minutes
Requirements
Access to the online tool Dig Web Interface or a system with the
digcommand-line tool installed and internet access
Learning Content
Tasks
We suggest using the Dig Web Interface for this lab, as the Dig tool may not be installed on all machines. If you already have Dig installed on your system, you may use Command Prompt or Terminal to complete this lab.
Task 1: Perform a DNS Trace
Use the Dig Web Interface to trace the DNS delegation for shopping.ddi.ninja
Task 2: Interpretation of DNS Delegation Output
Interpret the DNS delegation output to understand how DNS queries are processed at various levels, from root servers to authoritative name servers.
Solutions
Task 1 Solution: Perform a DNS Trace
You can trace DNS delegation using one of the following methods:
Using Dig Web Interface:
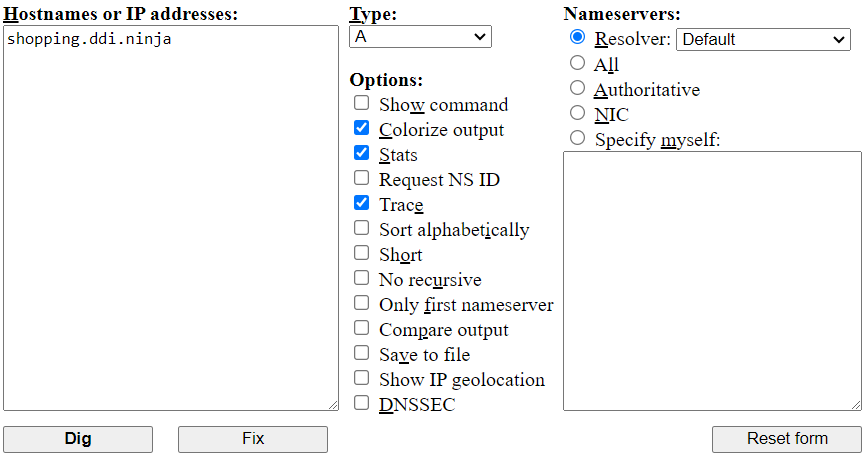
Access Dig Web Interface using a web browser.
Enter shopping.ddi.ninja in the "Hostnames or IP addresses" field.
Select A in the "Type" dropdown.
Under the "Nameservers" field, select the Resolver option. From the dropdown, select Default to use the default resolver.
Enable the Colorize output, Stats, and Trace options.
Click Dig.
Using Terminal (Linux and macOS):
Open the terminal on your system.
Linux: Press Ctrl + Alt + T to open the terminal.
macOS: Press Command + Space, type Terminal, and press Enter.
Run the following command:
dig shopping.ddi.ninja. A +trace +multi +nocrypto
Using Command Prompt (Windows):
Open the Command Prompt by pressing Win + R, typing cmd, and pressing Enter.
If you have dig installed, run the following command:
dig shopping.ddi.ninja. A +trace +multi +nocrypto
This command will output the trace, showing each step in the DNS delegation process when the dig utility is used from the command line. Below is an example of the trace output:
% dig shopping.ddi.ninja. A +trace +multi +nocrypto
; <<>> DiG 9.10.6 <<>> shopping.ddi.ninja. A +trace +multi +nocrypto
;; global options: +cmd
. 3091 IN NS e.root-servers.net.
. 3091 IN NS f.root-servers.net.
. 3091 IN NS g.root-servers.net.
. 3091 IN NS h.root-servers.net.
. 3091 IN NS i.root-servers.net.
. 3091 IN NS j.root-servers.net.
. 3091 IN NS k.root-servers.net.
. 3091 IN NS l.root-servers.net.
. 3091 IN NS m.root-servers.net.
. 3091 IN NS a.root-servers.net.
. 3091 IN NS b.root-servers.net.
. 3091 IN NS c.root-servers.net.
. 3091 IN NS d.root-servers.net.
. 3091 IN RRSIG NS 8 0 518400 (
20240818170000 20240805160000 20038 .
