Creating a DNS Secondary Zone in Universal DDI (2576)
Scenario
The clients on your network need reliable access to the domain ddip.org, which is owned and operated by a training provider outside your organization. You could set up a forward zone, but local clients cannot resolve names in this domain during a network outage. For local survivability considerations, you decided to set up a secondary zone. You have contacted the administrators of ddip.org to allow zone transfer access. Now you need to complete the setup by creating a secondary zone on the Infoblox Portal and map the zone to your DNS servers.
Estimated Completion Time
20 to 30 minutes
Prerequisites
Administrative access to the Infoblox Portal
Permission to perform zone transfer from external primary DNS server
Learning Content
Tasks
Creating a DNS Server Group
Creating a Secondary Zone ddip.org
Validating the DNS zones and records from a client
Task 1: Creating a DNS Server Group
The administrators of ddip.org have granted zone transfer access by providing a TSIG key. The key is stored in a file named tsig_xfer_sha256.txt, located in the Shared Drive on the jump-desktop VM. They have also provided the IP address of their external primary name server: mimosa.techblue.io (45.120.106.133).
You will create an Authoritative DNS Server Group that includes this external server (mimiosa) and the provided TSIG key. This server group will later be used to configure a secondary zone for ddip.org.
Task 2: Creating a Secondary Zone ddip.org
Use the DNS Server Group created in Task 1 to create a secondary zone for ddip.org in the Infoblox Portal.
Task 3: Validating the DNS zone and records from a client
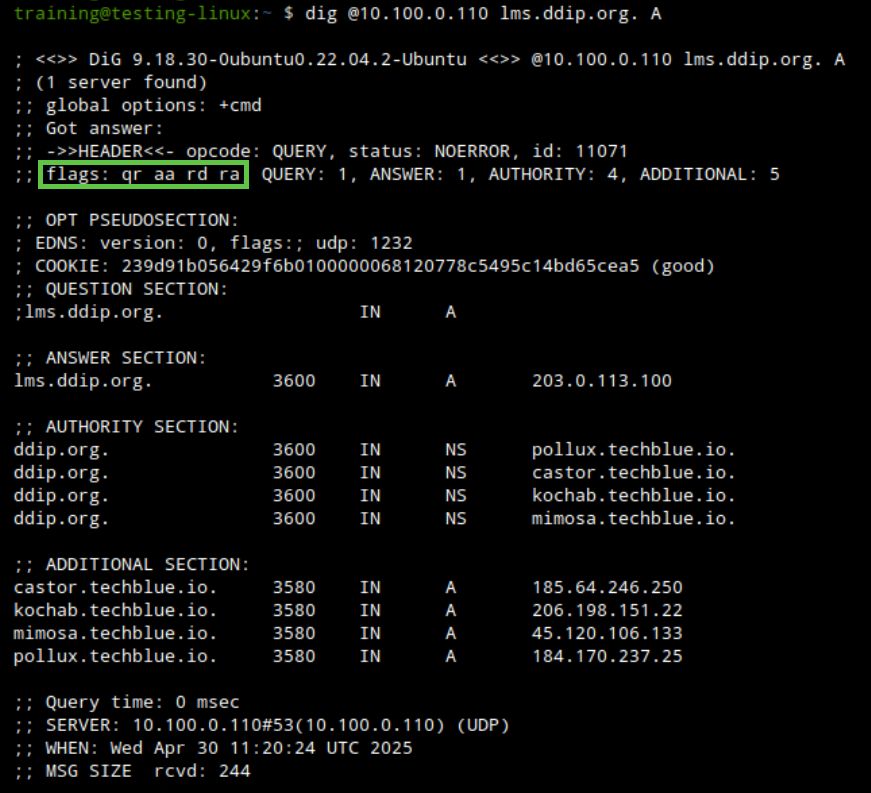
Verify that the zone transfer has completed successfully by confirming that clients can resolve records from the secondary zone. Use the testing-linux virtual machine to check for the A record of lms.ddip.org.
Solutions
Task 1 Solution: Creating a DNS Server Group
Log in to your lab’s jump-desktop
Use your Education Infoblox Portal Credentials to log into the Infoblox Portal
Navigate to Configure → Networking → DNS
Click the DNS Server Groups tab.
