Adding Endpoint Groups to Security Policies (2815)
Scenario
Following the successful deployment of Infoblox Endpoint agents on company-managed devices, your organization is now extending Threat Defense policies to these roaming endpoints. This ensures consistent security enforcement across all user devices, regardless of location.
You are tasked with the following:
Add the Endpoint Group named Techblue Endpoints as a Network Scope in the existing security policy:
Policy Name: Techblue Sec Policy
Verify the configuration by performing domain lookups from a device within the Techblue Endpoints group to ensure the policy is applied correctly.
Estimated Completion Time
20 to 30 minutes
Prerequisites
Administrative access to the Infoblox Portal
Tasks
Adding an Endpoint Group to a Security Policy
Testing Security Policies against Techblue Endpoints Group
Task 1: Adding an Endpoint Group to a Security Policy
In the Infoblox Portal, add the Techblue Endpoints Endpoint Group to the Techblue Sec Policy as a Network Scope.
Task 2: Testing Security Policies against Techblue Endpoints Group
In testing-windows open the Tools folder on the Desktop and run the interface-static-internet.bat file as an administrator. This sets a static IP address for the VM. Please re-enter the command if the VM does not get an IP address the first time.
In the lab environment, use the testing-windows VM and its web browser to navigate to some websites and verify that security policies are working as intended. www.infoblox.com should be allowed, while sites such as eicar.pw, eicar.steam, and eicar.host should be blocked. Access several websites and verify that the category and application filters are working. Finally, look at the Security Activities under the Reports section to confirm that Threat Defense logged these queries.
Solutions
Task 1 Solution: Adding an Endpoint Group to a Security Policy
In this task, we will add the Endpoint Group Techblue Endpoints into the security policy Techblue Sec Policy as a Network Scope. This will allow all the rules already configured as part of the policy to apply to traffic handled by the Endpoint Group.
Log into your lab’s VM jump-desktop.
While logged in to jump-desktop, use your Education Infoblox Portal Credentials to log into the Infoblox Portal.
Navigate to Configure → Security → Policies → Security Policies
Select the checkbox to Techblue Sec Policy and click Edit
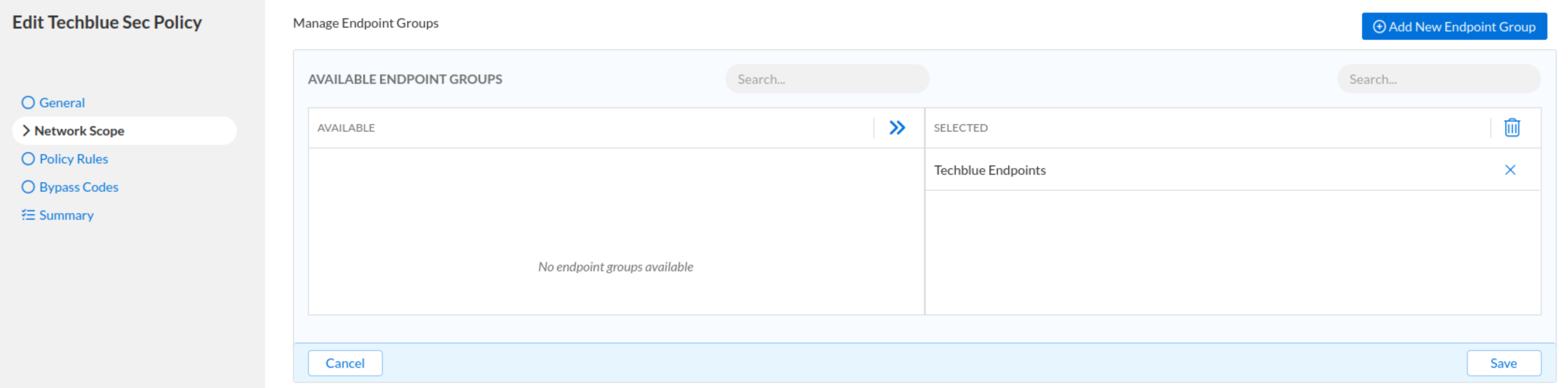
Under the Network Scopes tab:
Click Add Source and choose Endpoint Groups from the list.
Add Techblue-Endpoints and click Save.
Click Finish, then Save&Close.
