Configuring DNS Services in Universal DDI (2573)
Scenario
You have just deployed two NIOS-X servers, oph1 and oph2. You need to enable and configure DNS services on these servers so you may use them to perform DNS lookups for external domain names, such as training.infoblox.com. For security considerations, only clients from the internal subnets can perform recursive DNS lookups.
Estimated Completion Time
20 to 30 minutes
Prerequisites
Administrative access to the Infoblox Portal
Tasks
Creating DNS service instances for NIOS-X servers oph1 and oph2.
Configuring DNS hostnames for each service instance.
Creating a Named ACL that contains internal networks.
Creating a DNS Config Profile with recursion enabled and associating the Named ACL with the profile.
Associating the DNS Config Profile with the DNS service instances.
Verifying recursive DNS resolution on a client.
Task 1: Creating DNS service instances
Service instances provide service-to-server mapping. We can use our two online NIOS-X servers as DNS name servers for our clients. Create two DNS Service Instances for each of our NIOS-X servers oph1.techblue.net and oph2.techblue.net. Name the Service Instances Techblue DNS service 1 and Techblue DNS service 2.
Task 2: Configuring DNS hostnames for each service instance
Our new DNS service instances need resolvable names. Use oph1.techblue.net and oph2.techblue.net for the respective service instances.
Task 3: Creating a Named ACL
We only want to allow trust subnets to use our DNS services. Create a Named ACL Training Subnets. We will use this profile later to restrict recursion:
Table 2573-1
Type | Value | Permission |
|---|---|---|
IPv4 Network | 172.31.0.0/16 | Allow |
IPv4 Network | 10.100.0.0/24 | Allow |
IPv4 Network | 10.200.0.0/24 | Allow |
IPv4 Network | 10.35.22.0/24 | Allow |
Task 4: Creating a DNS Config Profile with recursion enabled
DNS Config Profile controls DNS service settings such as recursion. Create a profile called Techblue NYC Branch and configure it to allow recursion from the subnets we specified in the Named ACL Training Subnets.
Task 5: Associating the DNS Config Profile with the DNS service instances
Associate the DNS Config Profile to the DNS service instances so the DNS servers will apply the access control list and recursion settings.
Task 6: Verifying recursive DNS resolution on clients
Use the virtual machine testing-linux to verify that the DNS resolution works as intended. Use the command sudo set-network-static-bloxone to set the IP address on the virtual machine and to allow a route to the DNS servers. Look up names on the Internet, such as training.infoblox.com.
Solutions
Task 1 Solution: Creating DNS service instances
Log in to your lab’s jump-desktop.
Use your Education Infoblox Portal Credentials to log into the Infoblox Portal.
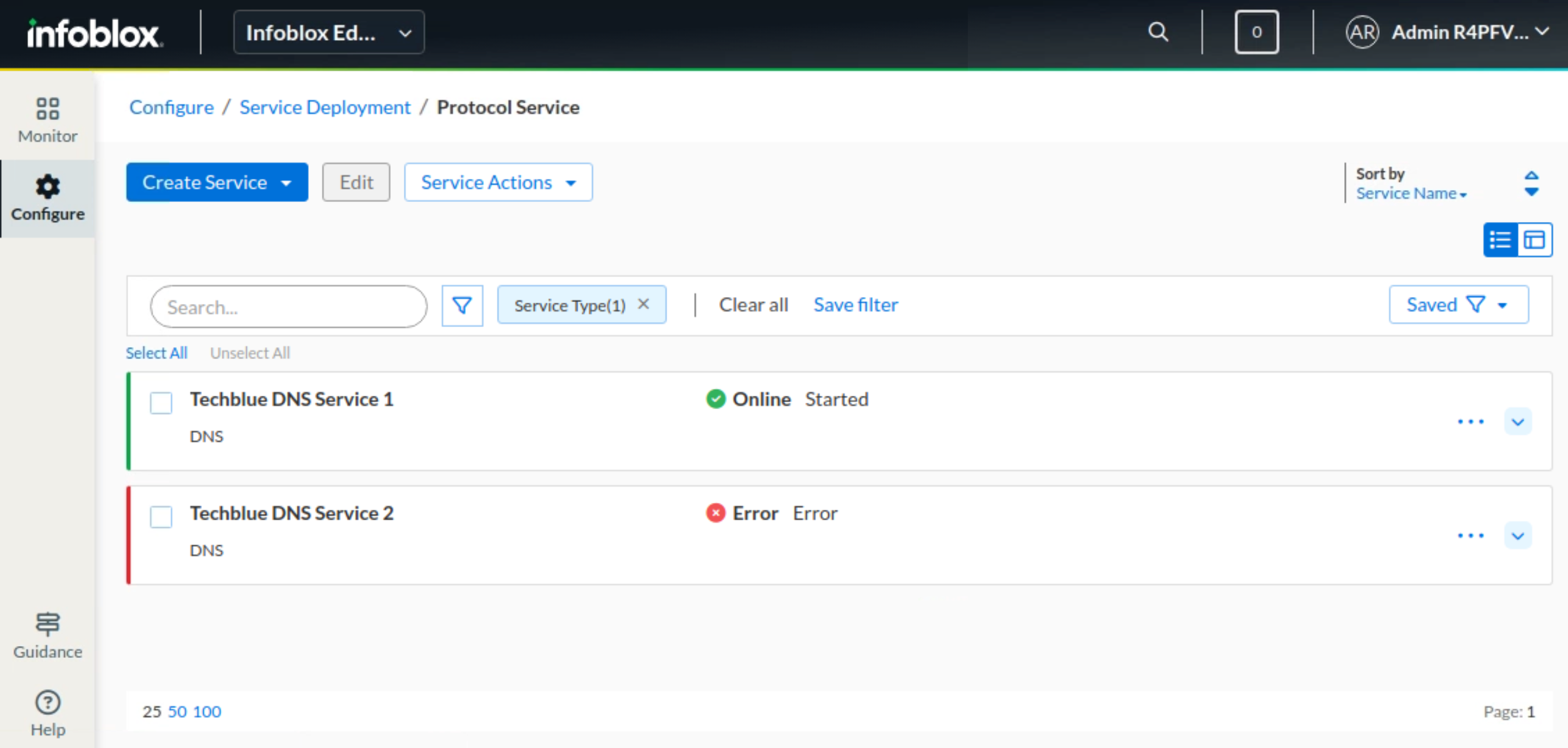
Navigate to Configure → Service Deployment → Protocol Services.