Click the Create button and select Authoritative DNS Server Group from the list.
In the Name field, enter:
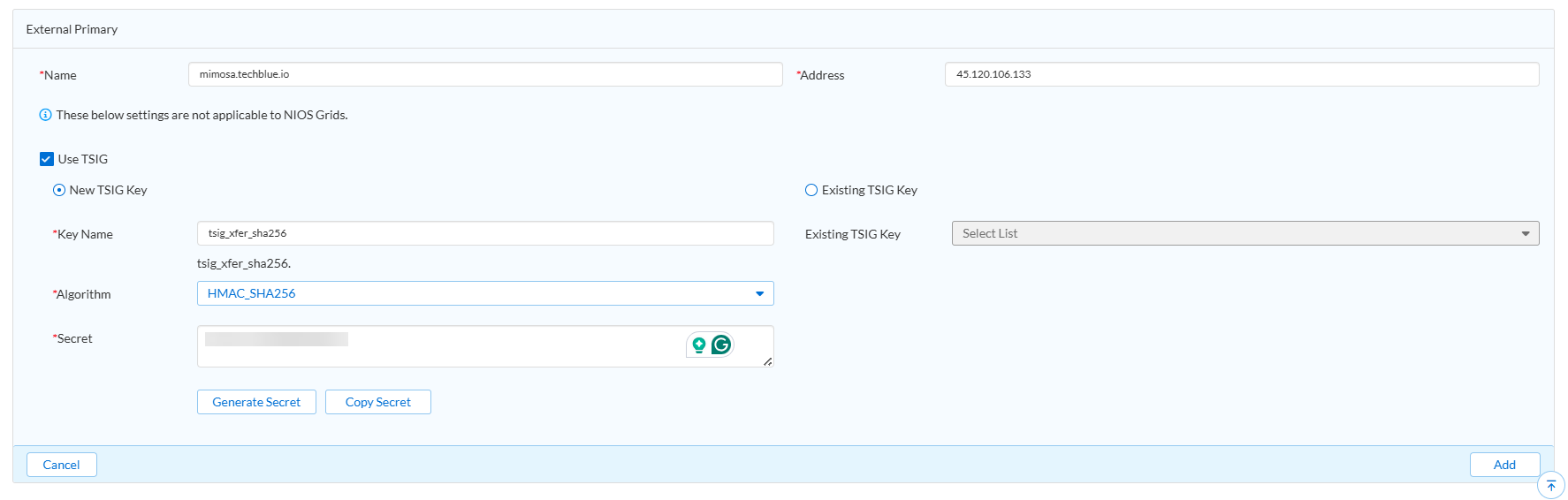
external-ns-group.Under External Primary Servers, click Add and select External Primary.
Enter the following details:
Name:
mimosa.techblue.ioAddress:
45.120.106.133(You can verify this using the commanddig @8.8.8.8 mimosa.techblue.io.in the terminal)
Check the Use TSIG option and select New TSIG Key.
To retrieve the TSIG key details:
On the Jump-Desktop VM, click the Start menu and open the Geany application (text editor).