Task 2 Solution: Testing Security Policies against Techblue Endpoints Group
In this task, we are simulating a remote worker using an insecure internet connection. The Infoblox Endpoint should forward all the client DNS traffic to the Threat Defense Cloud and block any unwanted or harmful traffic based on our Security Policies.
Log into your lab’s Testing-Windows, with the password
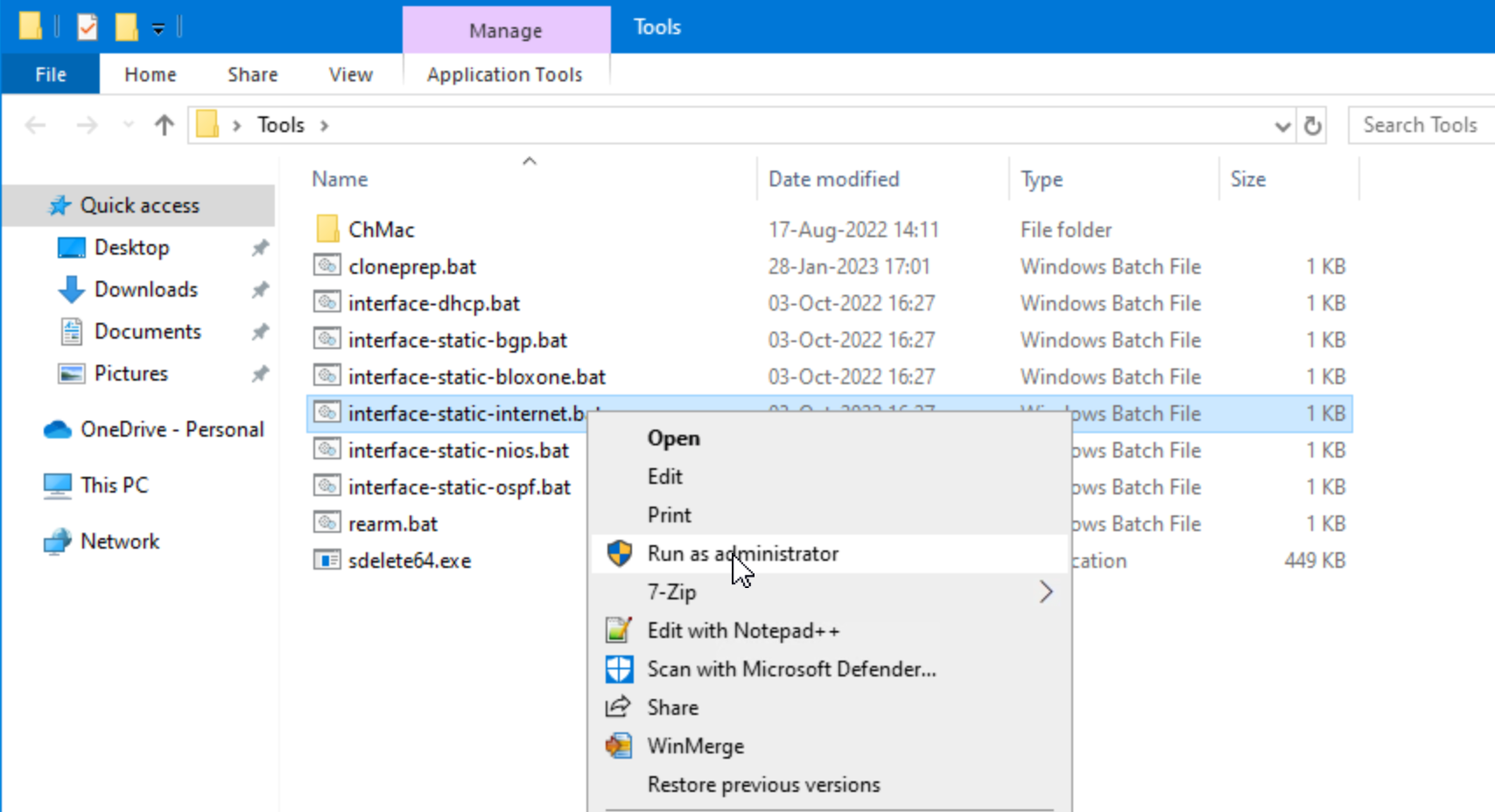
infoblox.Open the Tools folder on the Desktop and run the
interface-static-internet.batfile as an administrator.NOTE: This file is used to set an IP address for the VM in a subnet simulating a direct internet connection.
NOTE: If the machine doesn’t get an IP address, please re-enter the command.