Click on Create Service and choose DNS from the drop-down menu. This opens the Create DNS Service dialog window.
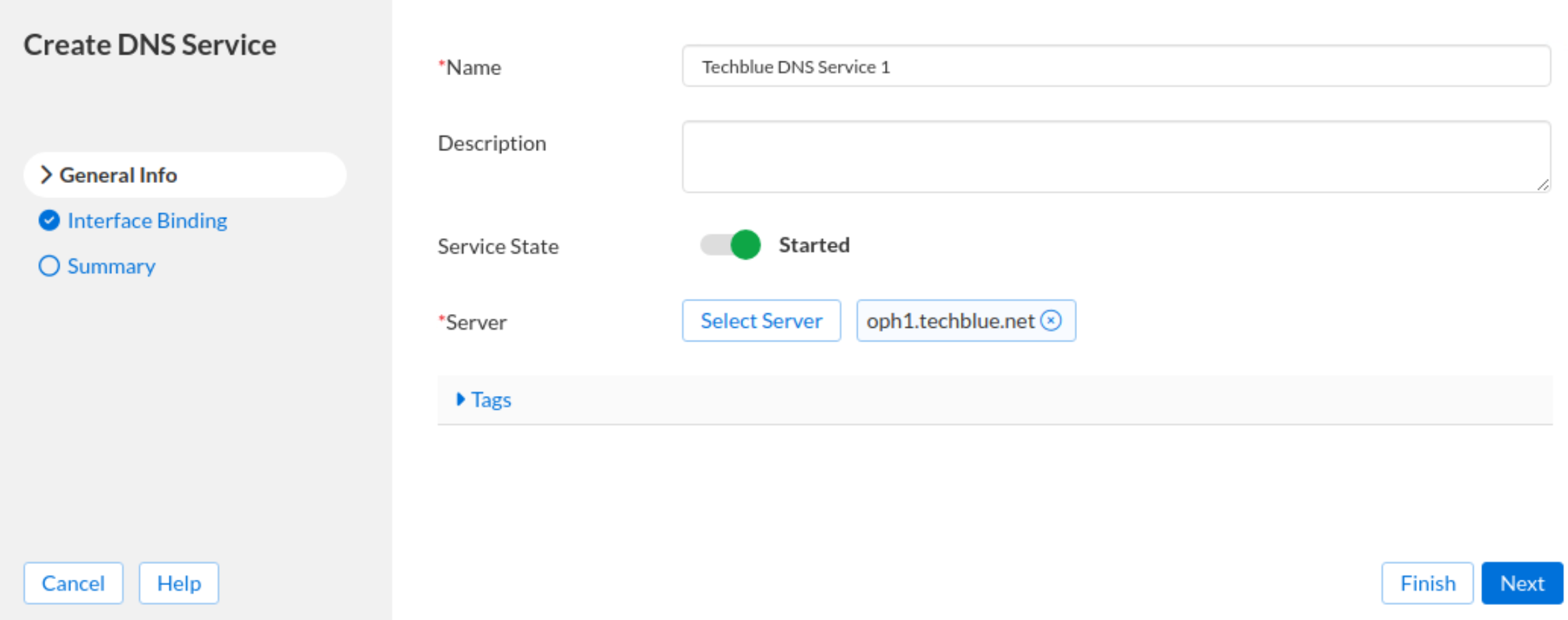
For the Name field, enter Techblue DNS Service 1.
Click Select Server and choose oph1.techblue.net. Click the Select button.
In the Create DNS Service dialog window, click Finish.
Review the setting and click Save & Close.
Repeat steps 4 to 8 to add another service instance named Techblue DNS Service 2 for the server oph2.techblue.net.
The services take a few minutes to start the first time. Do not be alarmed if you see the Error state. Refresh the page after a few minutes, and you should see the servers online and services started.