[omitted] )
;; Received 717 bytes from 127.0.0.2#53(127.0.0.2) in 44 ms
ninja. 172800 IN NS v0n0.nic.ninja.
ninja. 172800 IN NS v0n1.nic.ninja.
ninja. 172800 IN NS v0n2.nic.ninja.
ninja. 172800 IN NS v0n3.nic.ninja.
ninja. 172800 IN NS v2n0.nic.ninja.
ninja. 172800 IN NS v2n1.nic.ninja.
ninja. 86400 IN DS 46082 8 2 (
[omitted] )
ninja. 86400 IN RRSIG DS 8 1 86400 (
20240819050000 20240806040000 20038 .
[omitted] )
;; Received 764 bytes from 170.247.170.2#53(b.root-servers.net) in 28 ms
ddi.ninja. 3600 IN NS kochab.techblue.io.
ddi.ninja. 3600 IN NS mimosa.techblue.io.
ddi.ninja. 3600 IN NS pollux.techblue.io.
ddi.ninja. 3600 IN NS castor.techblue.io.
5tp114rg535tp80r8qpe7mhes2orqd7s.ninja. 3600 IN NSEC3 1 1 0 73 (
5TSFHCSCD4S5N3HFOFDMSUD5GS59NHTE
NS SOA RRSIG DNSKEY NSEC3PARAM )
5tp114rg535tp80r8qpe7mhes2orqd7s.ninja. 3600 IN RRSIG NSEC3 8 2 3600 (
20240827135656 20240806125656 58014 ninja.
[omitted] )
ln2ucok3mhagn588s087hp4s54ja1n9l.ninja. 3600 IN NSEC3 1 1 0 73 (
LNT48S8A1QIEHT5F5UL76MJ6N5KPH6FL
NS DS RRSIG )
ln2ucok3mhagn588s087hp4s54ja1n9l.ninja. 3600 IN RRSIG NSEC3 8 2 3600 (
20240822154146 20240801144146 58014 ninja.
[omitted] )
;; Received 633 bytes from 65.22.21.4#53(v0n1.nic.ninja) in 35 ms
shopping.ddi.ninja. 3600 IN A 172.31.53.28
shopping.ddi.ninja. 3600 IN A 172.31.53.30
shopping.ddi.ninja. 3600 IN A 172.31.53.31
;; Received 95 bytes from 45.120.106.133#53(mimosa.techblue.io) in 255 msWhen using the Dig Web Interface, the tool directs the query by default to one of the quad9 DNS servers (9.9.9.9 or 9.9.9.10), from which the root server list is retrieved.
; <<>> DiG 9.11.4-P2-RedHat-9.11.4-26.P2.el7_9.16.tuxcare.els1 <<>> +additional +trace shopping.ddi.ninja. @9.9.9.10
;; global options: +cmd
. 1597 IN NS g.root-servers.net.
. 1597 IN NS i.root-servers.net.
. 1597 IN NS e.root-servers.net.
. 1597 IN NS f.root-servers.net.
. 1597 IN NS l.root-servers.net.
. 1597 IN NS m.root-servers.net.
. 1597 IN NS h.root-servers.net.
. 1597 IN NS j.root-servers.net.
. 1597 IN NS d.root-servers.net.
. 1597 IN NS a.root-servers.net.
. 1597 IN NS c.root-servers.net.
. 1597 IN NS b.root-servers.net.
. 1597 IN NS k.root-servers.net.
. 1597 IN RRSIG NS 8 0 518400 20240907170000 20240825160000 20038 . yYmN/Amos7GAQxGjiZGDwoAOcNOVPVGgBRqFwkwDKxxM/gjQJHYUBOOi s/cZcfb2CbBtjkYZq4YMGcUADWuA7TLGzHignWtIS6rm3dSK26VxRzou 0Uc9zlLM4GNLtFx6B0kOU/mbvM5T0rx3Hmu1b0eatQllVJj61835yAES 50/nirbe7mbCGUTPTP0mSxO0GdJ7Kxr70l7rsVHbP9RXjjmYxdWtACz2 E0g58GDspRLmfOf43st9sMEv1p/lFJt3X39tgFBjY9HvHUgIvz1jOcmR RLuh7l48V+0qkJyNZ9mBRZuzVMHTlkh8v249Vq/wg/mzbHjE9LsmcUYp SCxDRQ==
;; Received 525 bytes from 9.9.9.10#53(9.9.9.10) in 1 ms
ninja. 172800 IN NS v0n0.nic.ninja.