Open a browser window and surf
www.infoblox.com,eicar.pw, eicar.stream and eicar.cowww.infoblox.comshould be allowed, and the Infoblox home page should be visible.
eicar.pw, eicar.stream, andeicar.coshould all be blocked, and the browser should fail to connect to the server.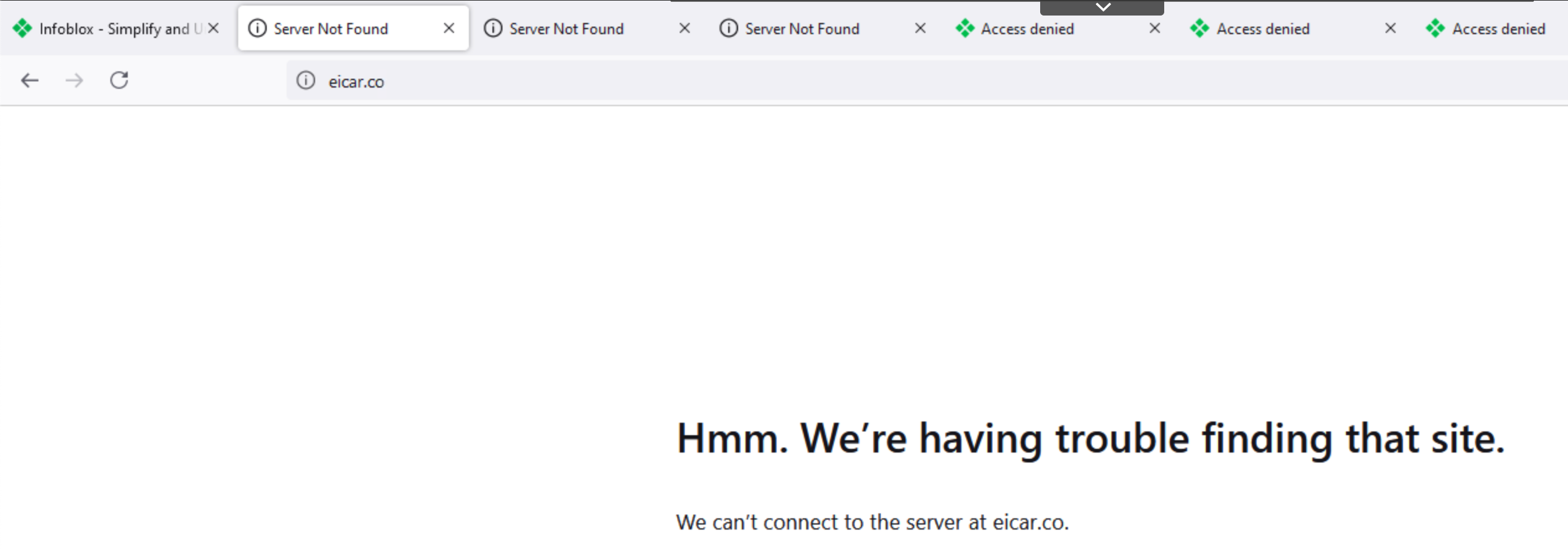
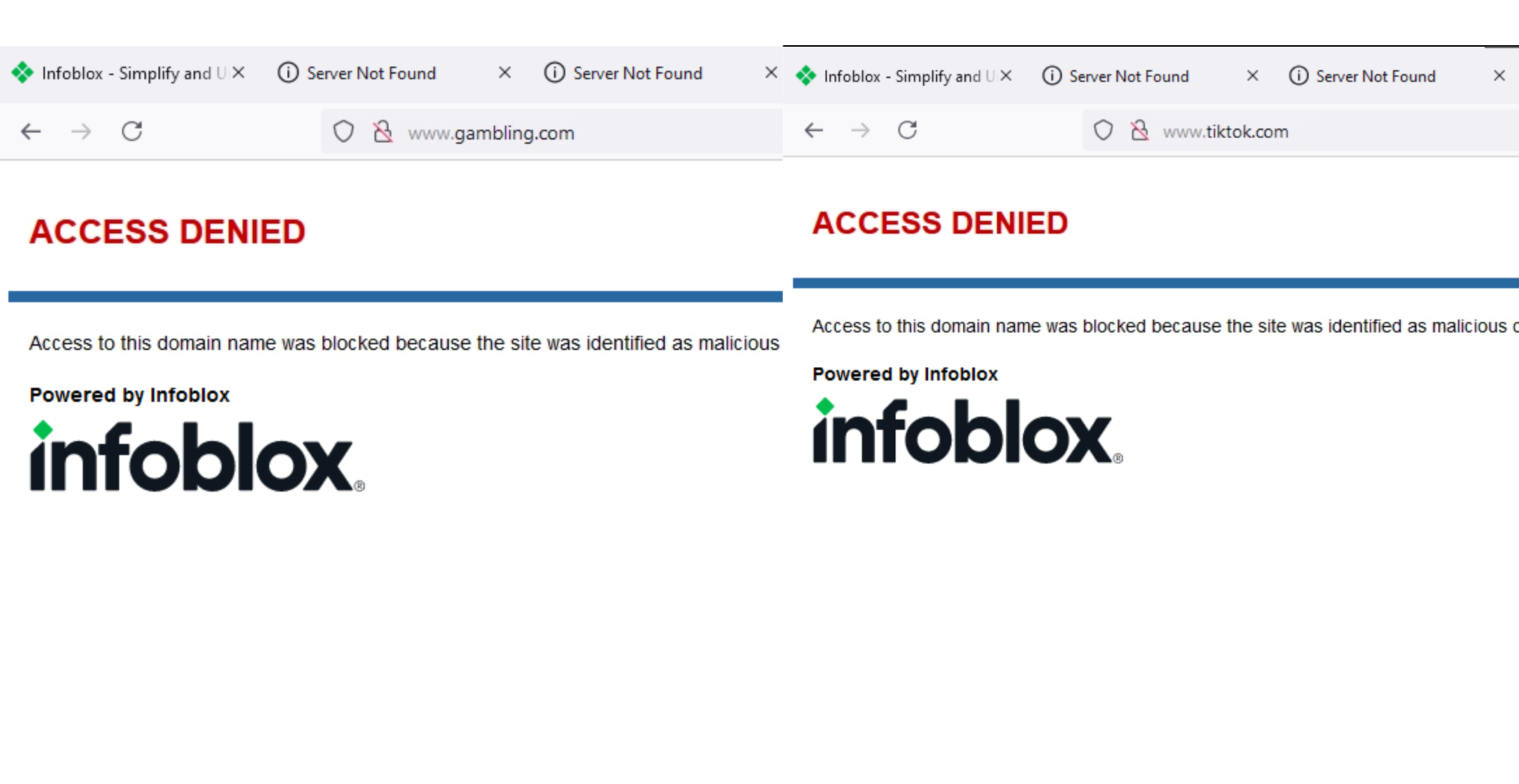