Task 2 Solution: Configuring DNS hostnames for each service instance
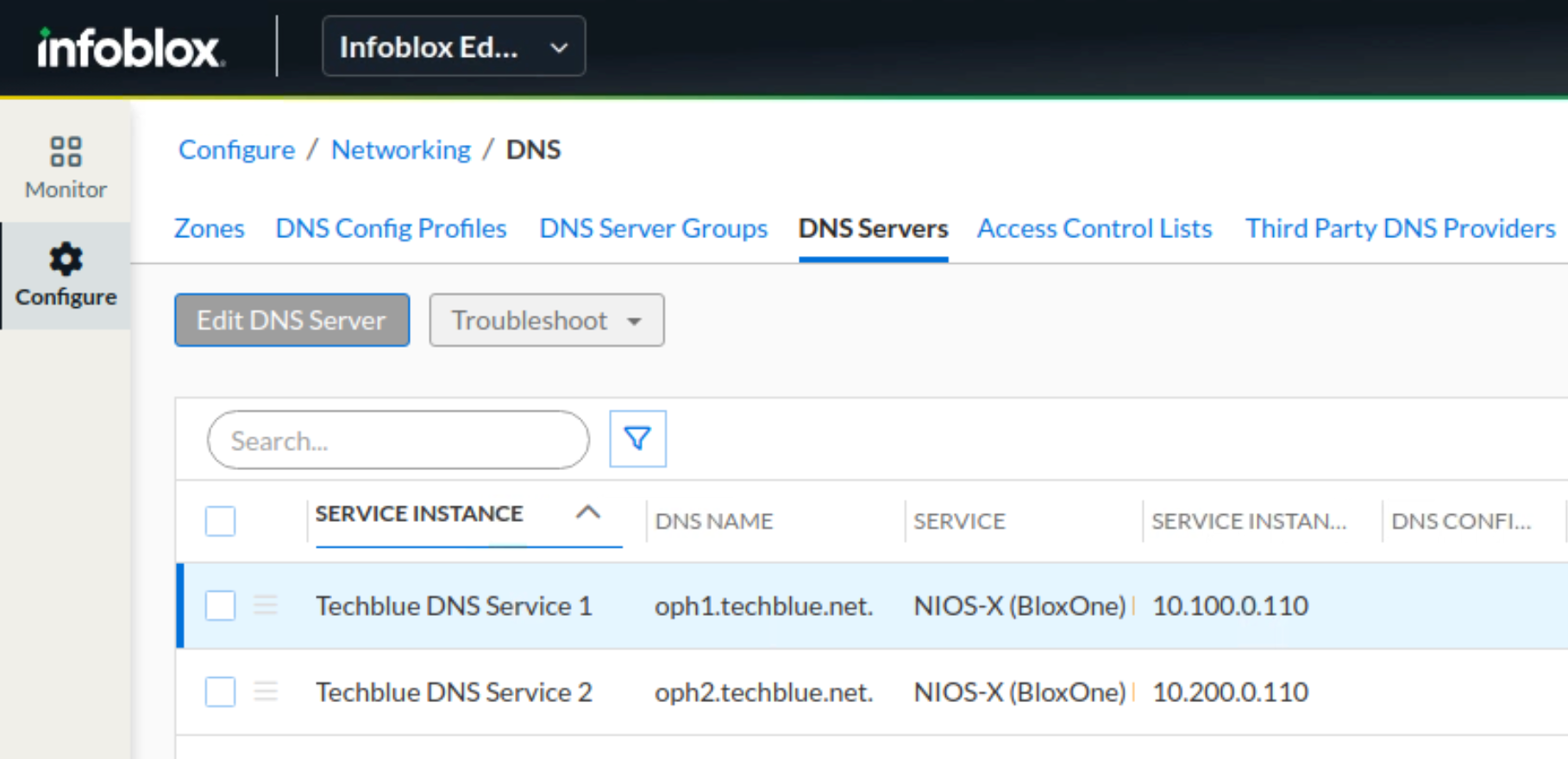
In the Infoblox Portal, navigate to Configure → Networking → DNS. Select the DNS Servers horizontal tab.
Click the menu (hamburger icon) next to the service instance and click Edit.