ninja. 172800 IN NS v0n1.nic.ninja.
ninja. 172800 IN NS v0n2.nic.ninja.
ninja. 172800 IN NS v0n3.nic.ninja.
ninja. 172800 IN NS v2n0.nic.ninja.
ninja. 172800 IN NS v2n1.nic.ninja.
ninja. 86400 IN DS 46082 8 2 C8F816A7A575BDB2F997F682AAB2653BA2CB5EDDB69B036A30742A33 BEFAF141
ninja. 86400 IN RRSIG DS 8 1 86400 20240908050000 20240826040000 20038 . CrBaN5Pqrl0z1PAaUjvr2oX0LPY68FOZP//UFivHXzALcAZdovbtbf0j 6CwdAoskp0/WdEw2tdQujFgtFlui18fjzkAjkGmPmlzQi2plRagE9S7I +p+5rr0q2pOHzkmVVBY7PWQXEtZ54kQrubFQ6yeZrY/QnWIX1RJb91ck b2kEqaN7Fb7LGJszpEVvtohnD5YNcwCT9XvalwW+qji3seiUvDU0QAYG 9pmnCExd5u9klAYVAiKDFozRAKPfA5e0yN/JkCGxORFnMAexsOOW7zC9 ymG2lHws9SwOwcpgv/txTThBV0F7IOo6o0uvrWaUGWW6LZoFT7ImUbwt ZSBYwg==
;; Received 764 bytes from 199.7.91.13#53(d.root-servers.net) in 1 ms
ddi.ninja. 3600 IN NS mimosa.techblue.io.
ddi.ninja. 3600 IN NS pollux.techblue.io.
ddi.ninja. 3600 IN NS kochab.techblue.io.
ddi.ninja. 3600 IN NS castor.techblue.io.
5tp114rg535tp80r8qpe7mhes2orqd7s.ninja. 3600 IN NSEC3 1 1 0 73 5TSFHCSCD4S5N3HFOFDMSUD5GS59NHTE NS SOA RRSIG DNSKEY NSEC3PARAM
5tp114rg535tp80r8qpe7mhes2orqd7s.ninja. 3600 IN RRSIG NSEC3 8 2 3600 20240916154738 20240826144738 58014 ninja. W1wCSf0TIZmT93loZvqTb7o2EjA4nMiNb8bqbek+pX3dvsQd4Svr8Jsc 3MsR7l6DXQV63axe9Uq2sFN1gnr/QNOiFGgJZtGnSltJ4UgDyE0qfhlO dAjQebx3iOIoh+KB1NV7qO/1wxwrA+t6RYTLuT7RBRKtdUvwR3FG0ARc 01E=
ln2ucok3mhagn588s087hp4s54ja1n9l.ninja. 3600 IN NSEC3 1 1 0 73 LNT48S8A1QIEHT5F5UL76MJ6N5KPH6FL NS DS RRSIG
ln2ucok3mhagn588s087hp4s54ja1n9l.ninja. 3600 IN RRSIG NSEC3 8 2 3600 20240915155245 20240825145245 58014 ninja. Y882Ga9Mgo+7trFqS+bNE3j6eZ1y/Z4jpJHsDG/9OTHBIJur9tT9J9bA oH4qSl77o1+utf7rT7Cjb+wTH4j83TzN86qedhut+8qJPY0BkePtRTVz E8KNyoR53f5UmIAggo2vTDIu3A4uXP8JL/jP898j1M2B427iAA9BSQAN JOw=
;; Received 633 bytes from 65.22.21.4#53(v0n1.nic.ninja) in 253 ms
shopping.ddi.ninja. 3600 IN A 172.31.53.31
shopping.ddi.ninja. 3600 IN A 172.31.53.28
shopping.ddi.ninja. 3600 IN A 172.31.53.30
;; Received 95 bytes from 45.120.106.133#53(mimosa.techblue.io) in 230 ms
Task 2 Solution: Interpreting the DNS Delegation Output
When performing the dig +trace query, the DNS query is sent to multiple servers in sequence as the resolver traces the path of delegation from the root to the authoritative name servers for the requested domain. Let's break down the output and explain each section:
Section A: Root Servers
. 3091 IN NS e.root-servers.net.