Surf
www.gambling.com,www.instagram.com,andwww.tiktok.comto test Category and Application filters.All three domains should be redirected to the default Infoblox redirect page.
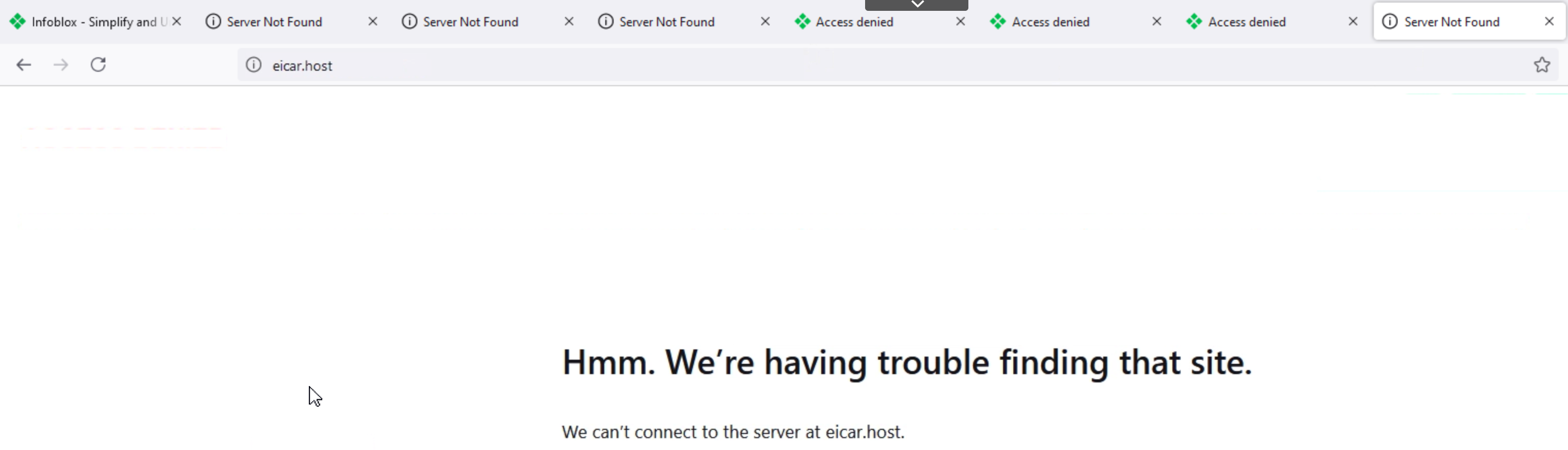
Surf
eicar.hostto test the Infoblox_Base Feed.The domain should be blocked, and the browser should fail to connect to the server.