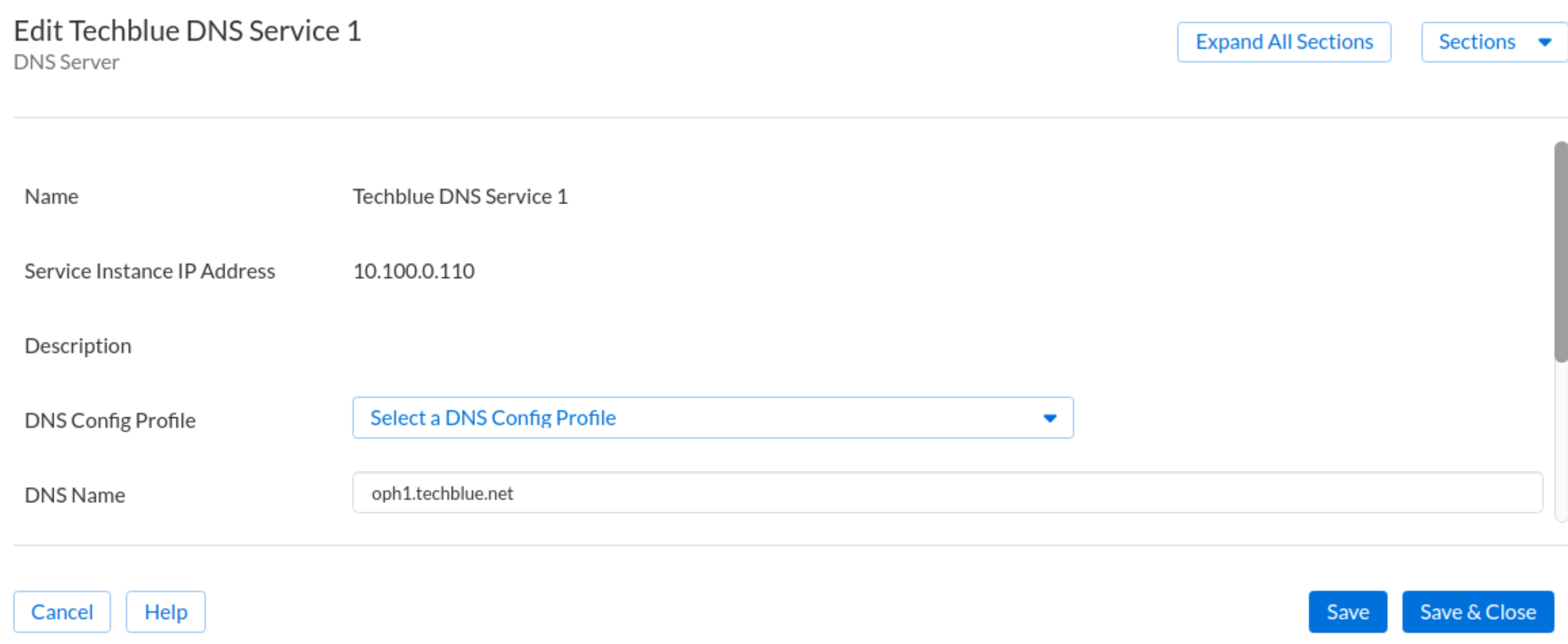
Edit Techblue DNS Service 1 so its DNS Name is oph1.techblue.net.
Edit Techblue DNS Service 2 so its DNS Name is oph2.techblue.net.
Click Save & Close. The screenshot below shows both service instances with names updated.
Task 3 Solution: Creating a Named ACL
In the Infoblox Portal, navigate to Configure → Networking → DNS. Select the Access Control Lists horizontal tab.
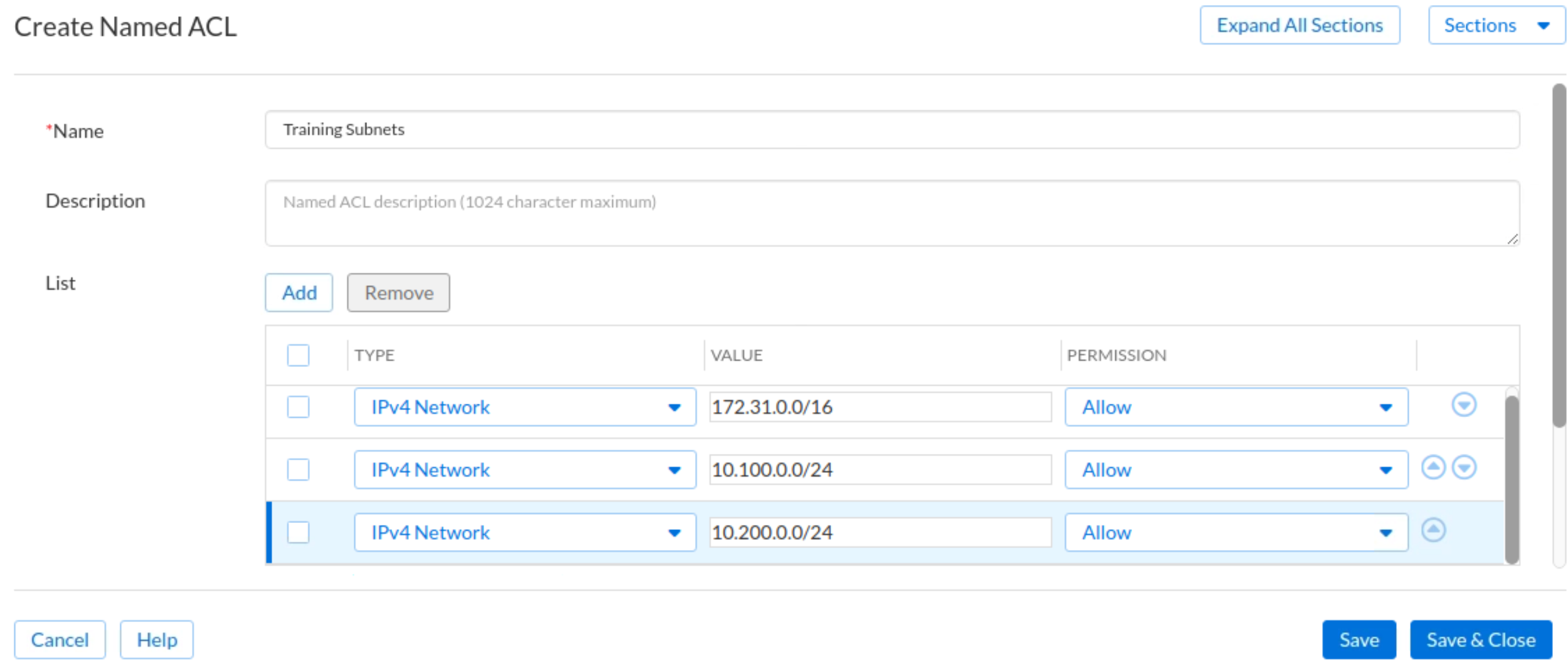
Click Create Named ACL. This brings up the Create Named ACL dialog window.