. 3091 IN NS f.root-servers.net.
. 3091 IN NS g.root-servers.net.
. 3091 IN NS h.root-servers.net.
. 3091 IN NS i.root-servers.net.
. 3091 IN NS j.root-servers.net.
. 3091 IN NS k.root-servers.net.
. 3091 IN NS l.root-servers.net.
. 3091 IN NS m.root-servers.net.
. 3091 IN NS a.root-servers.net.
. 3091 IN NS b.root-servers.net.
. 3091 IN NS c.root-servers.net.
. 3091 IN NS d.root-servers.net.
...
;; Received 717 bytes from 127.0.0.2#53(127.0.0.2) in 44 msThe query starts by contacting the root DNS servers. In this case, the root server list is retrieved from the localhost’s root hints file. It returns a list of 13 NS records, each representing a root name server (e.g., a.root-servers.net, b.root-servers.net, m.root-servers.net., etc.).
Section B: TLD (ninja.) Servers
ninja. 172800 IN NS v0n0.nic.ninja.
ninja. 172800 IN NS v0n1.nic.ninja.
ninja. 172800 IN NS v0n2.nic.ninja.
ninja. 172800 IN NS v0n3.nic.ninja.
ninja. 172800 IN NS v2n0.nic.ninja.
ninja. 172800 IN NS v2n1.nic.ninja.
...
;; Received 764 bytes from 170.247.170.2#53(b.root-servers.net) in 28 msNow the trace continues by querying one of the root name servers from the list (in this case, b.root-servers.net). The root server returns a referral to the authoritative name servers for the ninja. TLD. The response contains NS records for authoritative servers (e.g., v0n2.nic.ninja, v0n0.nic.ninja, etc.), which are responsible for handling domains under the ninja. top-level domain (TLD).
Section C: Second-Level Domain (ddi.ninja.) Servers
ddi.ninja. 3600 IN NS kochab.techblue.io.
ddi.ninja. 3600 IN NS mimosa.techblue.io.
ddi.ninja. 3600 IN NS pollux.techblue.io.
ddi.ninja. 3600 IN NS castor.techblue.io.
...
;; Received 633 bytes from 65.22.21.4#53(v0n1.nic.ninja) in 35 msThe trace now queries one of the authoritative name servers for the ninja. TLD (e.g., v0n1.nic.ninja). These name servers return another referral, this time providing the authoritative name servers for the second-level domain ddi.ninja. The listed NS records (e.g., pollux.techblue.io, mimosa.techblue.io) are authoritative for all DNS queries for the ddi.ninja. domain.
Section D: Final Resolution for shopping.ddi.ninja.
shopping.ddi.ninja. 3600 IN A 172.31.53.28
shopping.ddi.ninja. 3600 IN A 172.31.53.30
shopping.ddi.ninja. 3600 IN A 172.31.53.31
;; Received 95 bytes from 45.120.106.133#53(mimosa.techblue.io) in 255 msThe following iterative query is sent to one of the authoritative name servers for the ddi.ninja domain, specifically mimosa.techblue.io. The server responds with the A records for shopping.ddi.ninja., returning the corresponding IP addresses (172.31.53.31, 172.31.53.28, and 172.31.53.30). This response is an authoritative answer, meaning this server holds the final resolution for the domain query, and no further referrals are needed.
Subscribers can access advanced labs like 3521 and 3531 to deepen their understanding of DNS troubleshooting. These labs provide hands-on experience with real-world DNS issues, such as diagnosing delegation failures and addressing server response errors. Students can work on problems like misconfigured DNS records, unreachable name servers, and other common DNS errors.