In Geany, navigate to File → Open, then browse to and open the file:
/mnt/shared/tsig_xfer_sha256.txt
In the New TSIG Key section, fill in the following fields using the values from the file:
Enter the Key Name as shown in the file
Select the Algorithm from the dropdown to match the one listed
Copy and paste the Secret exactly as provided in the file
Click Add
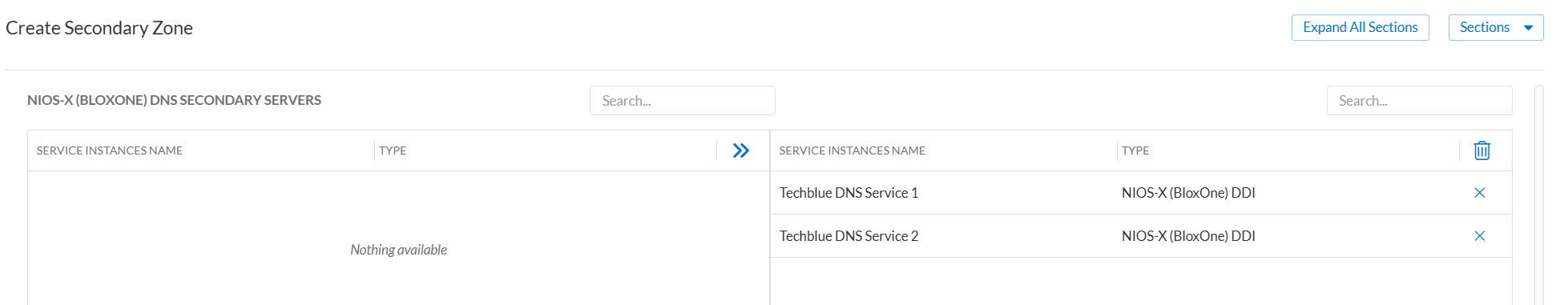
Under NIOS-X BloxOne Secondary DNS Servers, click the arrow next to both of your DNS service instances to move them to the list of Secondary DNS Servers
Click Save & Close
Task 2 Solution: Creating a Secondary Zone ddip.org
Navigate to Configure → Networking → DNS
Select the Zones tab
Click on the DNS view default
Click the Create button and select Secondary Zone from the list. This launches the Create Secondary Zone dialog window
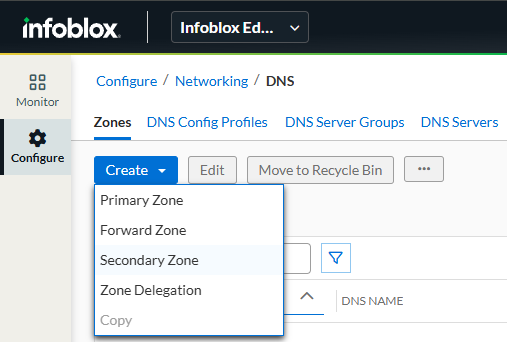
For the Name field, enter
ddip.orgExpand the DNS Server Groups section.
From the Available list, select external-ns-group, and then click the arrow to move it to the Selected column.
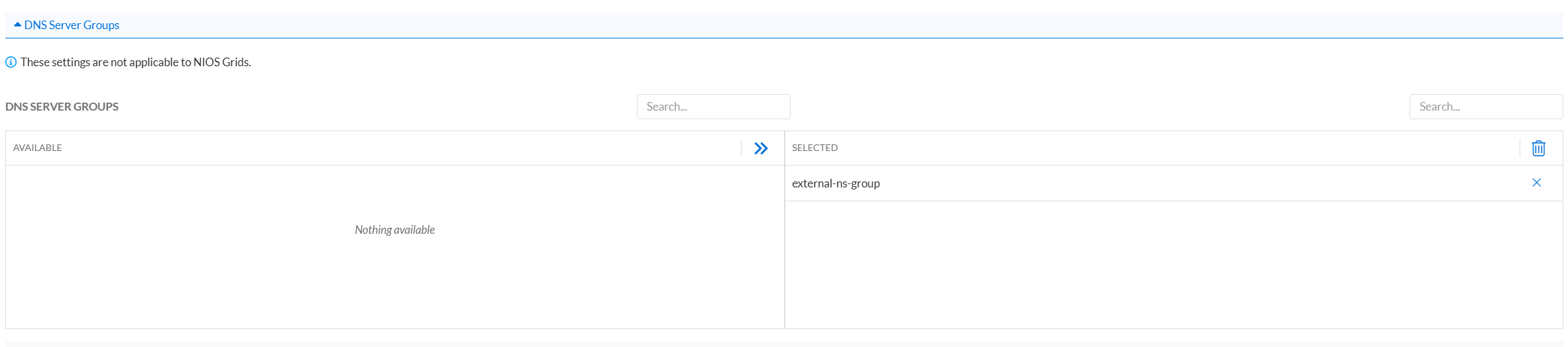
Click Save & Close
Task 3 Solution: Validating the DNS zone and records from a client
On testing-linux VM, open a Terminal window.
Set the IP address as a fixed address with the command
sudo set-network-static-bloxoneto allow a route to the DNS server. If prompted for a password, useinfoblox.Query the NIOS-X DNS server for the secondary zone we just configured with the following command:
dig @10.100.0.110 lms.ddip.org. ACheck the dig response. It should return an Authoritative Answer (aa) with NOERROR. This confirms that the server 10.100.0.110 has a copy of the authoritative zone data.