Set the name to Training Subnets.
In the List section:
Click Add and set a Type of IPv4 Network, Value 172.31.0.0/16, and Permission Allow.
Click Add and set a Type of IPv4 Network, Value 10.100.0.0/24, and Permission Allow.
Click Add and set a Type of IPv4 Network, Value 10.200.0.0/24, and Permission Allow.
Click Add and set a Type of IPv4 Network, Value 10.35.22.0/24, and Permission Allow.
Review the settings and click Save & Close.
Task 4 Solution: Creating a DNS Config Profile with recursion enabled
In the Infoblox Portal, navigate to Configure → Networking → DNS. Select the DNS Config Profiles horizontal tab.
Click Create DNS Config Profile. This brings up the Create DNS Config Profile dialog window.
Set the profile name to Techblue NYC Branch.
Expand the Queries tab and scroll down to Allow Queries From section. Slide the Override bar. Click Add. Add an entry of Type Named ACL and Value Training Subnets. (This is what you configured in Task 3)
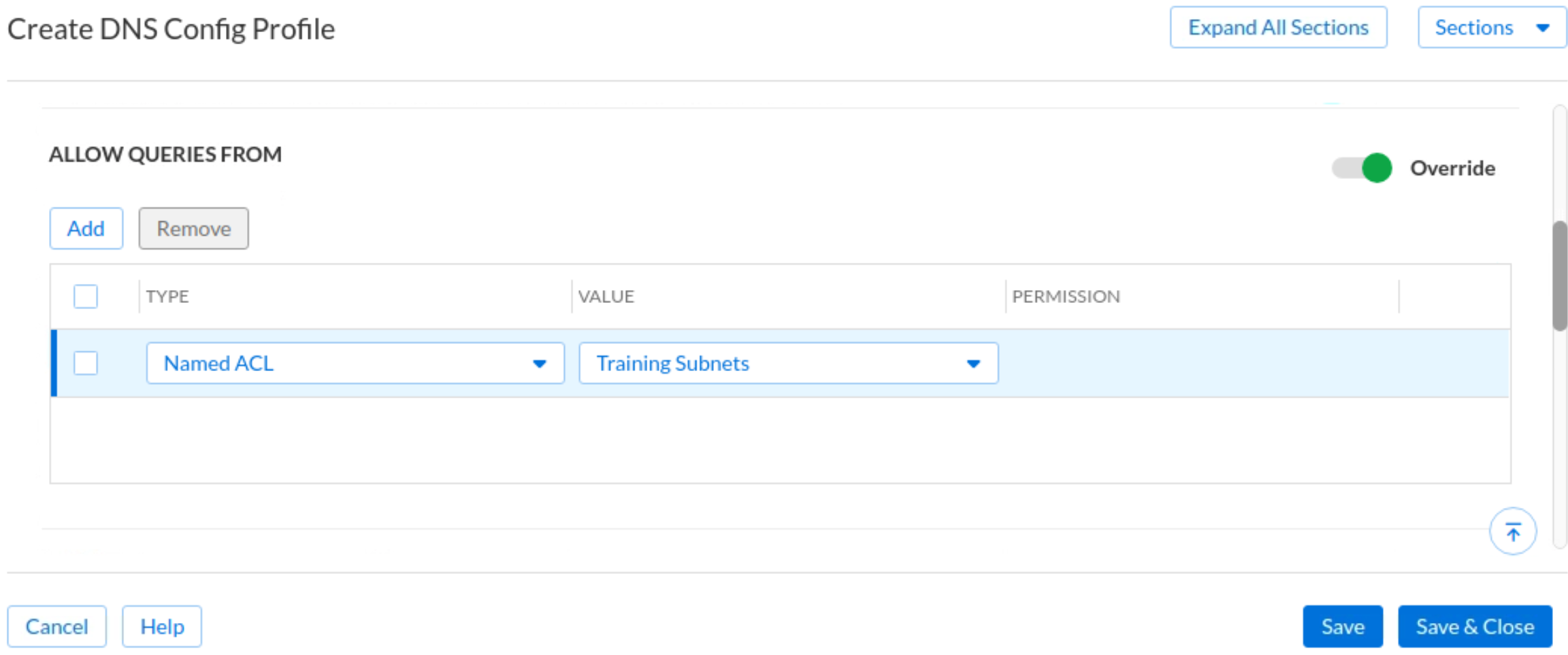
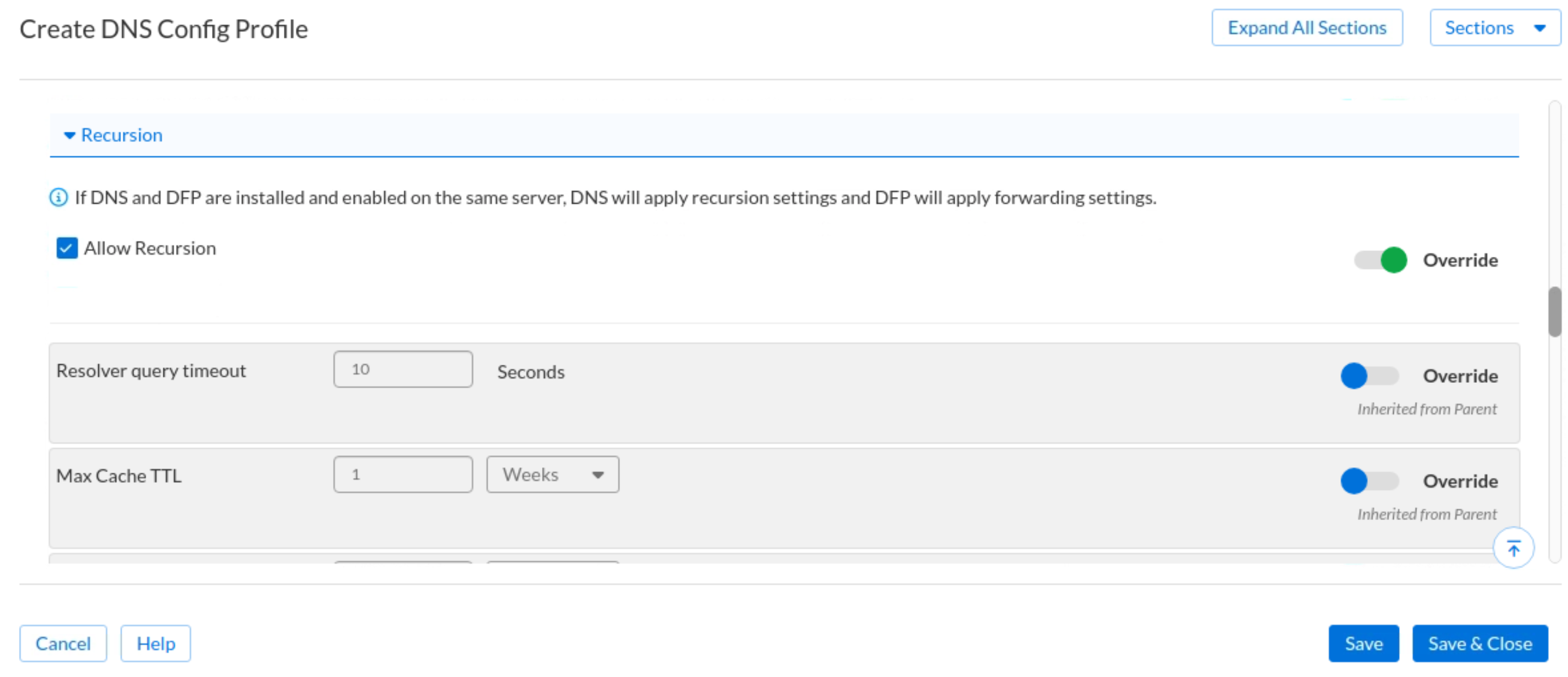
Scroll down and expand the Recursion section. Slide the Override bar and check the box for Allow Recursion.