Log back into your lab’s jump-desktop VM.
Use your Education Infoblox Portal Credentials to log into the Infoblox Portal.
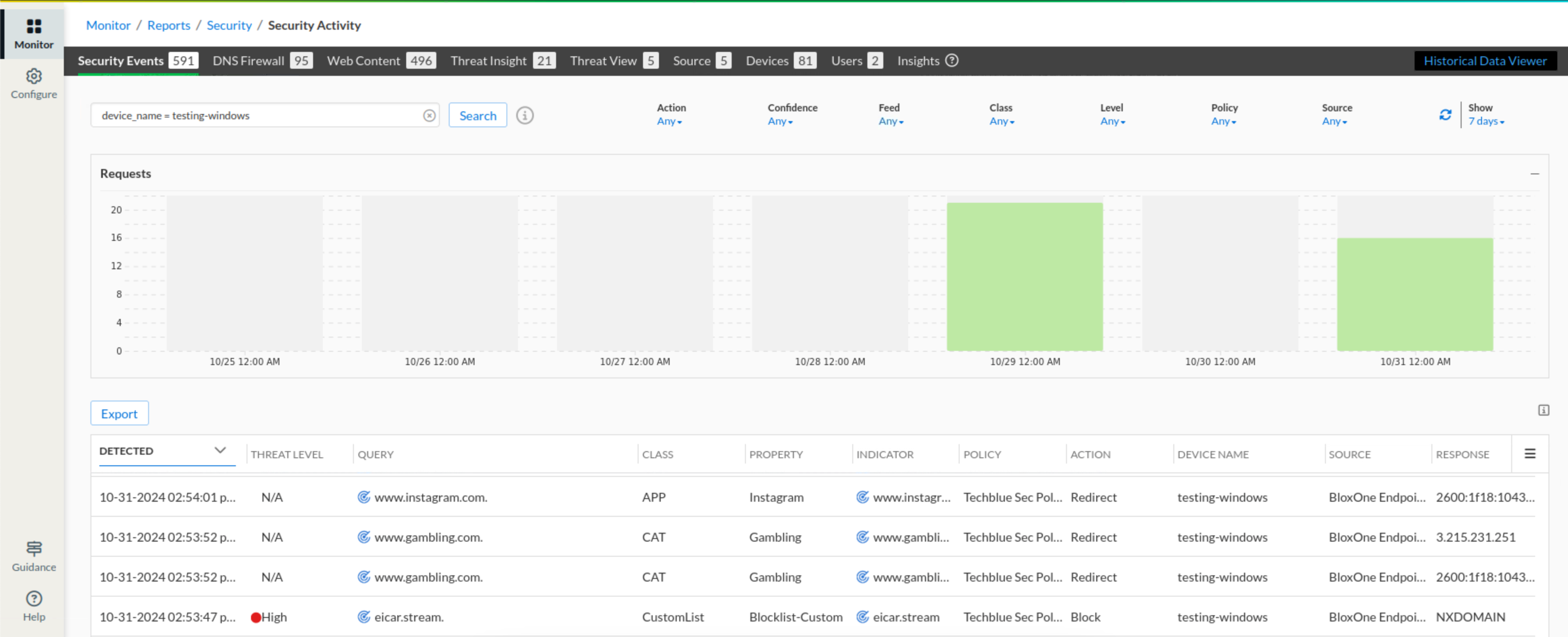
Navigate to Monitor → Reports → Security → Security Activities
Use the search bar at the top of the page and use
device_name = testing-windowsto view all the logs for this specific machine.The domain name will be under the Query field.