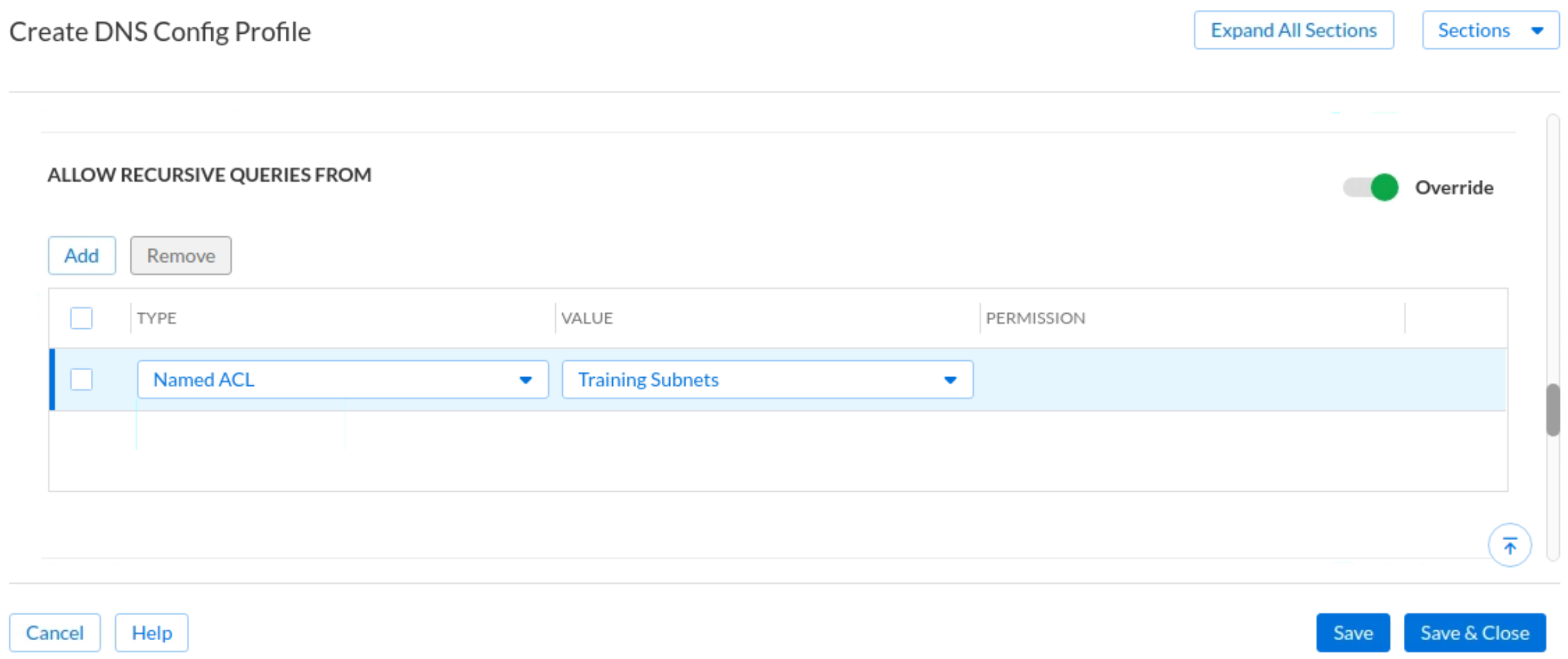
Scroll down to the section Allow Recursive Queries From. Slide the Override bar and click Add. Add an entry of Type Named ACL and Value Training Subnets. (This is what you configured in Task 3)
Click Save & Close.
Task 5 Solution: Associating the DNS Config Profile with the DNS service instances
While still in the DNS Config Profile screen, click on the menu icon next to the profile we just created (TechBlue NYC Branch) and select Edit.
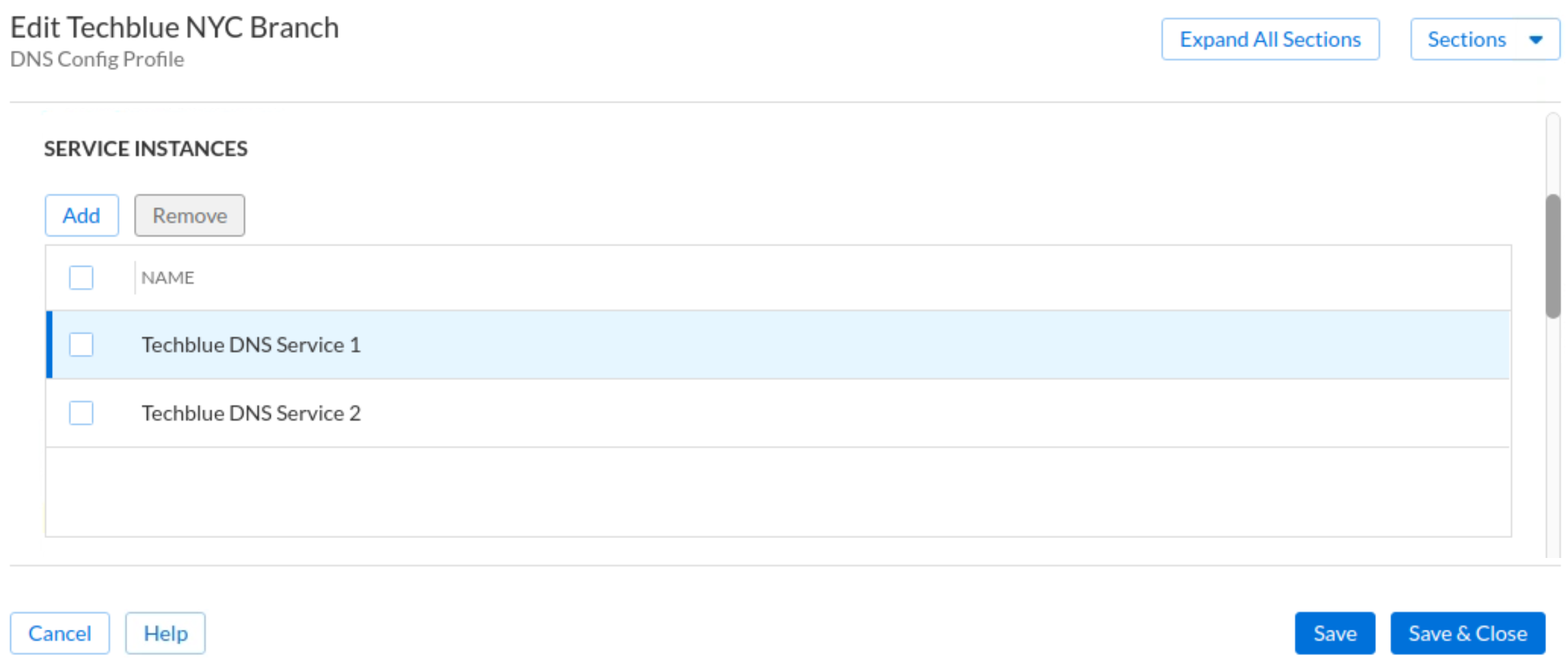
In the section Service Instances:
Click Add. Choose Techblue DNS Service 1 and click Select.
Click Add. Choose Techblue DNS Service 2 and click Select.
Review the settings and click Save & Close.
Task 6 Solution: Verifying recursive DNS resolution on clients
Switch to the virtual machine testing-linux. Open a Terminal window.
Use the command
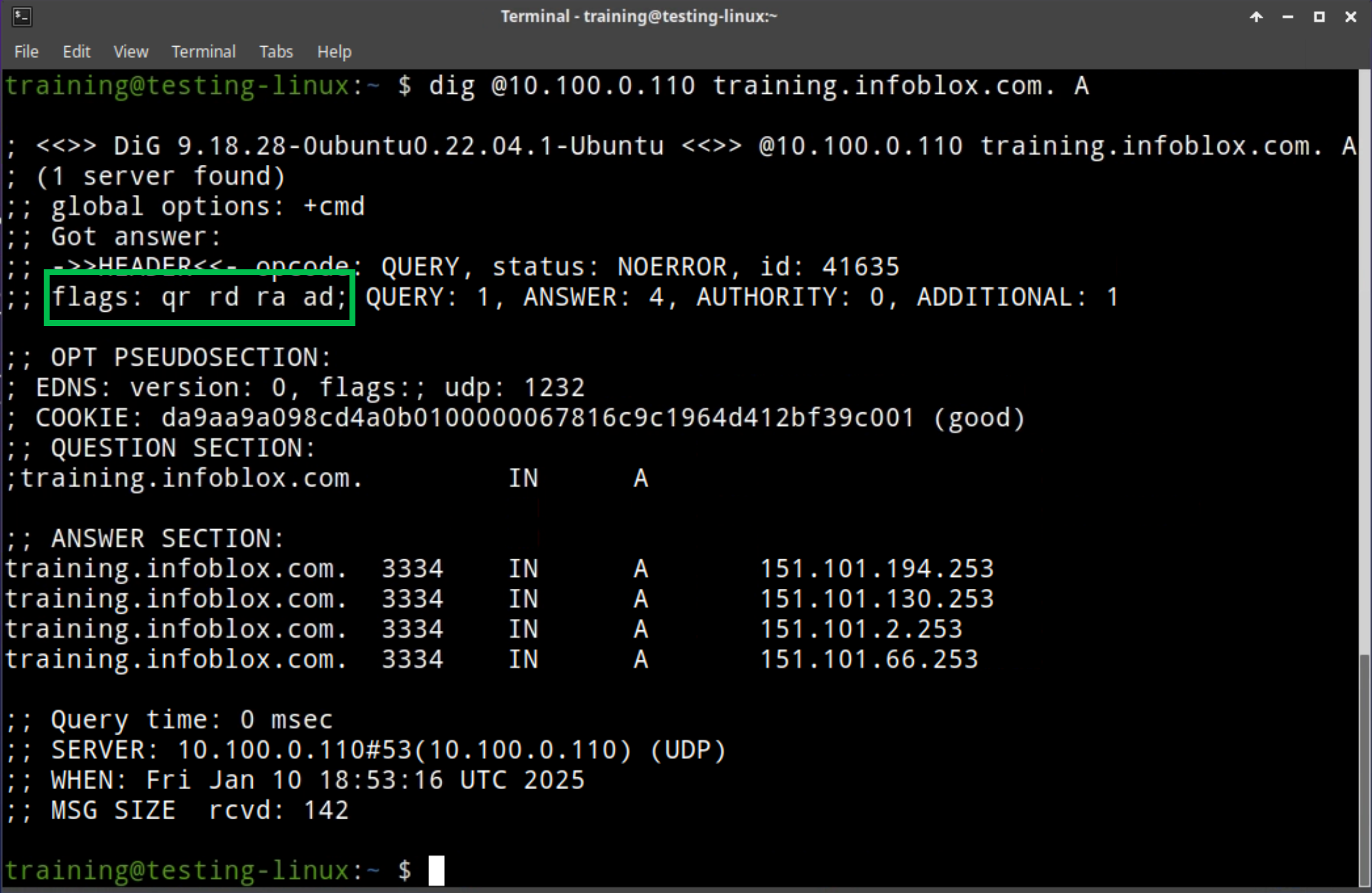
sudo set-network-static-bloxoneto configure the machine with a static IP address. This removes DHCP from our test.Use the following dig commands to query oph1 and oph2:
dig @10.100.0.110 training.infoblox.com. Adig @10.200.0.110 training.infoblox.com. A
Examine the results. If we see ra in the flags section of the output, we can verify that the answers are obtained via recursion.